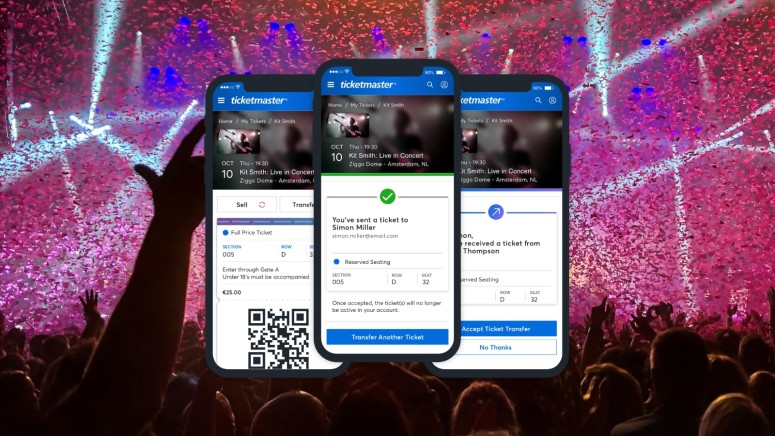
Ticketmaster Hackers Release 170,000 Stolen Taylor Swift Tickets and Want $2M Ransom
- The hackers who claimed the Ticketmaster data breach announced releasing almost half of the Taylor Swift tickets they allegedly stole.
- Advertised as “free tickets,” the barcodes were leaked on a popular hacker forum.
- A $2 million ransom asked from the ticketing company is also attached to the post.
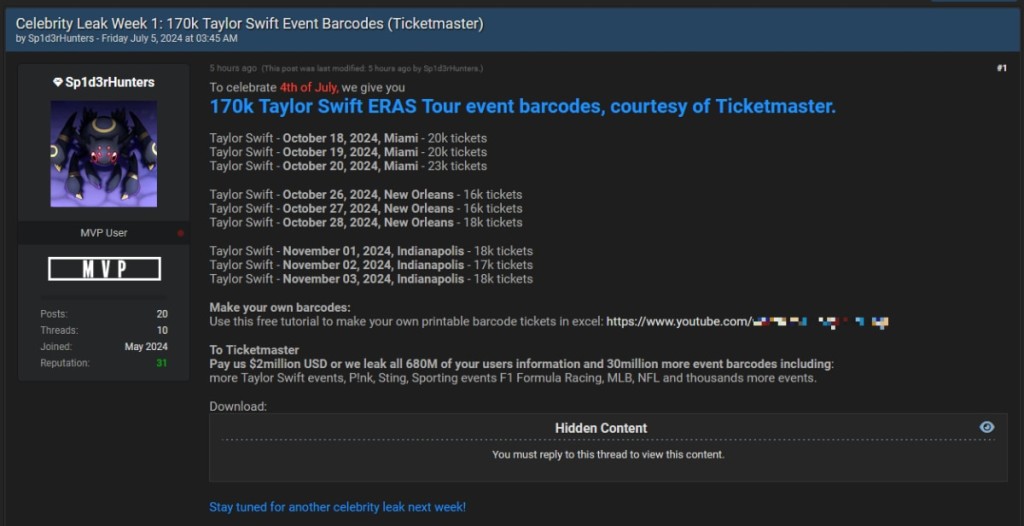
The cybercriminals who claimed the Ticketmaster data breach posted a sample leak of 170,000 free barcodes for Taylor Swift’s ERAS Tour on a popular hacker forum, saying they allegedly own 440,000 stolen tickets for this tour.
The tickets are reportedly for nine upcoming Taylor Swift concerts in three U.S. cities: Miami, New Orleans, and Indianapolis, which will occur between October 18 and November 3. The author even posted a guide to create printable tickets at home.
The post includes a message addressed to Ticketmaster saying the hackers want $2 million not to leak 680 million user details and 30 million more event barcodes they reportedly own, including more Taylor Swift concerts, Pink, and Sting tickets, and sporting events such as F1, MLB, NFL, and “thousands more.”
The Live Nation Entertainment-owned ticketing company still has time to reissue the stolen barcodes to the affected buyers, who are the rightful owners. In the meantime, Taylor Swift fans should be weary of phishing messages leveraging the “free concert tickets” lure.
The post was published by an entity using the handle Sp1d3rHunters, a merger of Sp1d3r and ShinyHunters. Both actors have been associated with the Ticketmaster data breach.
These breaches have been attributed to the UNC5537 threat actor. However, a member of the infamous ShinyHunters hacking group revealed earlier this month how they reportedly stole customer data from Snowflake accounts, and now it seems Sp1d3r and ShinyHunters have created an alliance.
The approximately 165 companies using Snowflake environments linked with the massive data breach include Ticketmaster, Ticketek, Neiman Marcus, Santander Bank, LendingTree subsidiary QuoteWizard, Advance Auto Parts, and Pure Storage.
In June, hacker Sp1d3r was selling data reportedly stolen from the cybersecurity company Cylance, including 34 million customer, prospect, and employee emails.
Incident response firm Mandiant said the data was stolen by threat actors leveraging leaked credentials collected by several info-stealer malware variants. These belonged to Snowflake customer accounts that did not enable the multi-factor authentication (MFA) feature.