Steam Phishing on the Rise Again Targeting In-Game Item Collectors
- Scammers are stealing precious Steam accounts and sell their items online.
- To grab the credentials, they are using well-made phishing webpages that look like the real thing.
- The verification and two-factor authentication are done via the genuine Steam Guard service.
According to a report by Kaspersky, scammers who lurk Steam and try to grab the credentials of prolific users are on the rise right now. As explained, the whole point of phishing the credentials of users isn’t to play a game for free, nor to sell the accounts to others. The primary goal this time is to sell the hard-earned in-game items that belong to the legitimate user for real money. After a player is stripped from all in-game items that are worth something, the scammer moves on to their next target, and so it goes.
As it becomes evident from the graph below, this type of attack have started to spike during the summertime and the activity continues. The first step for the fraudsters is to lure Steam users to websites that look like legitimate stores that sell in-game items. The phishing sites are created with meticulous care and are pretty hard to distinguish from real ones. They even feature HTTPS and a valid security certificate, so no red flags are raised. Once the visitor gets lured by an item that is for sale at a relatively low price, they are asked to enter their Steam account credentials in order to pay for their purchase. Alternatively, they may use their Facebook and Google accounts (if linked).
Source: Secure List
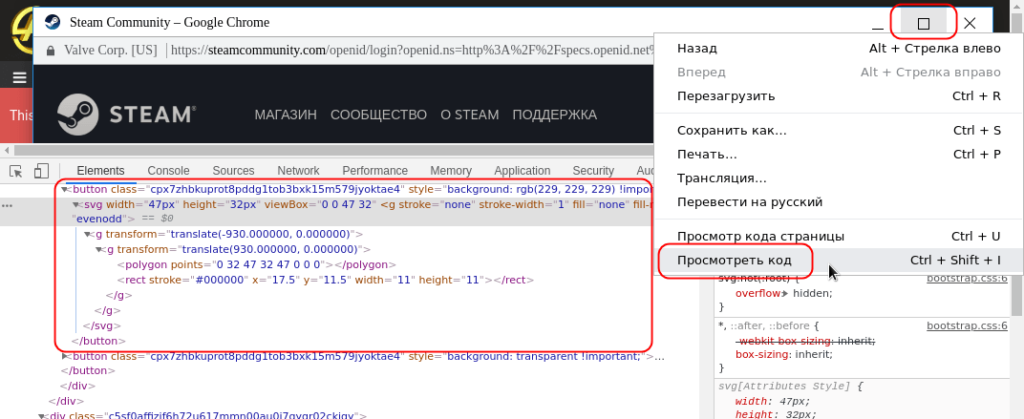
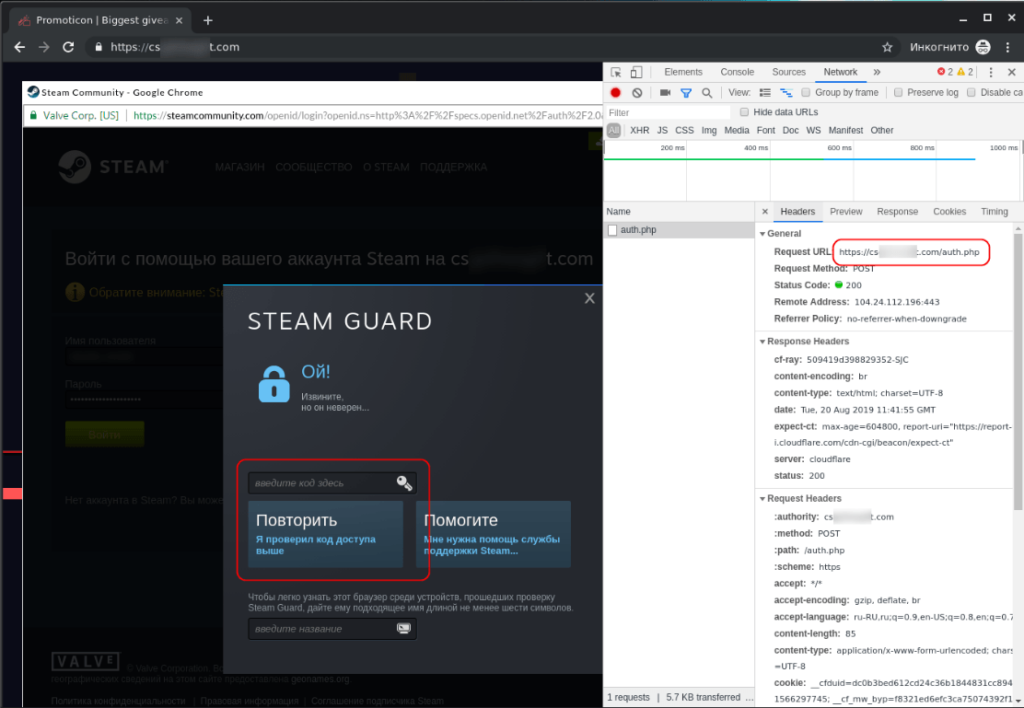
The fake login form that pops up is actually linked with the legitimate Steam services for verification, so if the victim enters the wrong password by mistake they will be shown an error message. Moreover, there’s a language interface that supports the page’s adaptive layout, convincing the victim further into the swindle. The username and password that are entered are transferred using the POST method through an API that is on a domain that is controlled by the actors. When a two-factor authorization step is involved, the code is generated by the actual Steam Guard app, which is forwarded to the scammers.
Source: Secure List
If you’re an item collector on Steam, be very careful with phishing pages, re-directions, and popup windows. When you’re met with a login form, take a step back and look at the URL. Using “WHOIS” to check a domain when you’re suspicious shouldn’t be a far-fetched option either. In the end, remember, if you log in on the actual Steam platform, you should stay logged on any user store. If you maintain a Steam tab where you’re logged in, refreshing the shop’s page should recognize you automatically if it’s legitimate.
Have you ever fallen victim to a Steam phishing campaign? Share the details with us in the comments section down below, or on our socials, on Facebook and Twitter.