When you purchase through links on our site, we may earn an affiliate commission. Here’s how it works.
Tor vs. VPN: Which One Is Right for You?
Our experts have reviewed 53 VPN providers, which were put through extensive rounds of testing. To learn more about that process, here’s how we review VPNs, where we explain our criteria and our policy of being fully transparent.
When reading online about digital privacy, you'll often encounter terms such as "Tor" and "VPN," most often in relation to encryption and ensuring no one follows you online. Still, just like other hardware and software technologies, there's no one-size-fits-all solution. With that said, we'll use this Tor vs. VPN comparison to explain the similarities and differences between the two.
In short, Tor is designed to protect your anonymity. Differently said, it hides who you are. VPNs are designed for privacy, hiding what you do on the Web. As you can see, those 2 concepts are very similar, even though Tor and VPNs are vastly different at their core.
What's crucial to mention is that both Tor and VPNs have proven to be excellent choices for online privacy. However, each has its pros and cons, which are essential to consider before using them.
So, join us as we explore the similarities and differences between Tor and VPN services.
What is Tor?
Tor is a network consisting of a large number of computers (nodes) run by volunteers from across the world, designed to encrypt your data and provide anonymity.
At its core, Tor is a software solution. It’s a free program (called "Tor Browser," maintained by a non-profit organization "The Tor Project") that