Subaru Starlink Vulnerability Allowed Remote Car Access and Location Tracking
- Subaru patched a flaw in its Starlink system that permitted an unauthorized party to access precise car location tracking data and logs.
- The vulnerability could have permitted remote takeover of key vehicle features like ignition, door unlocking, and more.
- The Starlink employee web portal password-reset function could be exploited due to bypassable client-side-executed security questions.
A significant cybersecurity flaw in Subaru's Starlink connected vehicle service has been recently uncovered. It enabled unauthorized access to all the vehicles, customer accounts, vital car controls and granular location histories of millions of Subaru vehicles.
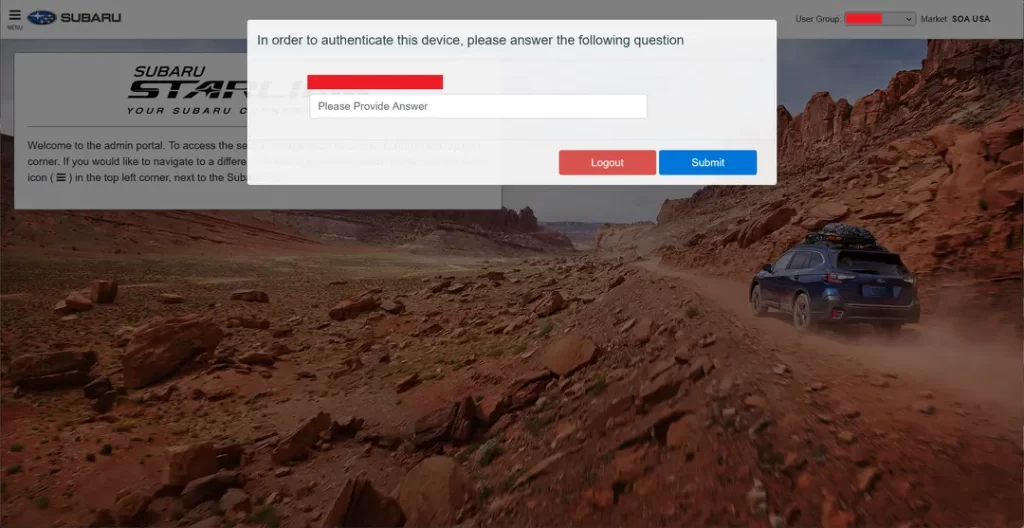
The issue was addressed soon following ethical hackers Sam Curry and Shubham Shah’s discovery. The researchers found a series of flaws in Subaru’s Starlink web portal, intended for employee use. Subaru's employee-focused domain, SubaruCS.com, presented multiple systemic failures.
These vulnerabilities allowed them to take control of key vehicle features remotely, including unlocking doors, honking horns, starting ignitions, and even accessing fine-grained location histories dating back over a year.
According to Curry, the location tracking data was precise enough to reveal highly sensitive details, including stops at homes, workplaces, or even parking spots at frequented locations like churches or medical offices. This exposed users to serious privacy and safety issues.
By locating employee email addresses on platforms like LinkedIn, the researchers exploited a password-reset function with bypassable security questions executed on the client side rather than server-side validation.
Using this method, the team accessed employee accounts, enabling them to remotely manage vehicle settings and access location data via Subaru’s backend systems.
These risks extend beyond Subaru, as the researchers noted similar vulnerabilities in the web interfaces of over a dozen carmakers, including Honda, Hyundai, Toyota, and Nissan.
Subaru has clarified that its employees, under specific roles, retain access to location histories for operational purposes, such as assisting first responders during emergencies. However, the ability to access up to a year of detailed location history raises questions about the privacy safeguards.
Subaru has stated that the vulnerability was "immediately closed" after notification in November and emphasized that no customer data was accessed without authorization.
In a public statement, Subaru noted, “There are employees at Subaru of America, based on their job relevancy, who can access location data. These systems have security monitoring solutions in place that are continually evolving to meet modern cyber threats.”
Curry countered Subaru’s statement on first-responder usage, pointing out that such scenarios wouldn't require extensive historical data access. Subaru has not disclosed how far back customer location history is logged.
This level of overreach demonstrates a broader issue in the automobile industry, where connected vehicles are becoming data-collection hubs with insufficient privacy protections. Recent reports warn that automakers often grant themselves extensive rights to collect, share, and monetize user data, leaving customers with little control or transparency.