Trend Micro Password Manager Found to Be Vulnerable to Privilege Escalation Attacks
- Trend Micro Password Manager version 5.0 is found to be plagued by a privilege escalation flaw.
- An attacker could use an unsigned arbitrary DLL to execute code as a privileged user through the app.
- This would result in a complete Windows system takeover with incredibly serious consequences.
If you are using the Trend Micro Password Manager v5.0 standalone, or the one that is part of the consumer version of the Trend Micro Security 2019 v15.0 product, you should update to the latest version immediately and apply the patch that came out two weeks ago. This patch fixes two severe vulnerabilities that were given the identifiers CVE-2019-14684 and CVE-2019-14687, and which concern DLL hijacking flaws that allow an attacker to load an arbitrary and unsigned DLL into the signed service’s process, escalating their privileges to the highest level. The attack would require physical access to the target machine to work, and Trend Micro states that there have been no known incidents of exploitation so far.
The discovery of CVE-2019-14684, the most severe of the two, was the work of the SafeBreach security researcher Peleg Hadar, who reported it to Trend Micro on July 23, 2019. The anti-virus vendor responded almost immediately and fixed the issue in just a week. Yesterday, the company published a security bulletin, and SafeBreach published the details of the vulnerability, demonstrating the PoC (proof of concept) and explaining the potential for malicious uses and their corresponding impact.
image source: https://safebreach.com
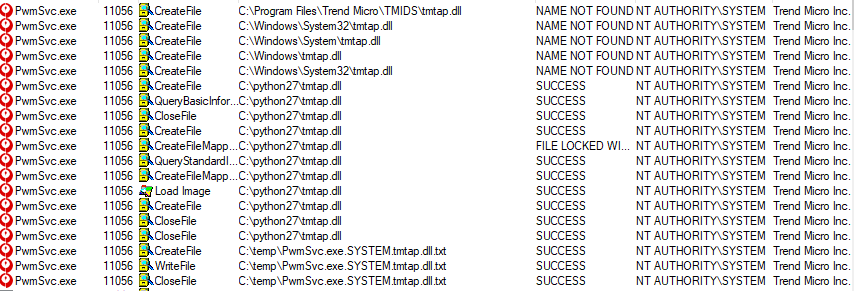
As the researcher explains, the main way to perform a catastrophic attack would be to bypass the app’s whitelisting system and execute code with “NT Authority/System” privileges. This service autostarts with the OS boot, so it adds to the persistence of the attack. Trend Micro’s password manager is executed at the “NT Authority/System” level, loading a library called “tmwlutil.dll” upon execution. This library is loaded from a specified python directory, but this can be modified together with the username who executed it, the name of the DLL file, and the name of the process that’s loading it.
A regular user could use an arbitrary DLL as a means to perform the code execution with the privileges of an authenticated user, thanks to the uncontrolled search path for the loading of the DLL, and the absence of certificate validation that allows the deployment of an unsigned DLL. The requirement is to modify the system to include a new PATH variable to include the desired directory where the malicious DLL lies. By operating at the “NT Authority/System” level, an attacker becomes the most privileged user in a Windows system, so they can access any file or process, modify them, etc.
Are you using Trend Micro’s Password Manager, or do you prefer a different product? Let us know which one in the comments section below, or on our social media, on Facebook and Twitter.