you can download on your computer, phone, or tablet. That's a special Web browser designed to route your Web traffic in a very specific way, stripping away any data that points back to you.
The name Tor is actually short for 'The Onion Router,' which refers to the special type of network routing technology that Tor is built on.
Onion routing is a networking method developed in the 90s by naval researchers. 'Routing' refers to how data packets are sent from your Internet devices to their final destination. Since the Internet does not have a central hub, packets can take just about any path.
Routing is just the method of ensuring the right packets make it to the right place. Usually, those packets can be inspected and read by the computers at all the stops on the way to the destination server (there are around 7,000 relays in the Tor network).
Onion routing wraps the original data in layers of encryption. Each stop on the way to the end-point strips away a single layer of encryption until the final server removes the last 'onion layer' and then passes on.
Tor goes far beyond that since it randomly selects which stops on the Tor network will carry a given piece of data. Each computer on the network only knows which node the packet comes from and which node it’s going to.
How Does Tor Work?
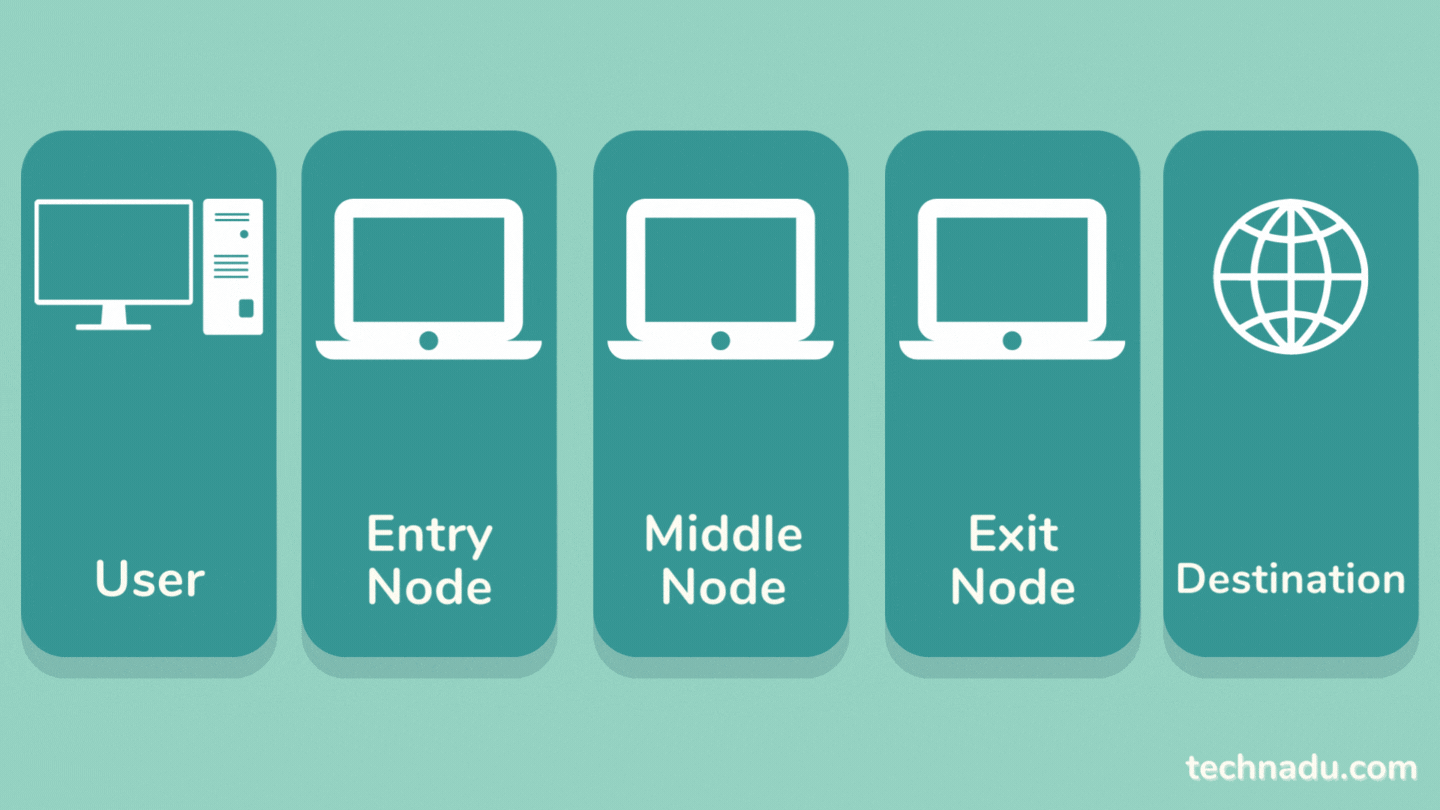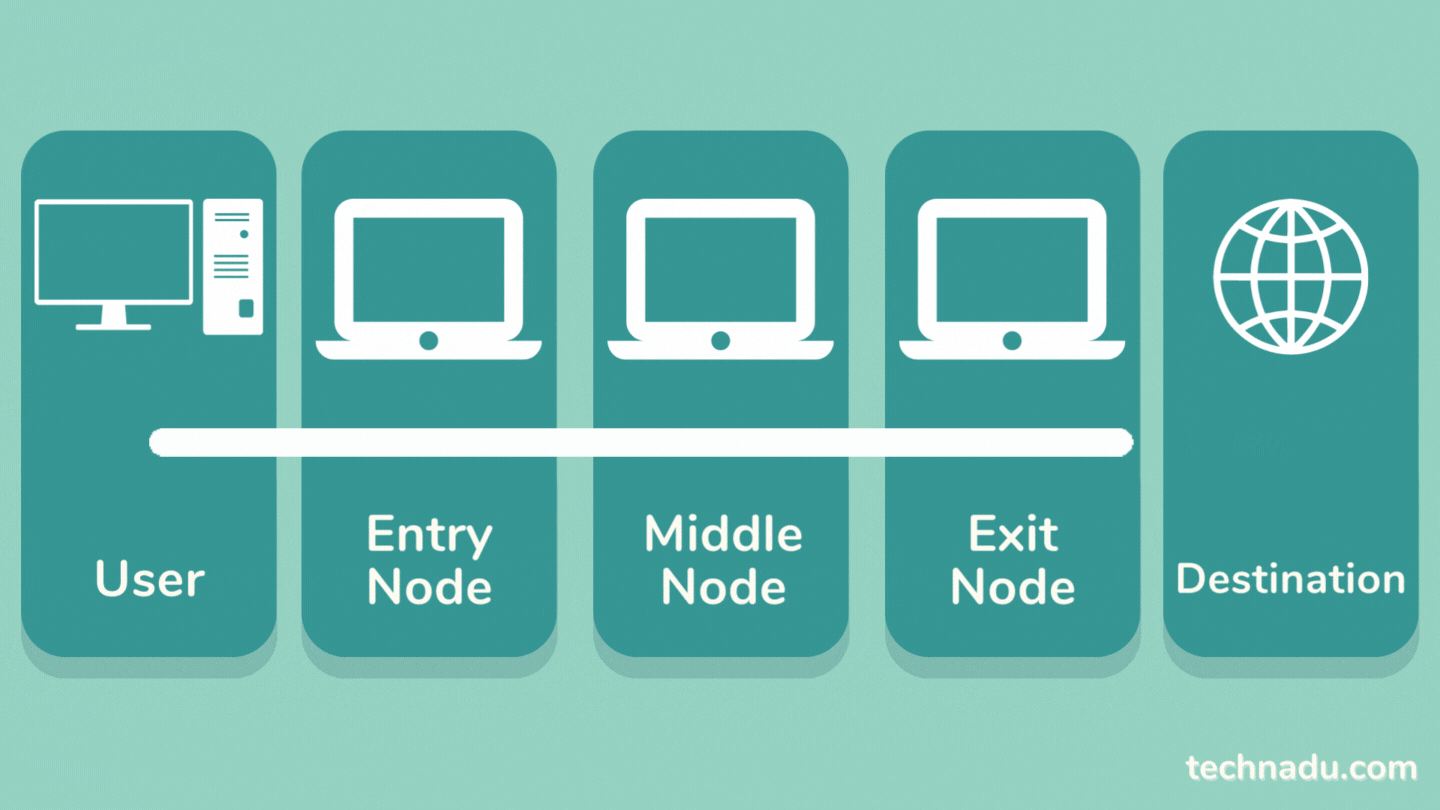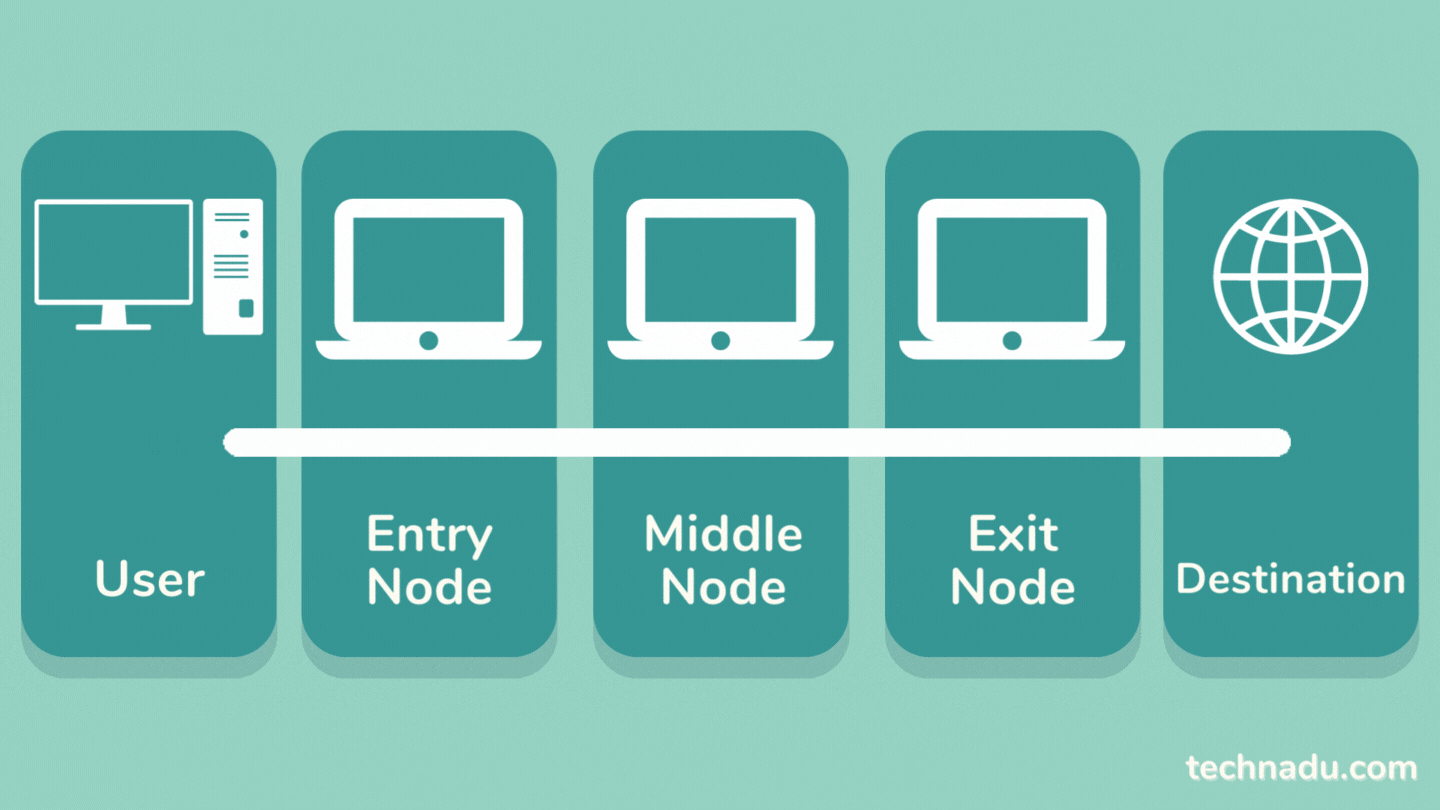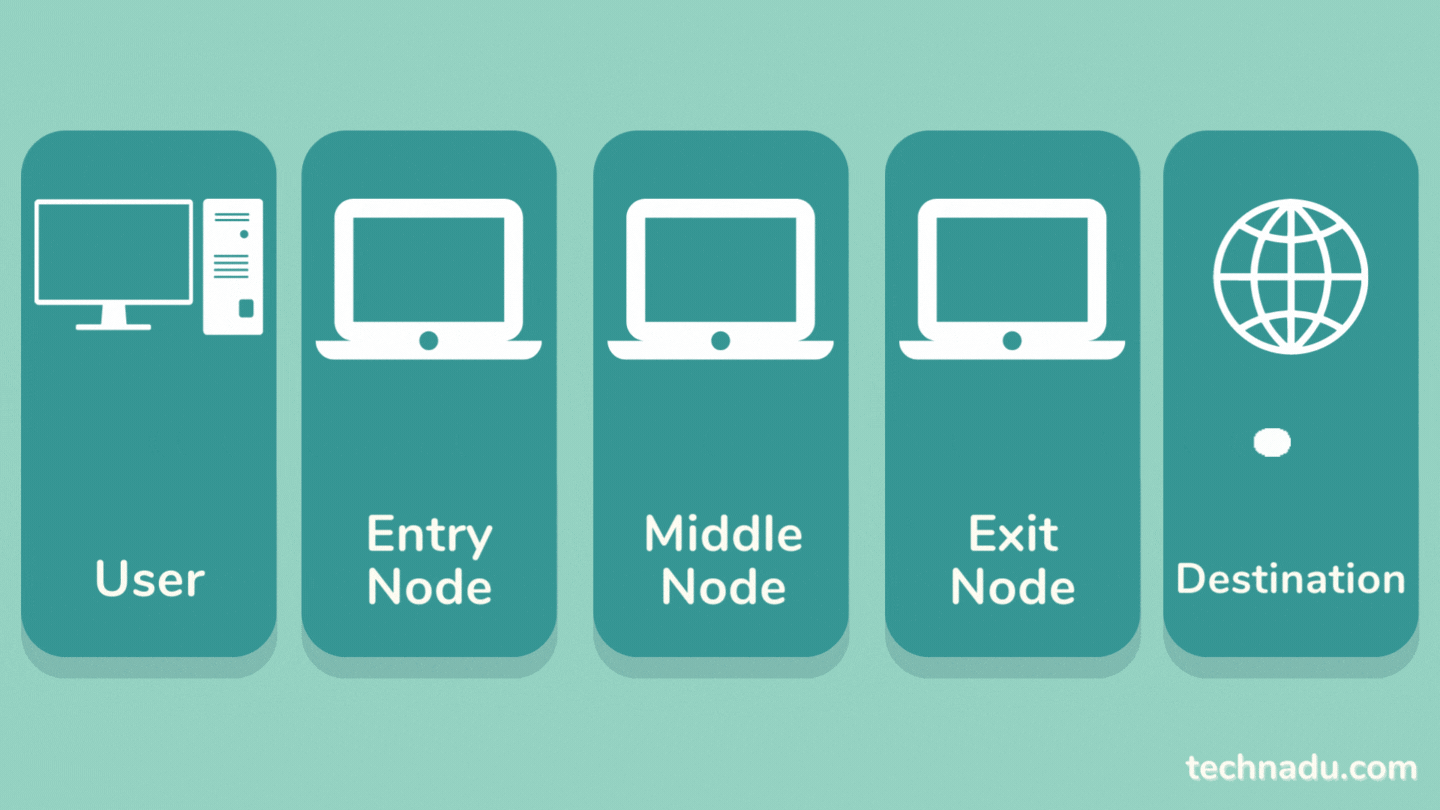
Tor works by routing your Web traffic through 3 nodes: entry, middle, and exit node. Each node has a role in stripping away your personally identifiable data.
