There’s a New “FatalRAT” in Town Using Telegram Channels to Move About
- A new powerful and sophisticated malware named "FatalRAT" has appeared in the wild, spreading on Telegram.
- The RAT can detect where it's running, what security tools are deployed, and what browsers it needs to target.
- The main goal is to exfiltrate credentials from the victims using a keylogger and encrypted communications.
A new malware called "FatalRAT" has appeared in the wild. It is a very sophisticated remote access tool that can perform a wide range of evasion, persistence, logging, and info-collecting tasks. The discovery was the work of AT&T Alien Labs, which sampled the malware and analyzed it thoroughly. For now, there has been no specific attribution for the campaign that distributes the new RAT, but AT&T's report does contain indicators of compromise, such as C2 IP addresses.
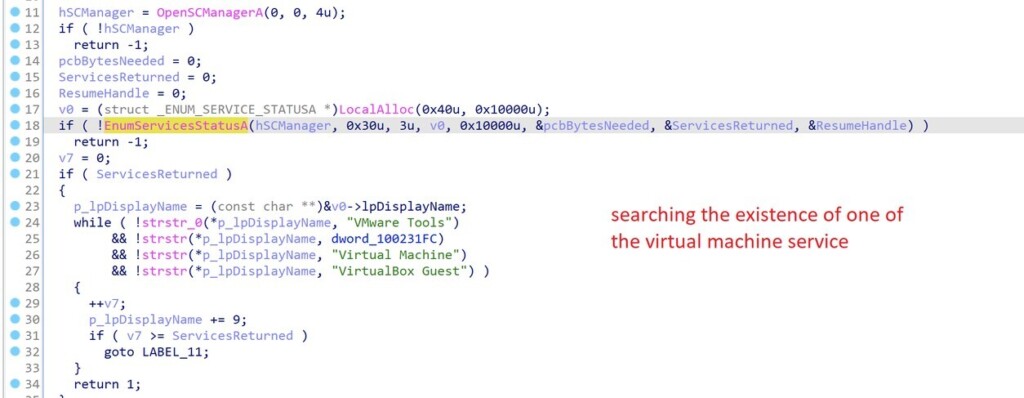
FatalRAT starts its execution by running several pre-injection tests to confirm that it's not running inside of an analyst's virtual machine. If it confirms that it's not, it decrypts its configuration strings and connects to the command and control address. After that, the malware performs a registry key edit to disable the ability to lock the computer, and then a keylogger is activated. The persistence is achieved either by a second registry modification or by creating a new service set to initiate upon system boot. The malware also checks if any security products are running on the device.
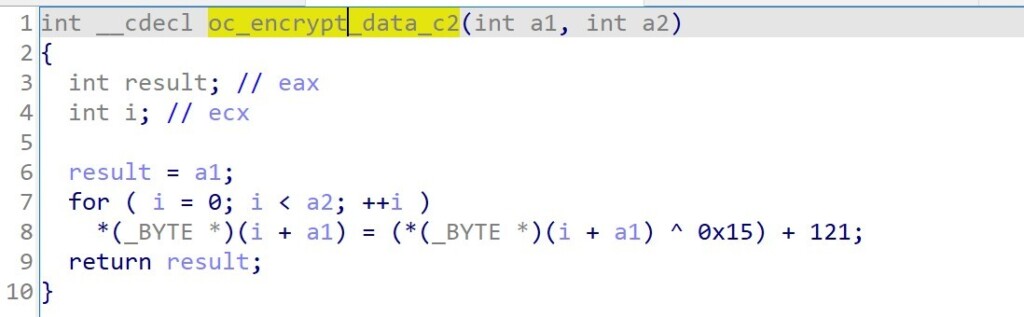
The information that is collected and sent to the C2 includes the external IP address, the username, and other basic information about the host system. The communication is encrypted, using a one-byte XOR key and the addition of a constant to derive a 121-character value.
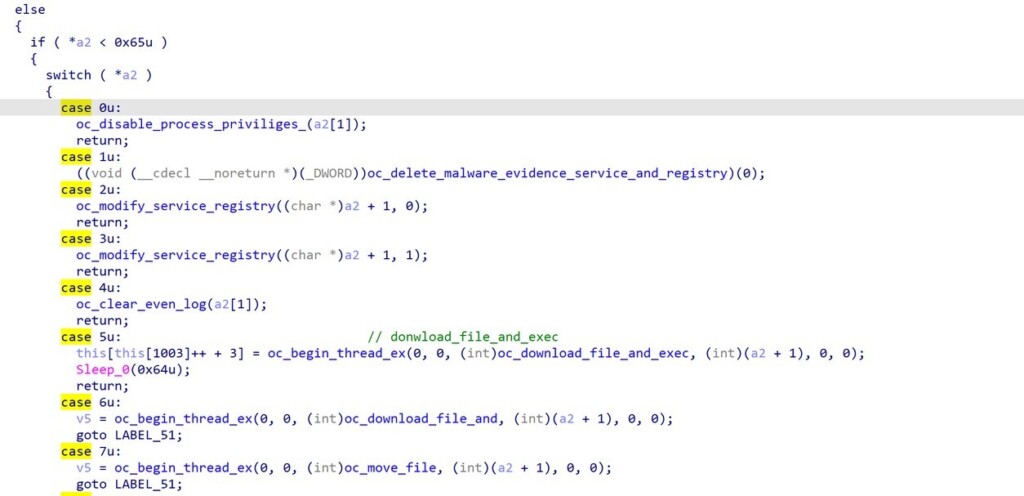
The commands that are included in the RAT are the following:
- Keylogger
- Change resolution
- Uninstall UltraViewer
- Download and install AnyDesk
- Execute shell commands
- Modify registry keys
- Download and execute a file
One trick deployed by the actors to steal user credentials is wiping the data on web browsers found in the infected system so that the victim is forced to re-enter their usernames and passwords. This is captured by the keylogger and is exfiltrated to the C2. FatalRAT activates a different wiping routine depending on which browser is cleaned. The browsers that are supported by the malware are Edge, 360Secure Browser, QQBrowser, SogouBrowser, Firefox, and Chrome.
The observed spreading mechanism is Telegram channels, but this is something that could change soon. In general, you should avoid downloading executables from shady sources, keep an antivirus/antimalware installed and up to date, monitor network traffic, and deploy an endpoint detection and response solution.