There’s a Ledger Phishing Campaign That Has Been Going on Since October
- A persistent campaign targeting Ledger users is stealing recovery phrases and assets.
- The actor is using a backdoored Ledger Live application and also a web-based phishing page.
- The users had their contact details exposed in October, and this is what actors are using now.
Someone is persistently targeting Ledger users through a sophisticated phishing campaign, trying to steal their recovery phrase and gain access to their cryptocurrency assets. According to Proofpoint researchers who dug deeper into this, the particular actor’s activity first appeared in October 2020. The hackers sent messages using the data that was stolen during a July 2020 security breach against Ledger, and which compromised the names and contact information of roughly 9,500 users.
The platform informed the users of the risk when the breach occurred, but this is obviously not enough to reduce the phishing success rate down to zero. The campaign continues to yield success for the actors even today, and they demonstrate a very high level of care in the preparation of the messages and the theming used.
Related: These Were the Most Imitated Brands in Phishing Campaigns During Q3 2020
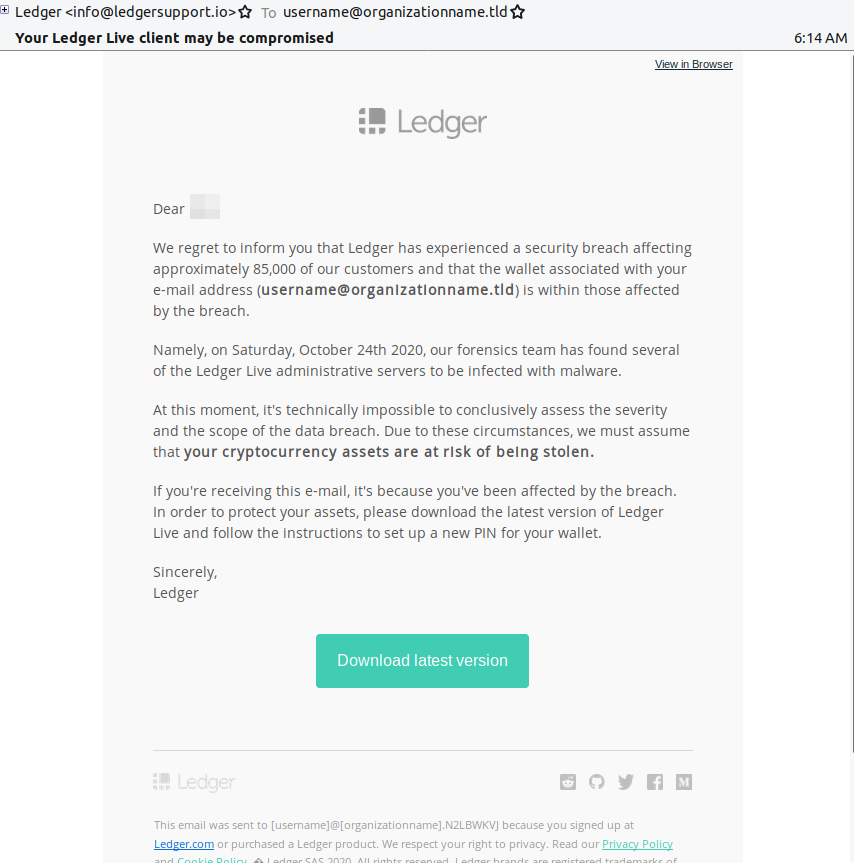
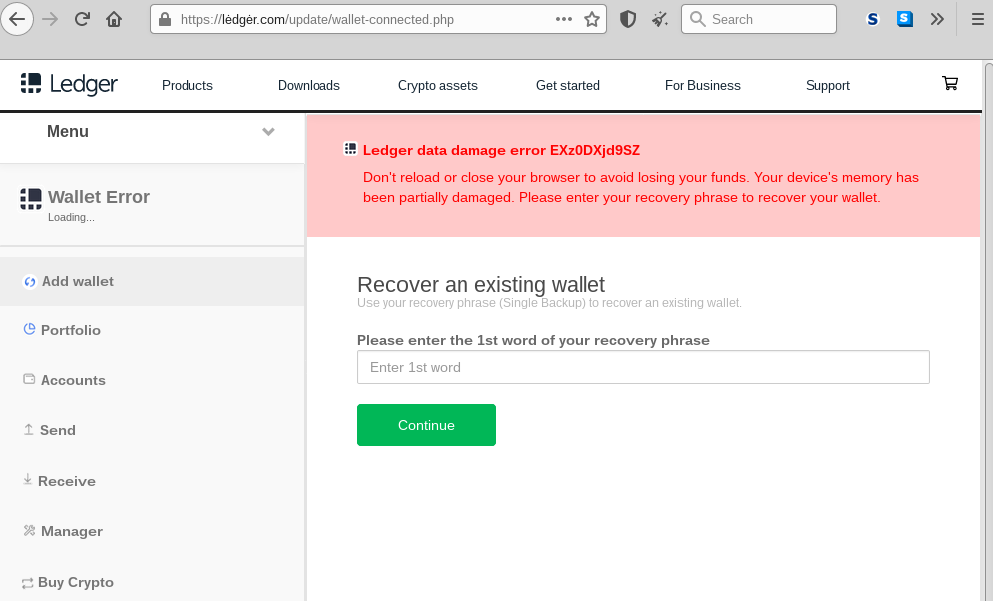
In most cases, the emails that supposedly come from Ledger talk about an October breach that resulted in the compromise of the recipient’s credentials.
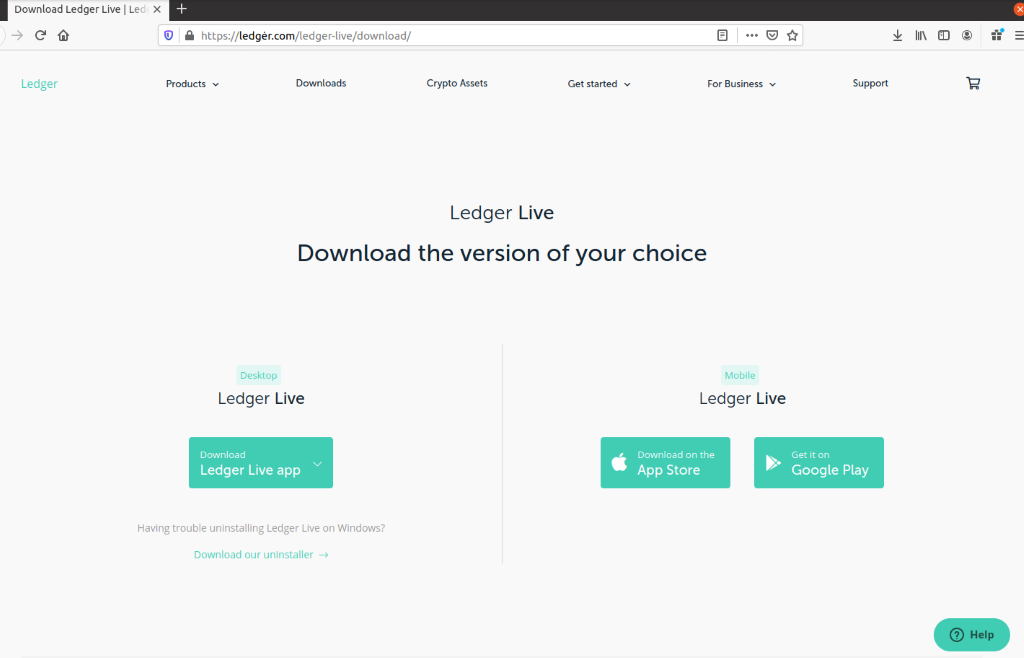
The victim is urged to download a “new” version of the wallet and set up a new PIN for their wallet. There’s an embedded download button in the message body leading to a spoofed Ledger page that uses a Punycode character to bring the URL as close to the real thing as possible.
