The “SunCrypt” Ransomware Group Is Now Partnering With DDoS Teams
- The SunCrypt gang, newcomers in the ransomware field, are deploying new tactics against victims.
- Those who ignore them and don’t negotiate the payment of ransoms are getting DDoSed by affiliates.
- This is added on top of the now typical data sample leakage that is meant to raise the heat of the extortion.
According to the latest reports, SunCrypt is now employing DDoS methods against its victims through affiliates. This form of vengeance strikes those who refuse to negotiate the requested ransom’s payment, followed by filesystem lockdown due to a ransomware attack.
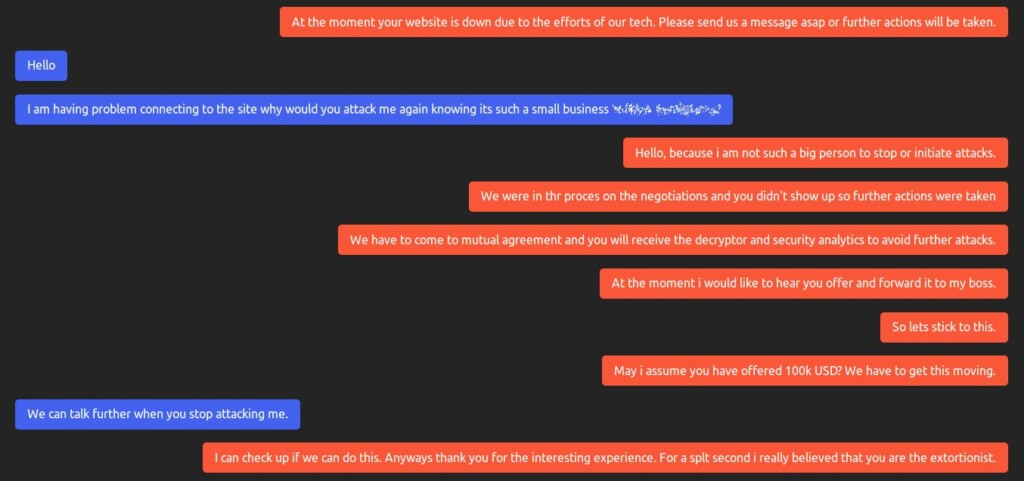
Usually, groups like SunCrypt leak samples of stolen files online as a form of extortion and additional pressure, but there are many times when this is simply not enough. In these cases, distributed denial of service (DDoS) could serve the hackers as an additional convincing factor for the victim to pay them.
It sounds like a game-changer, and it really is since this method cannot remain exclusive to the SunCrypt group, at least not for long. Ransomware actors are making so much money today that paying other teams of hackers to launch persistent and high-volume DDoS attacks against their victims for extended periods of time would be something they can easily support.
The smaller the target is, the higher the chances of managing to cripple their systems and bring their services down. Here’s a real example that was publicly shared by the “MalwareHunterTeam.”
SunCrypt is a new ransomware group operating under Maze's guidance but keeping an independent activity from the Russian RaaS. Whatever new methods we see in SunCrypt now, we may start seeing them in Maze operations soon, and that would be a total catastrophe for victims. There are entities with backups for restoring and secured their most sensitive files adequately so that hackers hold nothing good enough for extortion, but even they will have to consider negotiating with the actors now.
While it looks like ransomware actors are drawing all the aces here, some drawbacks come with this sheer power. The more these groups have to coordinate their activities with other teams, the more traces they leave behind, so the chances of the law enforcement authorities managing to track them down and convict them increase. Not by much, but definitely more than nothing.