The ‘Google App Engine’ Could Be to Blame for Stealthy Phishing Attacks
- Phishing actors are currently abusing the Google App Engine to spawn a large number of malicious URLs.
- The same abuse could be employed by malware campaigners while stopping them through reporting URLs would be impractical.
- Google’s team has to look deeper into this and change how their soft-routing works for invalid URLs.
Security researcher Marcel Afrahim has discovered a novel technique that involves the abuse of Google’s App Engine domains to support the operations of phishing or malware campaigns without running the risk of detection. Malicious actors are always looking for possible ways to abuse legitimate and widely trusted cloud service, hosting, and engine vendors, and this case is precisely of this type.
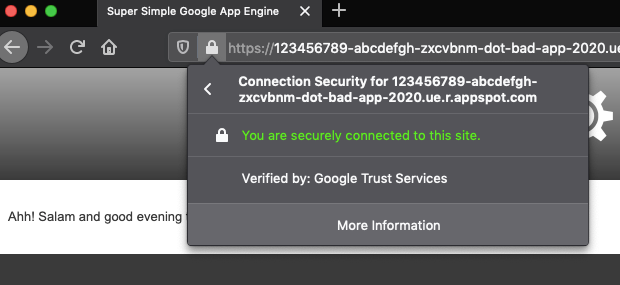
According to the researcher’s report, the issue lies in the way that the Google App Engine generates and handles subdomains. More specifically, a subdomain created with the Google App Engine can represent an app version, the service name, the project ID, the region ID, etc.
When something goes wrong, instead of serving a 404 error, a soft-routing procedure is initiated, redirecting the default page. By abusing this system, one can create many malicious subdomains that always route to the default app page.
Source: Medium.com
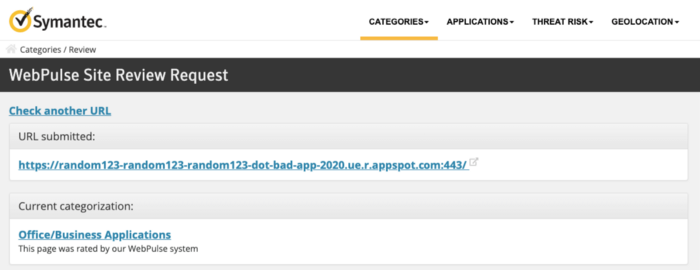
This creates two distinct problems. First, reporting abuse on a set of these subdomains won’t do much against the actors. Secondly, blocking all malicious subdomains is practically impossible since the URL structures weren’t developed in a way that permits such close-up monitoring and controlling.
Source: Medium.com
Even if someone was to deploy bots and sophisticated blocking tools, differentiating between the “PROJECT_ID” and “VERSION” URLs would be impossible, let alone the fact that these URLs would be generally considered trustworthy by most security solutions out there.
So, essentially, one could have a large number of URLs, which are all trusted, leading to malware payloads through soft-routing. If the actor was to deploy a Google Drive phishing kit instead of planting malware, they could steal people’s credentials this way.
Massive Microsoft #Phishing Attacks on appspot.com(Google App Engine). ⚠️
Phishing URL: hxxps://<xxxxxxxxxxxxxxxx>-dot-millinium[.]ey[.]r[.]appspot[.]com/app/index
IP: (Google App Engine)
Brand: Microsoft
List: https://t.co/xj3AOthHZUhttps://t.co/tdzauZVADX pic.twitter.com/yUD4ieKLWD— Osumi, Yusuke (@ozuma5119) September 13, 2020
To make matters worse, phishing actors appear to know all that already, as the security flaw is currently being under active exploitation. The actors are using random characters prefixed to the hostnames, so the process of phishing email distribution is fully automated and quite successful.
Again, reporting these URLs won’t stop the actors, so the only way to plug this hole is to change the way Google’s App Engine works and prevent its abuse.
Read More:
- Nasty PHP Malware Reinfects Cleaned Website Files in Less Than a Second
- Russian Draft Bill Threatens Apple’s and Google’s 30% Cut on Their App Stores
- Google Is Taking Steps to Prevent Geo-Tag Hijacking on Android 11