Stealing Grindr Accounts Was a Matter of Knowing the Email Address
- Grindr was plagued by a nasty account takeover bug whose exploit was simple and very effective.
- All that would be needed by the attacker is to know the email address of the target account.
- The flaw has been fixed now, although Grindr demonstrated incompetence in dealing with bug reports.
A severe security flaw in Grindr would allow anyone with a valid user email address to reset the password and take over the account. This was discovered by security researcher Wassime Bouimadaghene, who reported the flaw to the app developers but was initially ignored. He then reached out to Troy Hunt of Have I Been Pwned, who managed to eventually find someone working on Grindr’s security team and pass them the exploit process’s details.
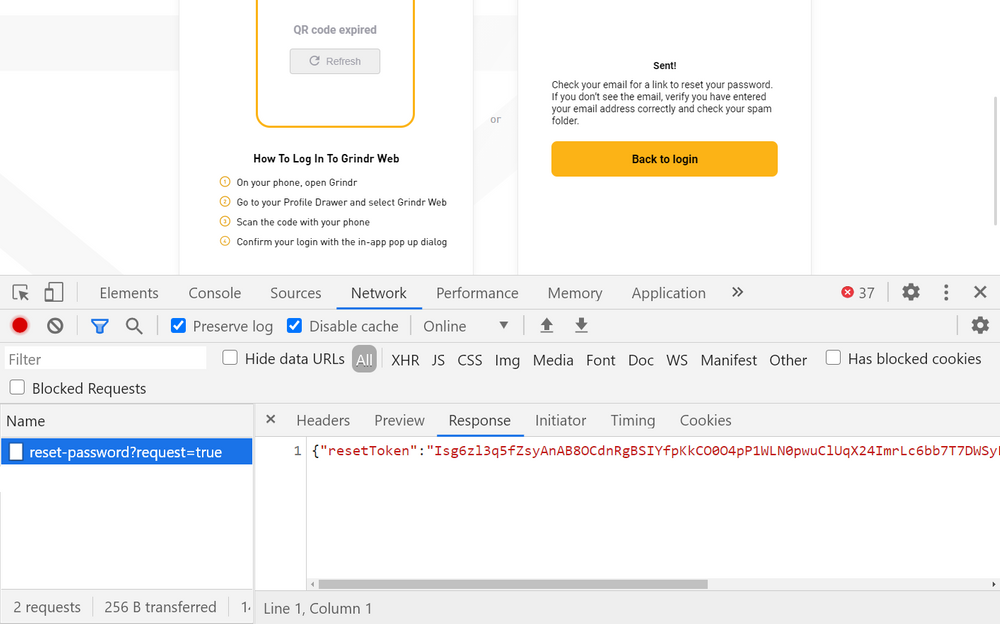
The attack begins with the actor using the target’s email address and going to the Grindr’s password reset page. There, a Captcha is served and solved, and the email with a reset link is sent to the owner. At this point, the attacker can open the dev tools on the browser and grab a valid reset token from right there. By copying and pasting the URL on a new tab, the actor could set a new password for that account, all happening quickly and without any other protection steps like 2FA, for example, standing in the way.
Knowing the email address and now the password, too, means that the actor can log in to another person’s Grindr account, as simple as that. There are no limits of any kind once this happens, as we’re talking about full account takeover. All information, media, and the ability to communicate with other users on the platform are available to the infiltrator as if he were the account holder.
Considering the nature of Grindr, this is extremely bad for its users. Since Grindr is a location-based social networking and online dating application focused on gay, bi, trans, and queer people, these are categories of people have to deal with social stigmatization, marginalization, bullying, racism, and unfair treatment at work or even by the authorities. Thus, exposing their interactions or sensitive personal details would induce dire consequences for them.
Read More: Half a Million ‘Activision’ Accounts May Have Been Hacked, but There’s No Breach
It took Grindr an unjustifiably long time to respond to Wassime’s report, and even Hunt’s messages, but at least they fixed the flaw almost immediately once they realized their blunder.
As Grindr’s chief operating officer Rick Marini told TechCrunch: