A Set of Bluetooth Flaws Named “SweynTooth” Affects Hundreds of Devices (Updated)
- Researchers found 11 critical vulnerabilities that can lead to severe Bluetooth attacks.
- The attacks could crash the target device, force boot loops, or straight out take it over.
- Consumers are advised to be vigilant and apply any available updates immediately.
Researchers from the Singapore University of Technology and Design have discovered a collection of vulnerabilities that underpin Bluetooth Low Energy (BLE) systems. Calling the set of the 11 flaws “SweynTooth”, they warn about the extent of its affection as it is to be found across various BLE SDKs used by at least six SoC (system on a chip) vendors. This means that the list of the devices that are vulnerable to SweynTooth contains at least five hundred entries. The flaws with their identifiers are given below:
- CVE-2019-16336 and CVE-2019-17519 – Link Layer Length Overflow
- CVE-2019-17061 and CVE-2019-17060 – Link Layer LLID Deadlock
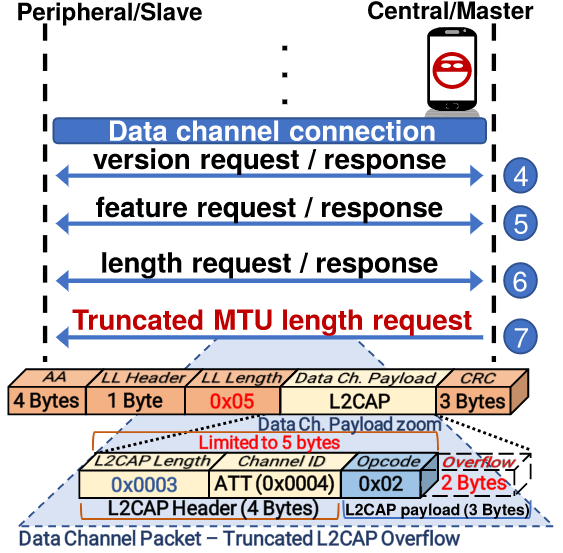
- CVE-2019-17517 – Truncated L2CAP
- CVE-2019-17518 – Silent Length Overflow
- CVE-2019-19195 – Invalid Connection Request
- CVE-2019-17520 – Unexpected Public Key Crash
- CVE-2019-19192 – Sequential ATT Deadlock
- CVE-2019-19195 – Invalid L2CAP Fragment
- CVE-2019-19196 – Key Size Overflow
Sequential ATT Deadlock Diagram, Source: ASSET Research Group
The above enables an attacker to crash a device by triggering a series of faults via memory corruption, create deadlocks in the SDK firmware which would force the device to endlessly reboot, and bypass security measures. This last one is the most critical of all, as an attacker in Bluetooth range could pair with a device without authorization, and without the owner realizing it. The vendors who are vulnerable to crashing flaws are Cypress, NXP, Dialog Semiconductors, Texas Instruments, Microchip, and Telink Semiconductor. Those susceptible to deadlocks are Cypress NXP, Texas Instruments, and STMicroelectronics. As for the security bypassing, the only vendor plagued by this is Telink Semiconductor.
This creates a big problem for users of wearables, smart home IoT devices, and even security/surveillance systems. Examples of products that are using the vulnerable SoCs are the Fitbit Inspire range, the Eve Systems, the CubiTag Bluetooth tracker, and the eGee Touch smart lock. Unfortunately, medical products from VivaCheck Laboratories, Medtronic Inc., and others, are also vulnerable. The researchers are demonstrating how they manage to crash a Fitbit Inspire fitness tracker and deadlock a CubiTag in the following video.
So, the question now is, what can the users do to protect themselves from Sweyntooth? Unfortunately, not much other than wait for your product manufacturer to push updates that incorporate the fixing patches that were released by the SoC vendors. Cypress, NXP, Texas Instruments, and Telink, have already released their fixes, but it will take a while to reach the consumers. Even worse, Dialog, Microchip, and STMicroelectronics haven’t released a fixing patch yet. The only way to stay safe for sure is to disable Bluetooth when you’re in places where there are other people in your range.
Update 17/02: The mention of "Syqe Medical Ltd." has been removed from the article as the company has contacted us to inform about an inaccuracy in the researchers' report. While they have secured a license to use BLE technology on their "Inhaler v01" product, the BLE technology has not been enabled. Thus, their products are not vulnerable to SweynTooth attacks.