Once your data enters the Tor network, it goes through an entry node. That node encrypts your traffic, meaning your data is not encrypted from the start. In other words, the entry node can see your actual IP address but can't see the contents of your data.
Then, your data goes through a middle node, which strips a layer of encryption implemented by the entry node. Then, the middle node adds its own layer of encryption. At this point, no one can see your data's origin, which means your IP address and other information is hidden.
There's one more stop for your traffic, which goes through an exit node. That final node repeats the previous nodes' encryption process, making your data extremely difficult to trace, which is the primary purpose of the Tor network.
Once the exit node decrypts your data, it can see the contents of your Web traffic - but it can't see its origin (which means you remain anonymous). Then, your data is sent to its destination.
When Should You Use Tor?
You should use Tor if you want to anonymize your traffic. Also, using Tor is perhaps the best way to access the Dark Web, which is based on "onion" addresses.
As you can see by now, Tor is the ultimate privacy and anonymity solution, but it’s not a network built, funded, and maintained to perform well or handle a large volume of data. And since there are several steps in terms of encryption, you can expect your Web speed to drop dramatically.
You should only use Tor for truly sensitive Internet communication, which absolutely depends on this level of security. Think of Tor as a sort of an Internet emergency line. People rely on it for serious work, and we shouldn’t be using it for irrelevant stuff.
So, if we take a look at Tor vs. VPN - it's clear that Tor is a more 'serious' option between the two (but "serious" doesn't always equal "better").
Tor: Pros and Cons
Even though Tor comes with many benefits, it's not an ideal option for most users. You'll see why once you understand Tor's upsides and downsides.
First, here are the biggest pros to using Tor:
- ANONYMITY: Tor is an excellent tool if you're after anonymity. It's powered by a multi-tier system of encryption, guaranteeing that no one will get to track you on the Web.
- EASE OF USE: Anyone can start using Tor, as no prior knowledge is required. Simply download the Tor browser on your device, launch it, and you'll access the Tor network.
- DARK WEB: Using the Tor browser, you can access ".onion" addresses. So, if you plan on using the Dark Web, you're forced to stick to Tor.
- PRICE: Tor is free-of-charge as it's run by a network of volunteers. The Tor browser is also free of charge, which means accessing the Tor network will cost you $0.
And now, here are the biggest cons to using Tor:
- PERFORMANCE: The Tor network is a very inefficient way to transport data due to its high-end encryption. So, expect massive slowdowns even if you have a high-speed connection.
- SECURITY: There's no way of knowing who owns the nodes transporting your data. In theory, that could be an intelligence agency. There's no transparency involved.
- FLEXIBILITY: Tor's nodes are scattered across the world. You can't pick an exit node, which means that you can't replace your IP with one from a specific country.
- PLATFORM SUPPORT: Tor is available on Windows, macOS, Linux, and Android. That means iPhones, iPads, and other platforms don't have access to the Tor browser.
What Is a VPN?
A VPN is a network designed to route your Web traffic. It uses VPN servers that hide what you do online by encrypting your Web traffic and replacing your IP address.
The main difference between Tor and VPNs is in their accountability and transparency. VPNs are in charge of their servers, which means they have the power to create infrastructure designed from the ground up to obfuscate your data and make it invisible to anyone else on the Internet.
Today's commercial VPN services do that by renting or owning their entire server fleet. They're in charge of creating and implementing a privacy policy, which can be designed not to collect your personally identifiable information. The best VPNs out there won't know anything about you, keeping your privacy intact even in relation to your Internet Service Provider (ISP).
Also, there are no third parties involved, which isn't the case with Tor. A VPN routes your traffic through a secure VPN tunnel, which means all your incoming and outgoing traffic is hidden - at any given moment. So, your ISP, the government, or hackers can't see what you do online.
How Does a VPN Work?
VPNs work by authenticating, encapsulating, and encrypting your incoming and outgoing Web traffic. Let's take a close look at what those terms mean.
Before you connect to a VPN network, your request needs to be authenticated. The VPN needs to know that you are really you and that the VPN server is also who it says it is. Under the hood, there may be security certificates and cryptographic security methods.
From the user’s point of view, it’s basically a username and a password. However, two-factor authentication is a good idea for those seeking the highest possible level of data protection.
