Symantec Endpoint Protection Vulnerable to Self-Defense Bypassing Attacks
- Symantec’s Endpoint Security belongs to the big group of security apps that don’t validate DLL files.
- SafeBreach researchers have developed a proof of concept code that has numerous potential malicious uses.
- All versions prior to 14.2 RU2 are vulnerable, so users are urged to update their products immediately.
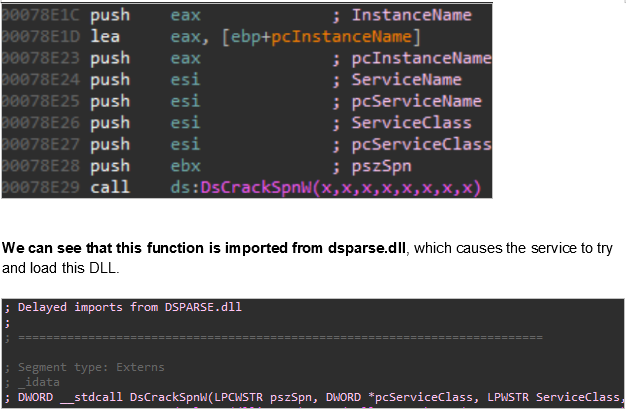
As we promised yesterday, today we are revealing another crucial vulnerability which plagues a product from a reputable vendor. This vendor is Symantec, and the affected product is Endpoint Protection. The flaw that was discovered by SafeBreach Labs, who was kind enough to share it with us beforehand, is given the identifier “CVE-2019-12758”. The vulnerability is again based on the loading of an arbitrary unsigned DLL into a process that is signed by Symantec and runs as NT Authority\System. The practical implications of this include defense evasion, threat persistence, and privilege escalation potential.
Symantec Endpoint Protection is a security software suite that is deployed in many high-risk environments, helping administrators set up intrusion-prevention systems. It also provides firewall features that can help keep dangers outside server farms or desktop computers. The particular product is the most popular endpoint security solution out there, so we’re talking about a vulnerability that affects many thousands. As was the case with other security products that we discussed in the recent past, the Symantec Endpoint Protection software is running a signed process as NT Authority\System, trying to load a specific DLL file without any validation.
The SafeBreach team has developed a PoC (proof of concept) in the form of a 32-bit proxy DLL which can write the required filename, username, and parent process name, essentially turning Symantec’s software into a persistent threat for the victim. This is because an actor could execute any code they would like through the unsigned DLL, and have it run at maximum system privileges, completely bypassing the self-defense mechanism of the product. The root cause for this is again, the absence of any form of digital signature validation for the DLL file.
SafeBreach reported the discovered vulnerability to Symantec on August 5, 2019, which the security company confirmed only a day after. Working on the release of a fix, however, took quite a while, with the fix finally arriving through a patch today. The affected versions are all going from 14.2 RU2 and older, so if you are running a vulnerable version you should update immediately. On that note, it is important to clarify that for the particular attack to work, the actor would need to have administrator privileges in the first place.
Do you have something to comment on the above? Feel free to share your thoughts with us in the section down below, or join the discussion on our socials, on Facebook and Twitter.