TeamViewer Zero-Day Flaw Exposes Windows Systems to Privilege Escalation
- A vulnerability in the TeamViewer Clients for Windows allows unauthorized command execution.
- The flaw concerns privilege escalation via argument injection due to improper neutralization of argument delimiters.
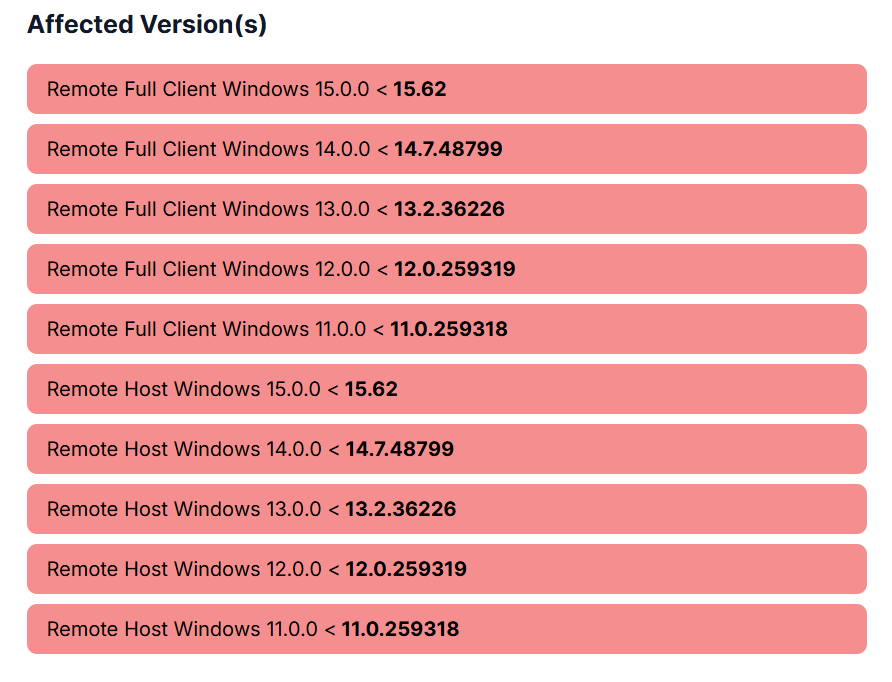
- Vulnerable versions are remote host and full client prior to 15.62, which can now be patched.
TeamViewer Clients for Windows is affected by a critical privilege escalation vulnerability that allows an attacker with local, unprivileged access to elevate their privileges, potentially granting them full control over affected systems.
Tracked as CVE-2025-0065, it affects versions prior to 15.62 and stems from improper handling of argument delimiters within the TeamViewer service component (TeamViewer_service.exe).
By crafting malicious input, an attacker can manipulate the service's execution environment, enabling them to execute unauthorized commands and bypass security restrictions. Successful exploitation could result in data breaches, system compromise, and operational disruptions.
Attackers could gain access to sensitive organizational data, customer records, and confidential files, and elevated privileges could give attackers complete control over the affected machine, potentially leading to further attacks within the network, including lateral movement.
Exploitation could disrupt TeamViewer services, impacting remote support and collaborative efforts, leading to downtime and reduced productivity. TeamViewer users are strongly advised to immediately update to version 15.62 or later to mitigate the risk of exploitation.
Organizations should prioritize patching systems running vulnerable versions of TeamViewer to prevent potential security breaches and maintain system integrity. Further monitoring of network activity for suspicious behavior is also recommended.
In July 2024, TeamViewer confirmed the Russian APT29 hacker group is behind its June 2024 corporate IT network breach, which reportedly managed to infiltrate the company’s corporate systems via stolen credentials.