“TeamTNT” Unleashed a New CryptoJacker Variant Called “Black-T”
- TeamTNT has developed a new cryptominer for Monero, targeting exposed Docker daemon APIs as usual.
- The miner features extensive scanning capabilities, and it could soon become a powerful worm.
- For now, “Black-T” remains in what seems like a testing phase, making insignificant amounts of money.
The group of hackers known as “TeamTNT” has reportedly authored a new cryptojacking variant called “Black-T,” which follows the traditional practice of targeting exposed Docker APIs. The particular malware comes with a specialization in network scanning, which indicates that the actors are looking to up their game in lateral movement and infection propagation. The discovery and the detailed report comes from Unit 42 researchers, who have been following TeamTNT’s operations for quite a while now.
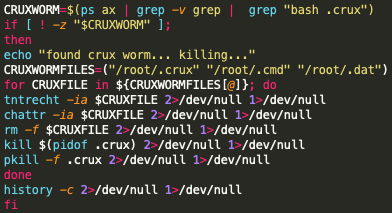
The infection starts with a cleaning phase, which is meant to free up system resources from other cryptominers and malware that may lie in the compromised system. “Black-T” is scanning for processes such as kswapd0, ntpd miner, redis-backup miner, auditd miner, migration miner, and finally, the Crux worm miner. After these are disabled, Black-T runs the XMRig process to prepare the system for XMR (Monero) mining.
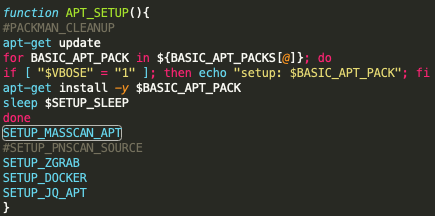
The next step for the malware is to fetch and activate its multiple scanners. There is ‘masscan’ for IP port scanning, ‘libpcap’ for network packet traffic listening, ‘pnscan’ for network scanning, ‘zgrab’ (zmap), and ‘jq’ (JSON processor).
Related: “Tor2Mine” Has Returned to Infecting Systems With Cryptominers
Unit 42 believes that the presence of all these tools is indicative of TeamTNT’s plan to incorporate more sophisticated features to this malware, like the ability to scan not only for bounce-able systems but also for specific vulnerabilities.
The new worm is now scanning port 5555, which is also something we’ve not seen before. One possible explanation is that Black-T could be adjusted to target Android devices in the future, but this remains a mystery for now.
Read More: New “Lemon_Duck” Cryptominer Is Testing the Linux Cloud Waters
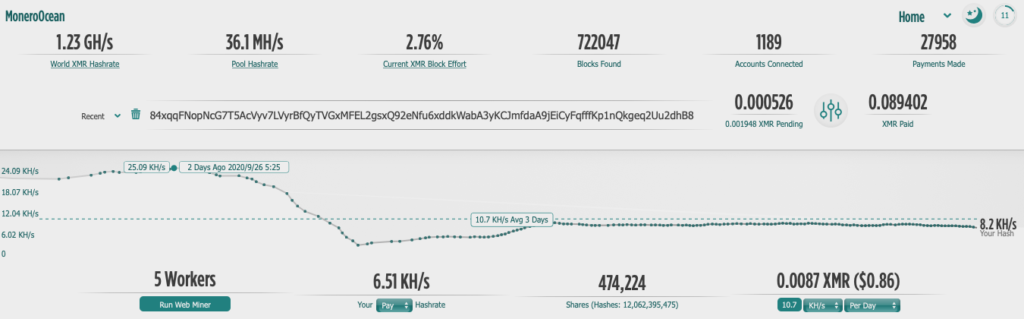
As for the detection rates of the payload that is downloaded by Black-T’s scripts, VirusTotal gives a score of 8/62, which means that the chances are in favor of the actors. The researchers have checked what the configured XMR wallet address has made thus far, and for now, the stats aren’t impressive.
Of course, only five workers are reported there, so we may still be in an early testing phase for Black-T, and all indications point to this scenario anyway.
If you’re administering cloud environments, make sure that there are no exposed Docker daemon APIs or any other network service that will serve as an entry point for TeamTNT. Also, advanced firewall and network security solutions should be able to catch excessive scanning operations like what we see on Black-T, so make sure to deploy whatever you can on that part.