Thousands of QQBrowser Users Took Part in DDoS Attack Without Knowing
- Researchers notice a weird DDoS attack that involved thousands of Chinese QQBrowser users.
- The attack was conducted through the “pingback” command, normally used for legitimate purposes.
- The users were probably tricked through malvertising and followed a link via a WeChat room.
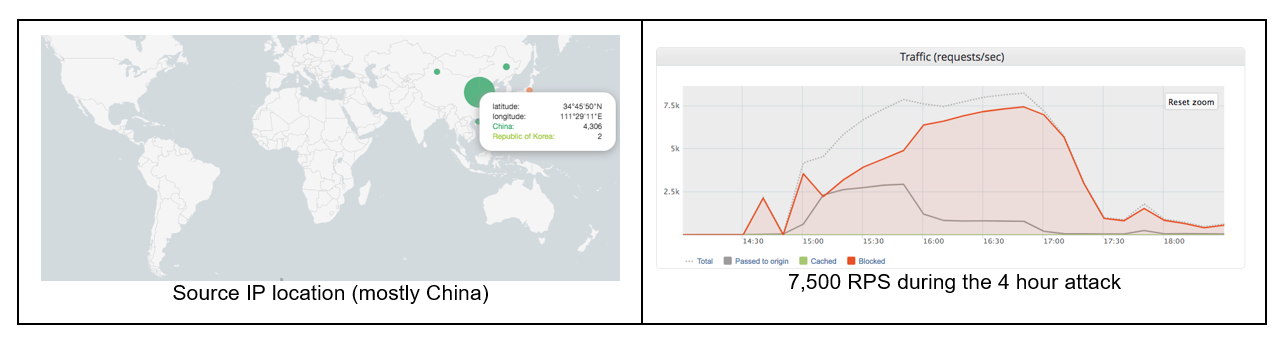
As reported by Imperva researchers, there has been an incident of an HTML5 Pingback DDoS attack that lasted for four hours, generated a peak RPS (requests per second) of 7500, and produced an overall of 70 million requests. What piqued the interest of the researchers was the fact that most of the 4000 IPs that took part in the DDoS attack were coming from China, something unusual. By investigating further, they found that both the “ping-from” and the “ping-to” values pointed to “http://booc.gz.bcebos.com/you.html”.
image source: imperva.com
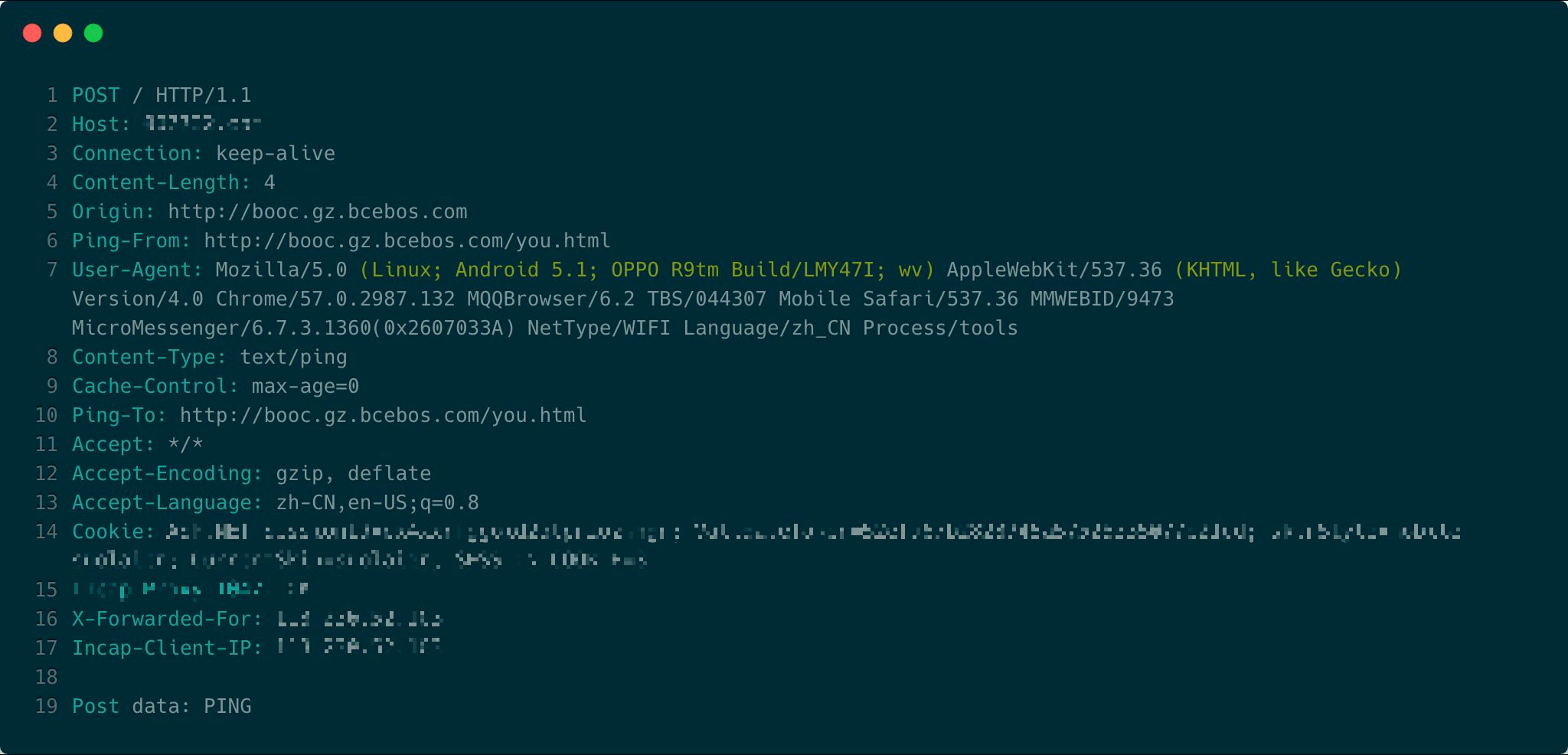
Ping is an HTML5 command that is used to specify a list of URL that should be notified when the user clicks on a specified hyperlink. This is a perfectly legit command that has been utilized in a malicious way before, but never by a collective of internet users who are using the same mobile browser (in this case QQBrowser) and come from the same region. The HTML samples that were analyzed by Imperva feature two external JavaScript files that helped create a “ping” request to the target website every second. As it seems, the thousands of QQBrowser users have been deceived into visiting the website that loaded the DDoS HTML and made to stay there for as long as possible, since they generated a ping request for every second that passed.
