New ‘StrandHogg’ Android Vulnerability Being Under Active Exploitation
- StrandHogg is a new malware for the Android platform, which can operate as powerful spyware.
- The malware is tricking the user with permission requests that are made to look like they come from elsewhere.
- The activity of the malware can go unnoticed, and Google hasn’t patched the Android vulnerability yet.
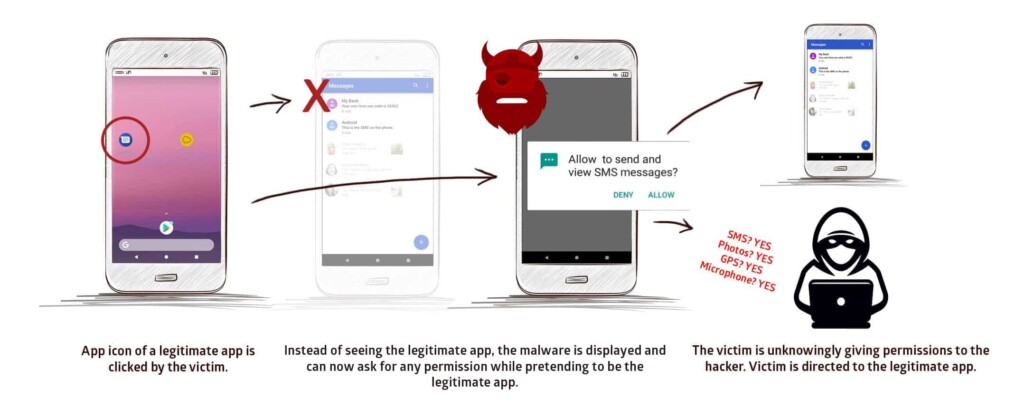
Researchers from Promon Security warn the public about a newly discovered vulnerability that affects all versions of Android (including the latest 10), and which is currently under exploitation in the wild. Dubbed as “StrandHogg”, this flaw allows the attacker to create a malware that poses as a legitimate app, asking the user for the granting of any permissions the actor wants. For this exploitation to work, there is no need for the target device to be rooted (unlocked bootloader). The researchers have already identified 36 malicious applications that are based on the StrandHogg.
The flaw is in Android’s ‘taskAffinity’ setting which allows an app to assume any identity it wants in the multitasking system. In the case of StrandHogg, the malware is faking the identity of legitimate apps that the user trusts. When the user clicks on the app icon to launch it, the malware is pushing permission granting requests, making it look like it is the legitimate app that’s asking for it. The user grants the permissions, and the malware is being empowered to access data, activate the microphone, read SMS, track the location of the victim via GPS, and everything else that you can see in the following video.
As demonstrated above, fully-fledged phishing attacks and the taking over of accounts protected by two-factor authentication systems are also perfectly possible. All of these exploitation case scenarios can take place without the victim realizing that something is off until it’s too late. If the attacker prefers it, they may also use the malware purely as persistent spyware, and eavesdrop the target device for extended periods of time. All that said, the question now is how to stay safe from this new threat.
Source: Promon
First of all, Google hasn’t patched the vulnerability yet, so it all boils down to what apps you’re using. The researchers have found that Google Play is currently free of droppers of the particular malware, but malicious actors are continually trying to upload their nasty apps there. In their tests, the researchers found out that the CamScanner app (PDF creator) contains the particular module. This is just an example of a StrandHogg app that can be downloaded from outside the Play Store, and which people have installed more than a hundred million times already. That said, you should avoid any APK sources outside the official app store, and you should also use a mobile security solution from a reputable vendor.
Have you had any experience with StrandHogg? Share the details with us in the comments down below, or on our socials, on Facebook and Twitter.