Talos Says ‘Gamaredon’ May Be Something Bigger Than an APT
- The ‘Gamaredon’ group doesn’t appear to have a fixed targeting scope of motivation.
- The particular threat actor has maintained a global character for over seven years now.
- The infrastructure used by Gamaredon is extensive, far-reaching, and frequently refreshed.
Researchers of the Cisco Talos team have taken a deep look into the "Gamaredon" threat actor's operations and have concluded that this may not be an APT as it has been considered all these years. Being active since at least 2013, "Gamaredon" has a very wide targeting scope, covering the entire world. Also, it appears to be not as stealthy as other APT actors, apparently as a choice of operation and not due to a lack of skills.
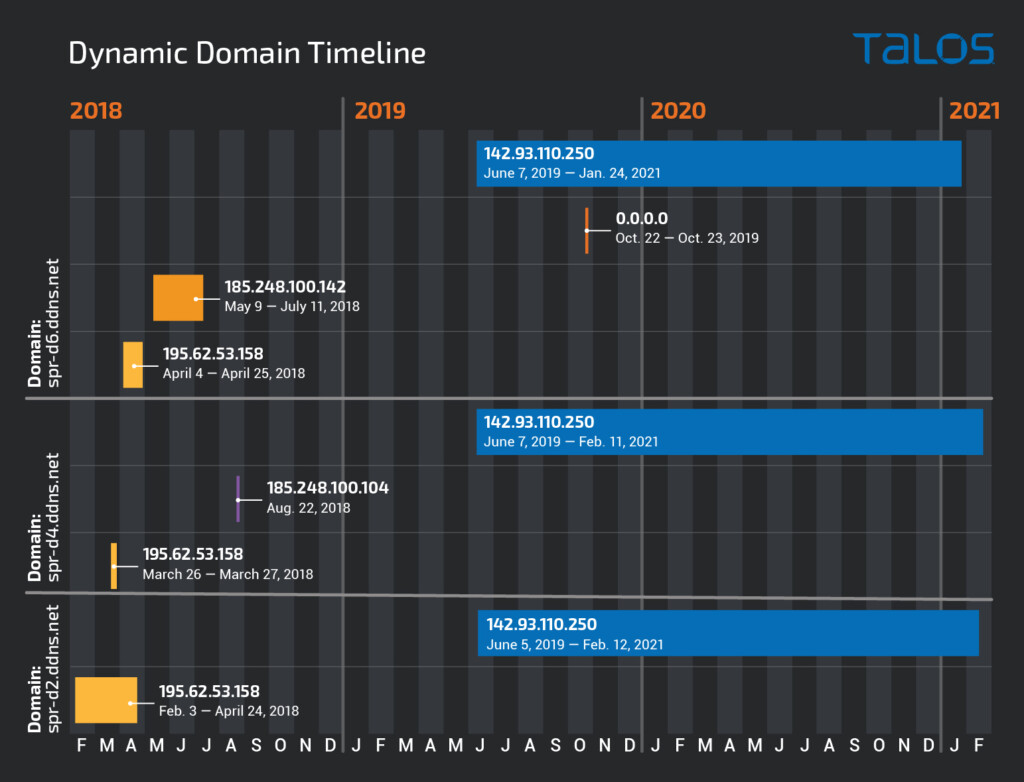
Talos has collected a rich set of data around Gamaredon’s operation all these years, seeing them launch their own attacks or support other APTs through a range of service provisions. The particular actor users trojanized app installers, self-extracting archives masqueraded as system files, spam emails with malicious attachments, and even template injection tricks. In terms of its C2 infrastructure, that’s pretty extensive, involving over six hundred active domains.