image source: imperva.com
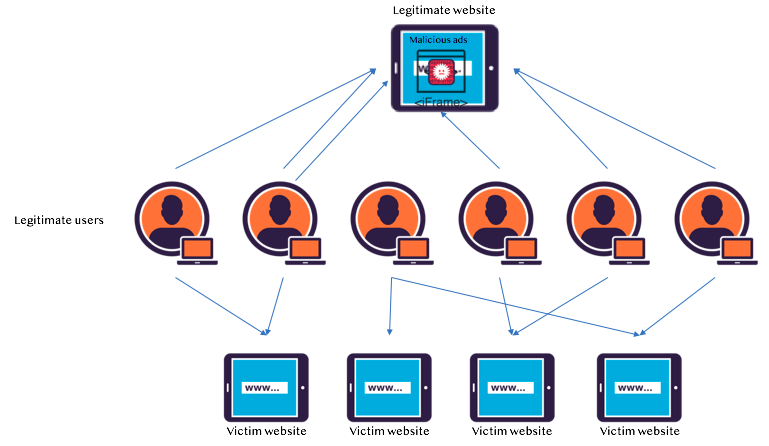
A possible scenario through which this type of attack could have been set up and carried out would involve social engineering and malvertising. As the WeChat app is quite popular in China, and as it uses QQBrowser to open links by default, it is likely that the point of the link injection was a popular WeChat room. The following diagram shows how this could have worked for the actors, putting thousands of unbeknownst users in the scheme.
image source: imperva.com
QQBrowser just happened to be the tool for this particular attack, but that doesn’t mean that other browsers are safe from being exploited by a ping-based DDoS attack. To the contrary, major browsers like Chrome, Safari, and Opera, will even strip away the very capacity that the users had to disable hyperlink auditing, part of which the POST requests and pingback commands are. This has previously sparked discussions on the users’ privacy protection, as getting away from online tracking will become much harder, but the DDoS attack that we explored in this post paints yet another dire picture for the functionality of the browsers — that of taking part in DDoS attacks without being able to stop it.
What are your thoughts on the above DDoS Attack? Let us know by leaving a comment down below, and don’t hesitate to do the same on our socials, on Facebook and Twitter.