Study Shows That 27% of Security Breaches Are Due to Unpatched Vulnerabilities
- 27% of organizations suffer data breaches due to irregular patching schedule.
- 11% of them don’t have the capacity to detect new hardware or software on their network.
- 12% of organizations do not run any vulnerability scans ever.
According to the findings of the Verizon Enterprise Data Breach Investigations Report, a large portion of data breaches that were sustained by organizations could have been avoided if the system administrators applied the required patches by simply updating. Crooks like to exploit vulnerabilities because they are released with useful details like their specific location and scope of affection, and very often with proof-of-concept (PoC) code as well. This is a double-edged sword as PoC code convinces the developers of the validity of the security flaw report and helps them fix it quickly, but also spreads a weapon out there that often arms malicious actors.
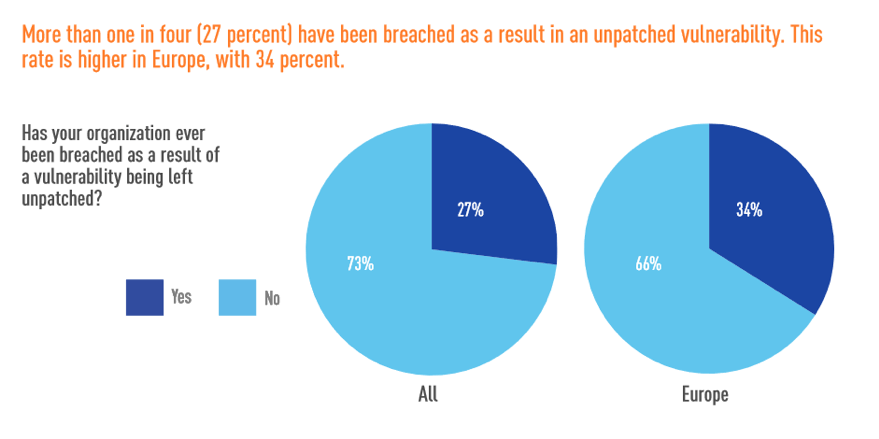
This study has led Tripwire to investigate the problem further, so they organized a recent survey where they found that 27% of organizations suffered a data breach that was a direct result of an unpatched vulnerability, while the percentage for European organizations goes up to 34%. In addition to this, the survey found that 21% of the organizations that participated in the survey required a couple of days only to detect newly connect devices on their network. Another 10% needed a whole month to discover these devices, while a whopping 11% doesn’t even have the capacity to detect new hardware or software connected to their infrastructure.
Image source: tripwire.com
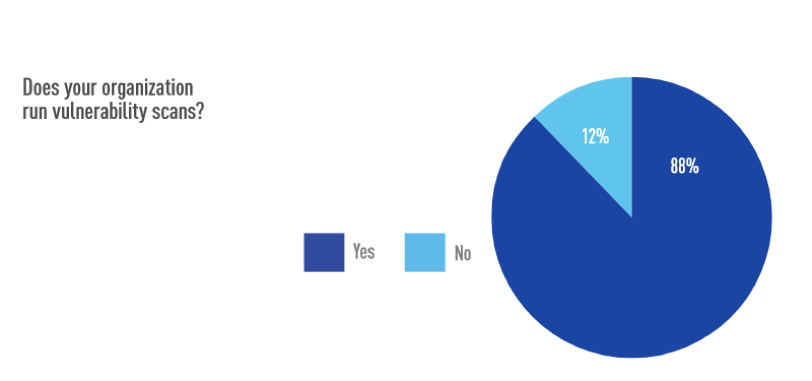
These percentages are characteristic of the lack of a robust vulnerability management plan, a tactic that usually results in breaches. Even for those that do have a plan in place, they allocate enough resources only to deal with high-severity vulnerabilities. 16% of the survey respondents said that whatever vulnerability management plan was applied in their organization was merely there to meet compliance with some form of a policy or standard. Finally, 12% of IT security professionals working for the participating organizations revealed that they run no vulnerability scans at all.
Image source: tripwire.com
In this day and age, organizations should be fully aware of the dangers and business risks of not patching and not following an effective vulnerability management plan. Still, we see inexplicably high numbers of organizations that choose to do nothing at all on that part, while an even larger percentage is doing the minimum, only for compliance purposes. It is no wonder how we’re still seeing data breaches within organizations that don’t get disclosed even after years, as many of them don’t even have the ability to detect that something bad has happened on their network.
Care to share your opinion on the above? Feel free to do so in the comments down below, and also on our socials, on Facebook and Twitter.