Tibetans Using Android Were Also Targeted by the Uyghur iOS Malware
- The Uyghur spyware was far more versatile than initially anticipated, deploying Android exploits too.
- A new report shows that the same campaign targeted Tibetans too, and the actor was the same.
- Chinese-state actors have a long record of targeting activists, and this operation was part of it.
According to a Citizen Lab report, the recent attacks of Chinese state actors against the community of Uyghur Muslims were not the whole part of the story. Apparently, Tibetans were also targeted in the context of the same operation, and Android exploits were also included. At the start of the month, researchers from Google’s Project Zero unveiled an operation involving “Watering Hole” websites that infected all versions of iOS with malware that carried a rich set of exploits. Some of these exploits were zero-days, so Apple was exposed in the media and decided to provide an answer to the allegations.
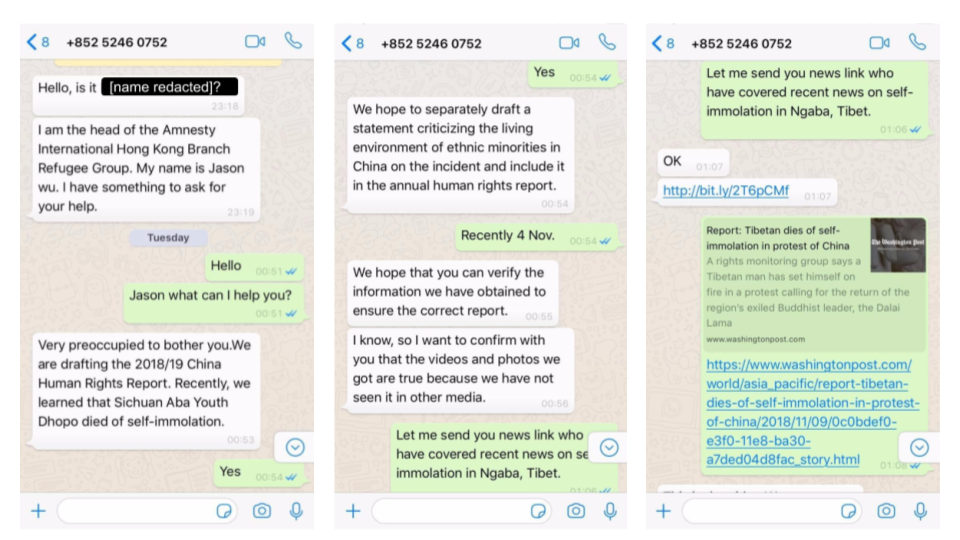
What Apple had to say was that the number of the actual victims was very small, the time of the operation was very short, and that Project Zero team inflated the issue to damage its market profile. If Apple knew that Android was also affected by the same malware, they would have a lot more or different things to say about the story for sure. Citizen Lab states exactly that, with its findings including a lengthy exposure of Tibetans to iOS and Android spyware, that infected their devices after they clicked on shortened links that reached to them via WhatsApp.
Source: citizenlab.ca
The texts were sent by actors who posed as journalists, NGO workers or other fake personas and tricked Tibetans into believing that the shared links were legitimate. In some cases, the landing pages were OAuth phishing websites. Citizen Lab sees a clear overlap between the campaign that was reported by Project Zero and the one they discovered. As for the details about the exploits that were used, on the Android platform, these exploits were focused on the web browser and none of them were zero days. This means that for Tibetans using the latest Android version and security patches, there was no risk, but we know that this is hard to find in the Android ecosystem.
That said, for people in risk, activists, targeted ethnic and religious minorities, it is clear that choosing Apple over Android or vice versa will usually not make a difference. What will make a difference in staying protected is to update your mobile OS and apply the latest updates on the system and all the apps that you're using. Finally, having researchers disclose the whole part of a story, and doing so in a way that raises universal awareness is vital.
This time, the Project Zero may have somehow missed the exploits that concerned the Android platform when they analyzed the spyware samples and reported only the iOS exploits. We like to believe that they did not opt to play a marketing game, damaging a competitor temporarily, only for someone else to make the additional discovery a couple of weeks after that. Project Zero researchers do not have a history of following unethical reporting approaches, so for now, we remain confident that they would have reported the Android exploits if they knew about them.
What is your opinion on the above? Share it with us in the comments section down below, or on our socials, on Facebook and Twitter.