This is how the US Law Enforcement Breaks into Phones
- Two documents containing tests of phone break-in tools from NIST have been published.
- Most older devices are completely unprotected from these tools, while the newer ones are harder to crack.
- Some see this as proof that asking for backdoors is aimed at mass surveillance and not fighting terrorists.
At the same time that the US government is asking for the banning of strong and backdoor-less encryption in software tools, a new report that has been recently made available to the public indicates that the law enforcement authorities don’t even need it. There are multiple tools from companies like Cellebrite, which exploit undisclosed zero-days to develop phone breakers for governments to use. The published reports indicate how successful these tools are against various popular devices and systems.
Source: Vice
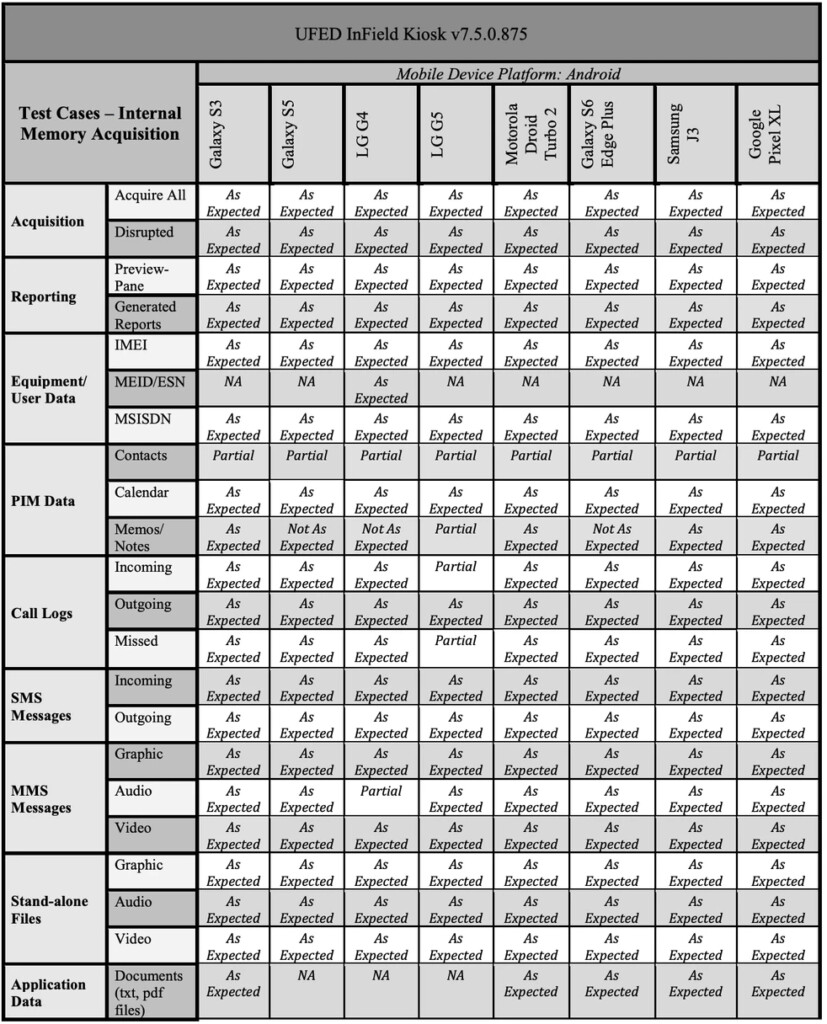
Cellebrite’s UFED InField Kiosk 7.5 test results show that the following devices are completely or partially vulnerable to it:
- iPhone 4
- iPhone 5S
- iPhone 6S Plus
- iPhone 7 Plus
- iPad Mini v9.1
- iPad Mini v11.3
- Samsung Galaxy S3
- Samsung Galaxy S5
- LG G4
- LG G5
- Motorola Droid Turbo 2
- Galaxy S6 Edge Plus
- Samsung J3
- Google Pixel XL
Of course, the above are the devices that were used by the US authorities for the testing sessions, so this is not a complete list of everything that Cellebrite’s tools can break into. Also, more recent devices running newer software are harder to crack. For example, the tests showed that Huawei’s P20 Pro was unhackable while the Samsung Galaxy S9 and the Google Pixel 2 gave away very little data. Depending on the type of the target, other experts in the field may be capable of providing a solution to unlock the device. For example, someone would have better chances of unlocking a recent iPhone device by using a product from “GrayShift”. Other tools that were used in the NIST tests include solutions from Paraben (E3:DS), and MSAB (XRY). These two had some specializations, but in general, they weren’t as powerful.
Private digital forensic experts claim that this is just another proof of the fact that the FBI’s requests for backdoors are blatant lies. Allegedly, the government wants to end encryption not to fight terrorists but to impose mass surveillance on its citizens. This is a position that has many supporters in the states. An FBI veteran told Motherboard that sometimes, even if someone manages to break into a phone, the raw data they’ll access will be hard to convert into a readable and useful form.
The field is constantly moving and the game is always changing. Other unnamed sources claim that Android has gotten a lot harder to break today, while iOS has gotten a lot easier to crack than it was in the past. The takeaway from this story is that if you want to maintain a good level of privacy and security on your phone, you should use the latest software and hardware available.