Telegram Zero-Day Allowed Malicious Android APKs to Masquerade as Multimedia Files
- A zero-day flaw targeting Telegram for Android was up for sale on a hacker forum.
- The exploit displays an Android app as a multimedia preview shared in channels, groups, and chat.
- The now-patched vulnerability downloaded a malicious APK payload on users’ phones.
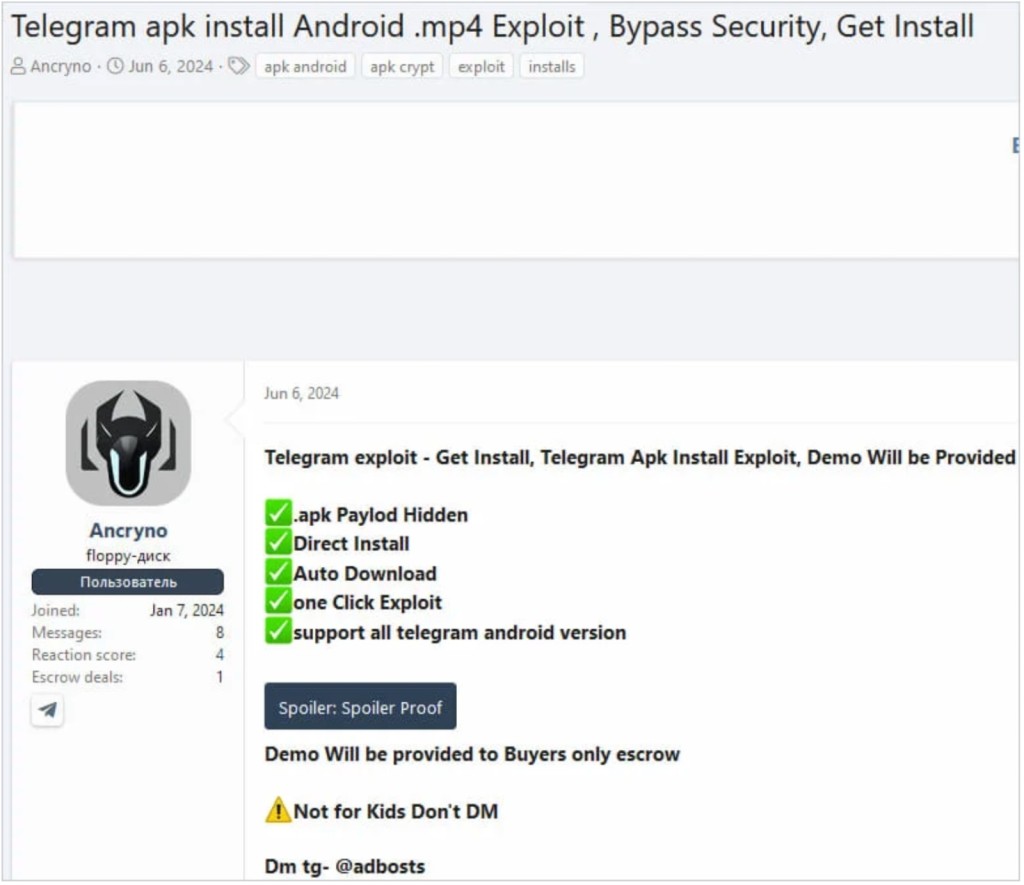
A cybercriminal was selling a Telegram zero-day exploit on a Russian-speaking hacking forum, ESET security researchers discovered. Dubbed EvilVideo, the flaw allowed attackers to send hidden malicious APK payloads that look like multimedia files via Android Telegram channels, groups, and chat in v10.14.4 and older.
The seller, under the name Ancryno, started the sale on June 6, 2024, and did not specify a price. The same hacker advertised an Android cryptor-as-a-service, reportedly fully undetectable.
After security experts reported it, Telegram released a fix for versions 10.14.5 and above on July 11. It now shows the shared file with its true APK extension.
Analyzing a sample from a ‘Proof of Concept’ on the forum, it appears trying to play the apparent video triggers a request to download an external app, which actually installs the malicious payload.
A threat actor could create a payload that displays an Android app as a multimedia preview and not as a binary attachment, appearing as a 30-second video once shared in chat. Security researchers believe cybercriminals could craft the specific payload using the Telegram API.
Telegram users who have left the default download option enabled trigger the automatic file download as soon as they open the conversation. The payload can also be downloaded manually via the button over the fake media file.
Trying to play the apparent video file shows an original Telegram error message suggesting that an external player be used to open the shared file.
Accepting will request to install a malicious app masquerading as an unknown external player, for which Telegram will ask for the user’s permission. The malicious app is downloaded as an apparent video file but with the .apk extension.
Security researchers have tested other Telegram environments, but the exploit only seems to work on Android.