Top Password Managers Found to be Vulnerable to Sniffing
- Five of the most widely used password managers were found to use poor memory sanitization techniques.
- Hackers who know of the specifics may target users and grab their passwords from memory strings.
- Using a password manager is still recommended than not using one, but there is certainly room for improvement.
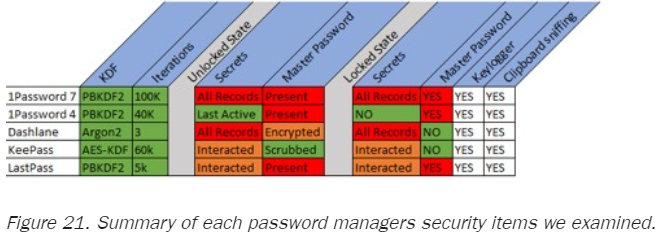
According to a detailed study conducted by researchers at the ISE (Independent Security Evaluators), all top password managers were found to contain certain weaknesses that make them vulnerable to attacks by hackers. The products that were thoroughly tested are the latest versions of 1Password4, 1Password7, Dashlane, KeePass, and LastPass, totaling a userbase of about 60 million users. The ISE researchers have focused on how passwords that are stored in the disk are protected, and how the keylogging and clipboard management is implemented. The operational states which were investigated are the “running”, “not running”, and “locked”.
Starting with 1Password4, the software failed to scrub the master password from memory when in the “locked” state, making it possible for a hacker to recover and deobfuscate it, getting access to the whole pass vault. The most recent version of the same product that is 1Password7 is actually even less secure when in the “running” state. This newest version caches all passwords in memory, including the master, the secret key, and all individual passwords. When transitioning between states, 1Password7 is not scrubbing the passes from memory, increasing the risk of exposure.
Proceeding with Dashlane, this tool stores passwords in XML in cleartext when in the “locked” state. Extracting this information is straightforward for those who know it’s there, although this data stays in memory for a few minutes before it gets overwritten. The open source KeePass tool is using encryption/decryption interactions, but its scrubbing action is sometimes failing to clear some specific memory buffers when in the “locked” state. This makes it possible for a hacker to scan the memory and connect/extract the login data pieces that are found.
Finally, LastPass followed a proper master-pass obfuscation and overwriting procedure, however, the password entries are kept in the memory, even after the program is placed in the “locked” state. If a hacker performs a strings dump, it is possible to recover the master password and all of the other password entries as well.
From the ISE study
ISE researchers conclude that if password managers employed SGX features, runtime process modification detection, and limited the exposure of data transversing to the OS, the results of the study would be very different. Still though, using a password manager is considered a far safer practice than not using one, and even if a hacker gets their hands into an obfuscated password, it may mean that brute forcing its decryption is not practically feasible. That said, all tools were found to work well when in the “not running” state. Where the situation gets risky is the “locked” and the “unlocked” states.
Which tool is your password manager of choice? Let us know in the comments section below, and help us spread the word by sharing this post through our socials, on Facebook and Twitter.