Three Million Cards From “Dickey’s” Restaurants for Sale on “Joker’s Stash”
- A new collection of credit card TR1 and TR2 data has appeared on the dark web, and it looks like it’s from “Dickey’s” BBQ.
- The chain hadn’t realized the breach until this batch appeared online, but the hackers already spent 15 months stealing cards from them.
- The consequences for the cardholders are dire, and the reminder to use cash next time is clear.
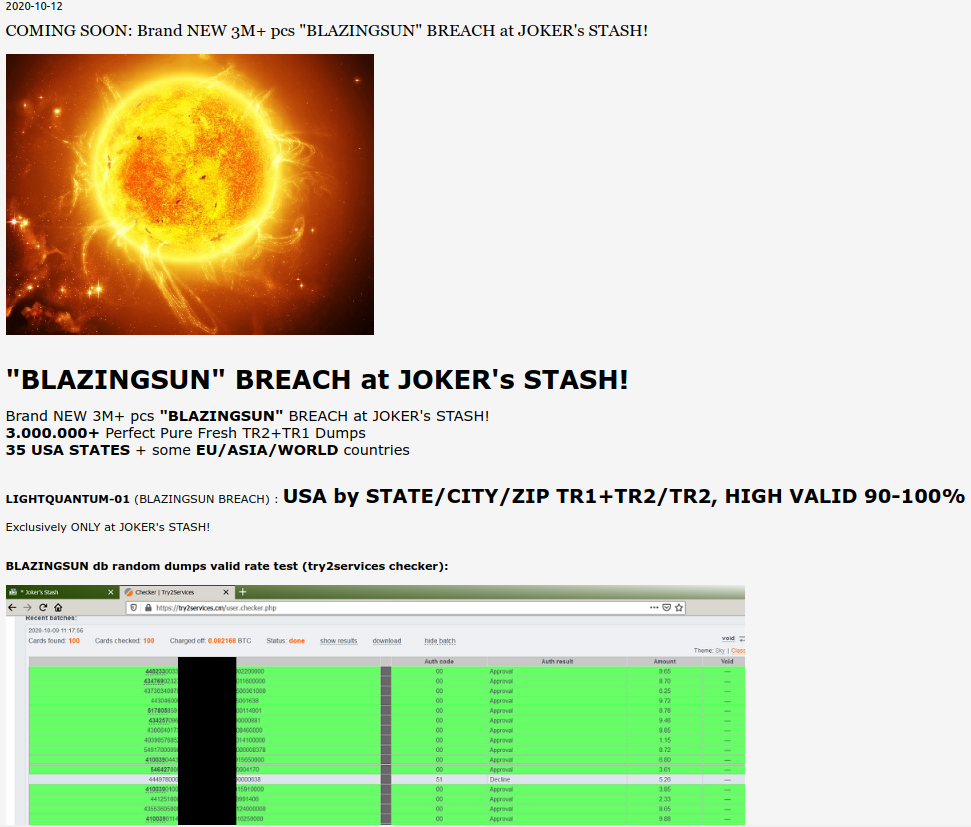
Roughly three million credit cards have appeared on the notorious dark web carding marketplace “Joker’s Stash,” and the listing claims to be a collection of data that was stolen during a lengthy data breach at the systems of Dickey’s BBQ Restaurants. The cards come from more than a hundred locations of the American chain, so this is either the result of a corporate network breach - or, more likely, a PoS malware infection and card data exfiltration operation.
The seller claims that most of the cards are valid, giving a percentage between 90% and 100%. This means the restaurant chain is most likely unaware of what happened. In fact, the hackers were allegedly in Dickey’s systems for the past 13 to 15 months, and the card entries match this claim.
Gemini, a breach monitoring platform, suggests that the exposure window is between July 2019 and August 2020 and that the data is derived from 156 individual locations across 30 US states.
As for the type of data made available, this includes both TR1 and TR2 and the amount of the captured transaction. By having the track1 and track2 numbers/codes, one could create clone cards and use that data to burn it to the magnetic strips. Even without knowing the PIN or anything else about the card, crooks could use the cloned card to carry out contactless payments that are valid for smaller amounts.
Researcher Brian Krebs reached out to Dickey’s a few days ago, and they answered with the following statement:
This is a catastrophic event for the card owners, who will now have to monitor their accounts or straight out freeze them. It is also another reminder that you should not blindly trust PoS terminals used in large chains that don’t bother with security and still use outdated systems.
If there’s another way to pay, like cash, or NFC, or electronic payment methods, pick that instead. If you use your card for a meal, or you may find yourself in great trouble.