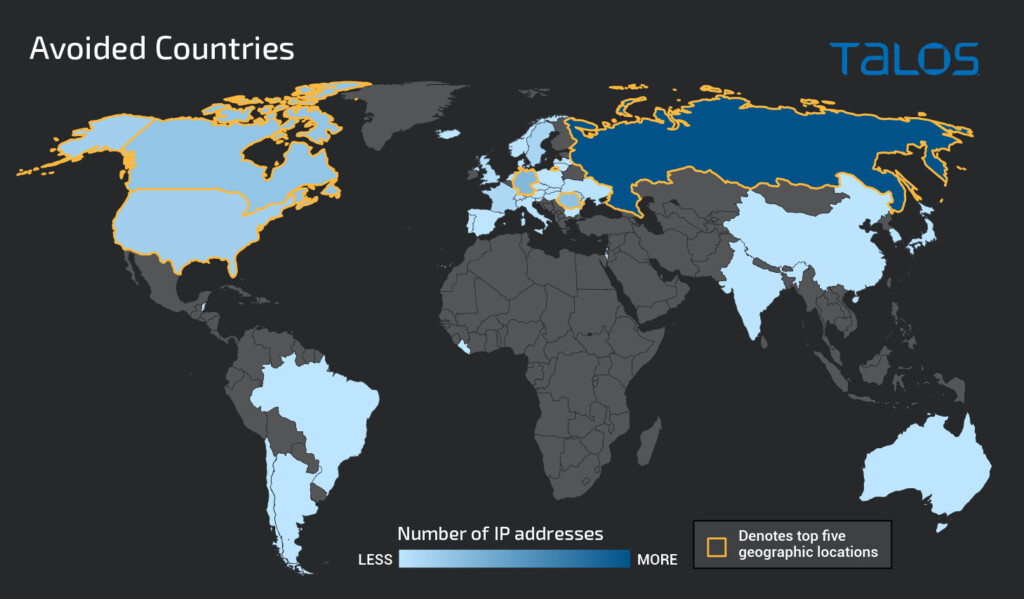
Gamaredon appears to have a constantly high-level activity relying on large-scale infrastructure. In one of the recently analyzed campaigns, the actor excluded 1,709 IP addresses from 43 different countries from first-stage infections.
The reason for this could be that the supported APT asked for the specific exclusion or that these IPs are Tor exit nodes, sinkholes, VPNs, etc. Excluding them indicates that the actor knows the far-reaching character of its malware distribution operations.
In general, Gamaredon appears to be more focused on Ukrainian targets, sending out large volumes of phishing emails that attempt to mimic government entities in the country. However, this doesn’t mean that other countries are safe from the group.
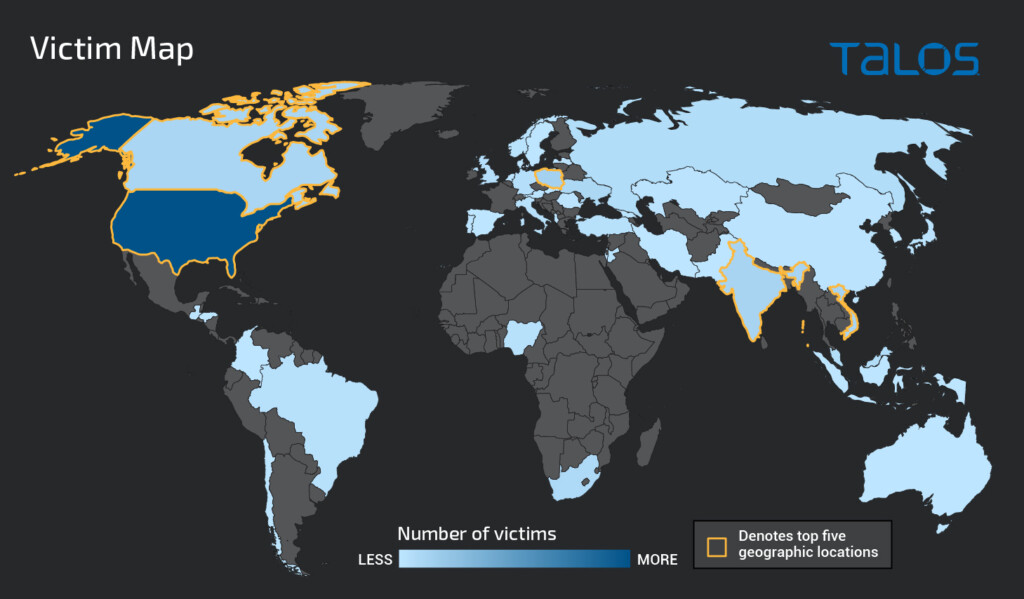
On the contrary, Gamaredon’s diversity makes it clear that this actor doesn’t have a specific political motivation or stable sponsorships. The following map shows the number of implants seeded on victims of Gamaredon since the start of the year.
Categorizing Gamaredon in a different space that breaks away from the APT classification is important for infosec researchers, as well as organizations looking to defend against cyber-threats. Understanding the subsistence and methodology of a group of actors is crucial in being able to stop it.
Gamaredon remains a very prolific actor that operates globally without winning many headlines precisely because it’s so multifaceted. It doesn’t tick all the boxes that would raise alarms, yet it remains a “powerhouse” working in the background.