A Super Mario Image Targets Italians with Ransomware and Malware
- An Excel file that comes as an attachment on a fake payment mail wants to run a macro to check if you’re Italian.
- If you are, it downloads a Super Mario image that in turn downloads the Gandcrab ransomware.
- This is one rare case of combining document macros, steganography, and ransomware deliverance.
A Bromium researcher has discovered a new campaign that utilizes steganography to deliver various pieces of malware and ransomware to Italians. Although common as a form of attack, the hidden code inside images that are lightheartedly opened by unsuspected victims are becoming increasingly trendy, as they can also avoid detection by the various anti-malware, firewall, and anti-virus solutions out there.
The particular campaign initiates the attack by sending an email that is posing as a payment notice for the victim. The recipients receive an MS Excel attachment with the email, with the file containing macros, so they are urged to enable them in their office suite. This should be a first sign that something is not right, as the functionality of macros allows for arbitrary code execution. Those who are tricked in opening the file and enabling the macros function in their suite will enable the script to check whether the computer is using the Italy region or not. If the victim is located in Italy, a Mario image is downloaded. If not, nothing else happens.
source: Bromium blog
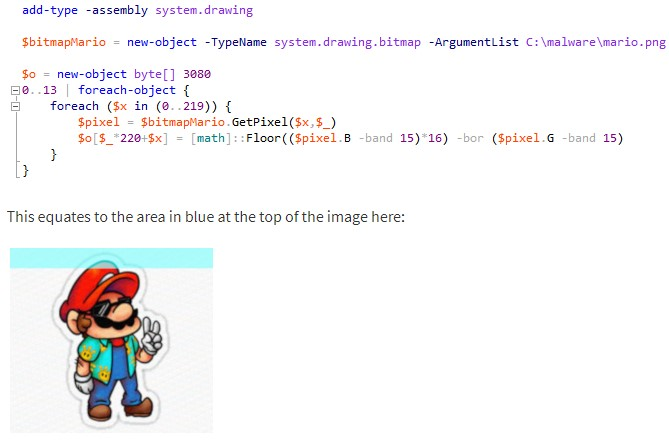
That image contains malicious PowerShell code in the blue and green channels, so when the victim opens it, the code runs to download various kinds of malware and ransomware such as the GandCrab. The PowerShell code is obfuscated by base64 encoding, so Bromium researchers had to go through multiple steps of multi-layer manual deobfuscation to finally download various samples of the Super Mario payloads through an Italy-based VPN. The samples at the time were mostly the widely popular Gandcrab ransomware, but this can be changed in the future.
To stay protected against this type of attacks,
a.) always have the macros function on your office suite disabled by default,
b.) do not download and open email attachments from people that you don’t know,
c.) always check the image size before opening it to try and figure out how likely it is to have hidden code considering its file type and resolution.
For more technical details, and a list of the indicators of compromise, check out Bromium’s report.
Have you received the Super Mario image Excel file? Let us know of your experience in the comments section below, and don’t forget that you can help us warn more people of this campaign by sharing this story on the socials. For this, visit our online communities on Twitter and Facebook.