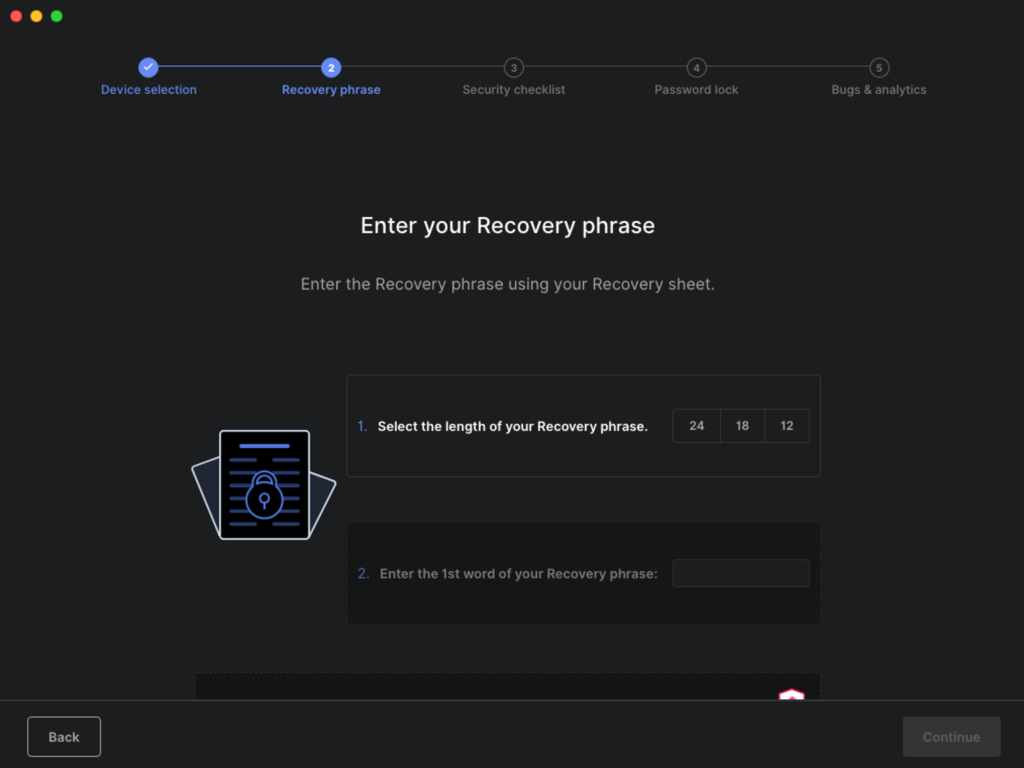
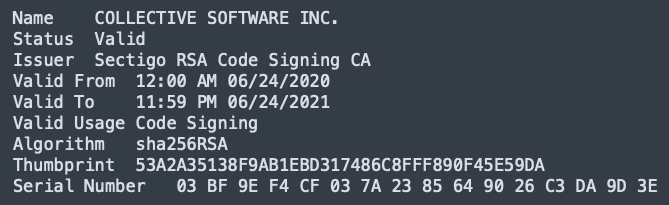
The fake Ledger app is using a valid code signature and version 2.15.0 of the real Ledger Live as a basis. The goal of the app is to grab the recovery phrases set up by the users. The actors would then use it to generate a copy of the victim’s private keys, and eventually, to steal the currency they hold.
This is why the spoofed app doesn’t even give users the option to “get started,” but instead points them to restore from recovery phrase. After entering this precious piece of information, the victim is then asked to enter a PIN, and with that, the actors pocket all they need to move forward.
Apart from the laced app, the actor is also using a web-based platform to steal the recovery phrase, hosted on the lėdgėr[.]com, which is still live at the time of writing this. Leading people there is a task that the actor carries out by sending SMS, exploiting the user contact details that leaked back in the October breach. In this case, the user is also informed about the need to recover an existing wallet due to a security incident.