Once your data starts routing through a VPN server, encapsulation ensues. That's a way for your data packets (such as a video stream packet) to be wrapped inside another packet (the VPN packet). In other words, anyone looking at the "envelope" of the packet won't know what's inside, which is how your privacy is guaranteed.
Lastly, encryption scrambles the actual content of the packet. That's done in different ways, but most of today's VPNs use AES-256 encryption, which is practically impossible to crack. In other words, even if someone gets to your encrypted data, they won't be able to read it.
The above said is a general description of how VPNs work. They use a range of VPN protocols to authenticate, encapsulate, and encrypt your data - which could be OpenVPN, WireGuard, IKEv2, IPsec, SSTP, PPTP, and more. At the moment, WireGuard and OpenVPN are your best options.
One key difference between VPNs and Tor's approach to encryption is that VPNs generally only encrypt the data once. There are some VPNs that allow or use double encryption, but that’s usually as far as it goes.
When Should You Use a VPN?
VPNs provide excellent privacy protection for almost all use cases on the Internet. A VPN is the way to go if you want to access blocked content with good data performance. It’s also a good solution for things that don’t require mission-critical privacy and anonymity.
That said, VPNs' primary role is to encrypt your data. So, if you access sensitive data on your device or want to prevent trackers from following you around, using a VPN is an excellent idea. Your online activities will be hidden even while using public Wi-Fi networks.
Then, many use VPNs to unblock the Web and bypass censorship. Access to the Internet can be pretty restricted in some countries, mostly authoritarian ones. The only way to open up your access to the Web and use websites unavailable in your country is to employ a VPN.
Lastly, many use VPNs to access more entertainment on the Web. Since VPNs replace your IP address, they make it look like you're elsewhere. That's how you can unblock Hulu, Paramount Plus, and Discovery Plus outside the US. You can also access more Netflix, Disney Plus, and HBO Max titles using your existing subscription.
VPN: Pros and Cons
VPNs are beneficial for many different types of users. To learn whether VPNs are the right pick for you, keep reading to learn more about their pros and cons.
Let's check out the biggest pros of VPNs:
- PRIVACY & SECURITY: The best VPNs out there implement a no-logs privacy policy, which means your data will 100% be safe. Then, they employ high-end protocols and encryption, preventing trackers from following you on the Web. That especially applies to the VPNs using WireGuard, which brings high-end cryptography and excellent speeds.
- ACCOUNTABILITY: VPNs are in charge of their networks, which means they guarantee the safety of their infrastructure. In other words, there's accountability and transparency involved, especially if you pick a reputable VPN service.
- EASE OF USE: You don't need technical knowledge to use a VPN. Many VPNs are made for first-time users, while you can also find options for advanced users. Those VPNs allow you to fine-tune various aspects of your VPN connection, letting you optimize its performance.
- NO BANDWIDTH THROTTLING: It's true that VPNs will slow you down a bit. However, if your ISP throttles your Web connection (while media streaming, which is often the case), a capable VPN can bypass ISP-induced throttling.
- BYPASSING GEO-BLOCKS: A VPN will help you browse the Web as if you're in another country. That means you can bypass geo-blocks and access websites and apps unavailable in your region. A VPN can even bypass sports blackouts.
Also, let's check the biggest cons of VPNs:
- MALICIOUS PRACTICES: Not every VPN is the same. Aside from fake VPNs that take advantage of your personal data, VPNs without a no-logs policy can collect your Web browsing data and forward that data to third parties. So, use a trustworthy VPN.
- PERFORMANCE: VPNs route your data through their servers, which means your data will travel more than usual. Therefore, you can expect your Internet speed to drop. However, the same best VPNs out there will slow you down by only 10-15%.
- DARK WEB ACCESS: Most VPNs don't let you access ".onion." addresses on the Dark Web. If that's crucial for you, there are a couple of VPNs providing "Onion over VPN" connections (such as NordVPN), routing your VPN traffic through the Tor network.
- PRICE: Even though free VPNs exist, they're not safe for use. Instead, you need to pick a commercial VPN service, which means you'll need to pay for a subscription. As expected, premium VPNs that offer a large server fleet, no-logs policy, and high-end protocols are more expensive.
What's the Best VPN on the Market Right Now?
