Telegram Has Become a Tool for Hackers Who Deploy Malware to Websites
- Telegram’s versatility as a messaging app has attracted cybercriminals who use it for nefarious purposes.
- Hackers use Telegram's API to create bots that coordinate their criminal activities, which mainly consist of complex attacks on websites.
- The bots can send back alerts with real-time updates about the infected target.
Telegram, a messaging app renowned for its commitment to user privacy and security, has unfortunately become a haven for cybercriminals. Sucuri reported these malicious actors exploit the platform's strengths to target websites, turning this app into a useful tool for controlling malware-infected targets. Tracing these activities back to the perpetrators is difficult due to Telegram’s strong encryption and privacy policies.
This alarming trend underscores the urgent need for website owners to be aware of the potential threats posed by hackers using this app. Last year, the Sucuri research team found many malware infections coming from attackers using Telegram as infrastructure for their operations and cleaned over 11,000 malicious files from more than 290 of these infected websites.
Using Telegram’s API, cybercriminals can create bots that coordinate the attacks and are used for real-time alerts and monitoring, data exfiltration, command and control communications (C&C), and evasion.
The real-time notifications offer details about the status of the attackers’ malware. Updates about the infected site announce new data capture, successful additional malware implant, or even if an administrator interacts with the infected areas of the website.
Some of these bots are configured to exfiltrate stolen information (sensitive user details, login credentials, financial data) directly to the attacker’s Telegram account under the cover of Telegram’s speed and encryption. The app is used as a stealthier C&C server, as attackers can command their deployed malware via simple messages – even to initiate a denial-of-service attack.
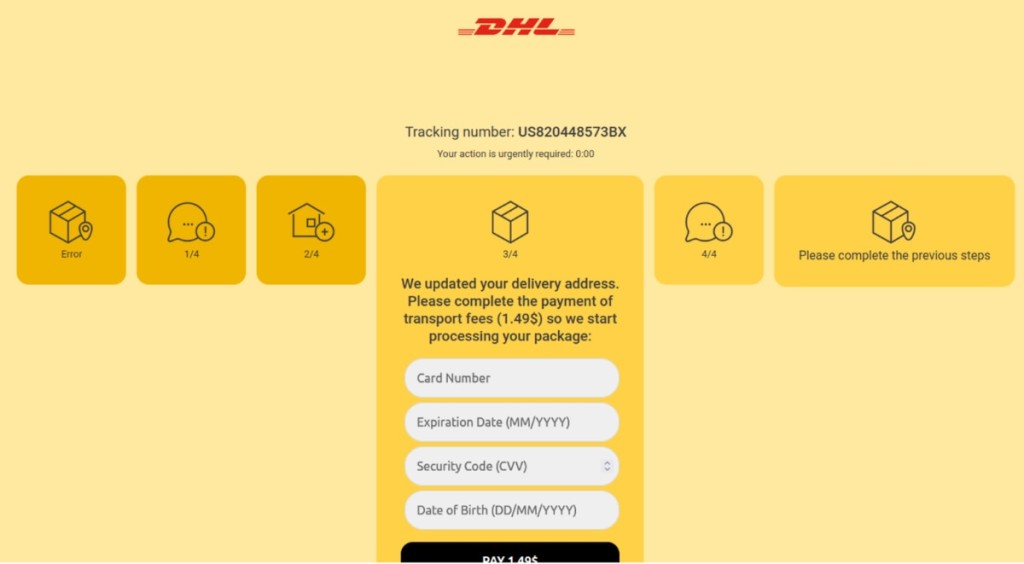
In a case study on phishing for credit card details via the Telegram API, which was used for data exfiltration due to its encrypted messaging, the researchers discovered a phishing page mimicking global courier service DHL, designed to look like a legitimate DHL tracking page.
The attackers used a JavaScript API call to check the visitor’s IP address for legitimacy. If the IP was legitimate, they asked the user to enter personal details and redirected the user to Google if it appeared suspicious.
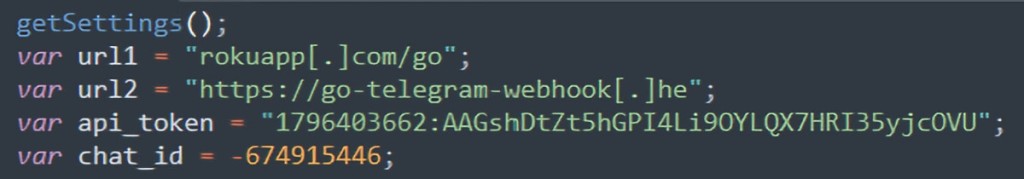
The Sucuri team highlighted the data exfiltration method that marks a sophisticated evolution in phishing techniques by allowing the attackers to leverage the legitimate Roku service to avoid detection.
JavaScript gathered any submitted data in the steps above, which was then sent to the Telegram bot via a Herokuapp-hosted service. A separate script defined the URL to send the data via AJAX and the API Token for a Telegram bot.