Thai Mobile Network Operator Exposes 4.7 Terabytes of Data Online
- A telecommunications service provider has exposed a massive volume of data belonging to its customers.
- At the same time, the incident exposes the internet activity logging practices of this particular firm.
- Approximately 40 million customers were exposed for as long as three weeks.
Security researcher "xxdesmus" has discovered a humongous data set in an unprotected ElasticSearch database on May 7, 2020. After investigating, the researcher figured that the data belonged to "Advanced Info Service" (AIS), Thailand's largest GSM mobile phone operator. The database's owner was contacted via multiple channels between May 13 and 21, 2020, but failed to respond. Eventually, "xxdesmus" reached out to "ThaiCERT," which is Thailand's official point of contact and the incident response agency dealing with computer and internet security incidents. The next day, the database was secured by its owner.
Source: rainbowtabl.es
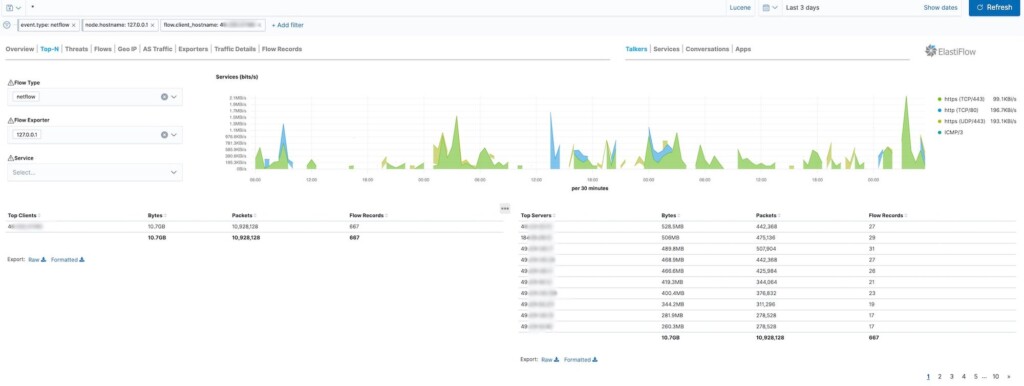
BinaryEdge first indexed the particular database on May 1, 2020, so the total period of exposure was three weeks. This is quite serious, especially when you're exposing highly sensitive data. The server was handled by a subsidiary of AIS, named "Advanced Wireless Network" (AWN), who were feeding the live database with user DNS query logs, customer NetFlow logs, source IPs, and more. So, in that database, the company logged the internet activities of its 39.9 million customers. Everything's there, from who made a DNS request, which location they did it from, what device they used, and what website they visited. Every day, there were 200 million new data rows added in the database - so, until May 21, 2020, there were 8,336,189,132 documents totaling 4.7 terabytes of size.
Source: rainbowtabl.es
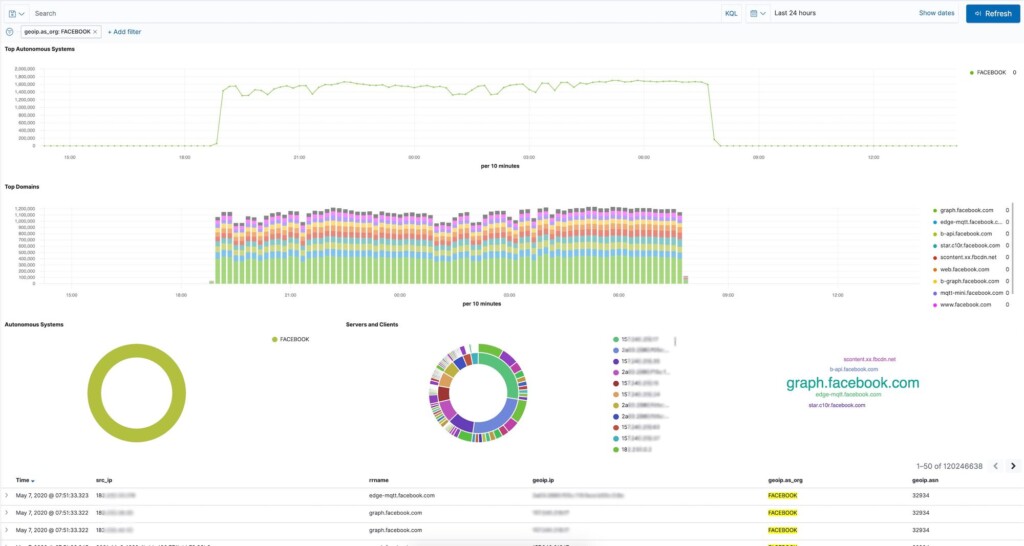
Apparently, AWN was using a tool that captures traffic details and feeds the information into the ElasticSearch database in a form that can be visualized. The telco could review the DNS traffic and filter stuff like domains and IPs, and it was generally engaging in unethical practices. The researcher has even found saved filters that were created for looking into Facebook traffic. This is pretty specific, so there can be no explanation involving an effort to manage traffic and loads on the network more effectively.
Source: rainbowtabl.es
The logging of the data goes down to a single customer, with the internet provider being able to see what types of traffic come from a particular IP, which websites were visited, and what devices, AV tools, and browsers they're using. All that said, this security incident exposes the AWN practices more than the user data itself. The only way we can avoid this type of logging from our ISPs is by using DNS over HTTPS, securing our privacy, and closing the door for spying.