Right now, the best VPNs you can find on the global market are ExpressVPN and NordVPN. Both are bulletproof privacy solutions with tons of extra features on offer.
Our #1 recommendation is ExpressVPN, which we've decided to feature after having tested more than 65 VPN services in total. Here are some of the key features this VPN brings:
- PLATFORM SUPPORT: ExpressVPN runs on any device imaginable. It brings native apps, is easy to install, and provides in-depth tutorials if you want to configure it manually (great for more advanced users). Here's how to get started with this VPN.
- EASE OF USE: You won't have a single issue with ExpressVPN, even if you have never used a VPN before. No prior knowledge or experience is required, as operating ExpressVPN is a one-click procedure. Connecting to a server is done instantaneously.
- SERVER FLEET: ExpressVPN has 3,000+ VPN servers in 90+ countries. It's among the most expansive VPNs overall, letting you obtain an IP from an endless array of countries.
- SIMULTANEOUS CONNECTIONS: You get up to 5 simultaneous connections. That means you can install ExpressVPN on multiple devices with ease.
- SECURITY & PRIVACY: ExpressVPN is a verified no-logs VPN service. It uses high-end protocols and AES-256 encryption, prevents website and app trackers, and allows you to unblock any website or app out there. It's great for practically any use.
ExpressVPN is closely followed by NordVPN, a trustworthy and reputable brand. Let's check out what makes NordVPN such an excellent commercial VPN service:
- PLATFORM SUPPORT: NordVPN is a decade-old VPN service, so it's no surprise to see it available for any computer, phone, tablet, streaming device, router, and more. We have a guide on getting started with NordVPN, so take a look.
- EASE OF USE: Like ExpressVPN, NordVPN is equally suitable for first-time uses. It also gives you some advanced options to fine-tune, which is excellent news for those with prior knowledge of VPN services.
- SERVER FLEET: NordVPN offers 5,000+ servers in 60 countries. Even though it has more servers than its competitors, the scope of its network is smaller (but still large enough). Also, NordVPN offers specialized servers, such as "Onion over VPN" servers, that let you use the Dark Web while using the highest level of protection available.
- SIMULTANEOUS CONNECTIONS: You get up to 6 simultaneous connections, which means using NordVPN at home and on the go should not be an issue.
- SECURITY & PRIVACY: NordVPN is a verified no-logs VPN with many audits under its belt. It uses AES-256 encryption in combination with ultra-strong protocols, such as NordLynx (which is Nord's protocol based on WireGuard). It's among the most secure VPNs available right now.
Of course, more options await. If you wish to check other reputable, capable, and trustworthy VPN services, check our central guide to the best VPNs overall.
Tor vs. VPN: What's the Difference Between Them?
The most significant difference between Tor and VPN is that VPNs are commercial products with a much higher degree of accountability and transparency.
Even though Tor and VPNs are very similar at their core, you'll find plenty of differences. So, to help you decide which of the 2 you should use, check the following table.
Tor vs. VPN: Which One Is Right For You?
Both Tor and commercial VPNs are excellent tools that are very good at what they do, but one can’t be swapped for the other.
Tor is the ultimate privacy tool for those of us who must protect our identities and activities. It’s a wonderful tool in the fight for freedom on the Internet. However, since it's decentralized, there's no way of knowing who's in charge of individual nodes.
On top of that, you can't pick your exit node, making it difficult to use Tor to unblock websites and bypass censorship. And speaking of individual nodes, they're not the most effective in routing your data, which means you can expect slow speeds overall.
On the other hand, VPNs are not impossible to compromise. Just very, very difficult. This means that unless you are literally trying to stay below the radar of major government intelligence services, it’s your tool of choice.
Furthermore, reputable VPNs feature no-logs policies, so you have guarantees that your data will be kept confidential. They're also great for torrenting, media streaming, and even online gaming. And, of course, they're suitable for bypassing censorship in practically any country.
Final Thoughts
We hope our Tor vs. VPN comparison has helped you make up your mind. Choosing your weapon of choice to preserve your privacy should be done very carefully. In that sense, both Tor and VPN should be able to meet your needs.
However, we believe VPNs are more aligned with the needs of most users. They're a safer bet right now, especially in the long run. With that said, we'll remind you that we recommend ExpressVPN, which truly is the best VPN available today.
You've reached the end of our Tor browser vs. VPN comparison. If you have any questions for us, let us know via the comments section below. Lastly, thanks for reading!