Stealing DNA Sequencing Data Via Smartphone Microphones
- Researchers show that it’s possible for someone to eavesdrop DNA sequencing data.
- All that you would need is a hacked phone near the machine and the model’s sound profile.
- The damage from this type of side-channel attacks could reach unheard scales.
Every now and then we stumble upon a report or a study that approaches a simple yet not at all simplistic problem, like stealing DNA sequencing data by taking advantage of microphone activation vulnerabilities on smartphones for example. Side channel attacks are nowadays possible in ways that go beyond our casual perception, as technology is so interwoven in our everyday lives that we often forget what is feasible, and what is possible is automatically probable. Researchers at the University of California have reminded us of this fact by demonstrating that snooping on DNA synthesizers and figuring out what blocks it’s building is entirely possible.
From the researchers' paper
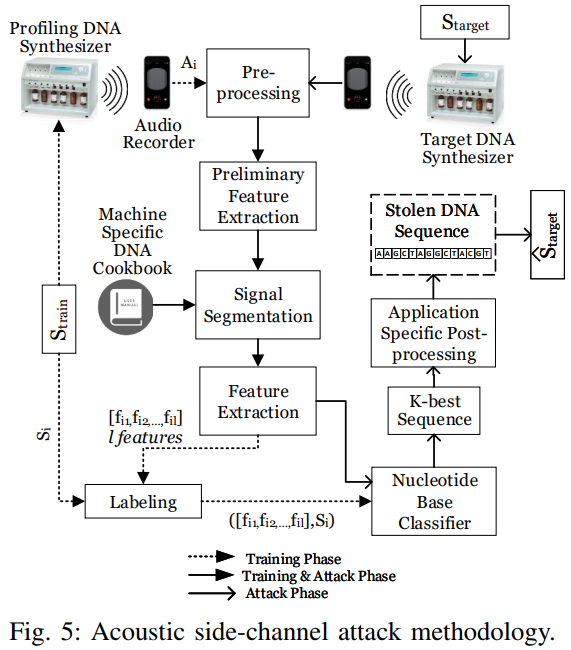
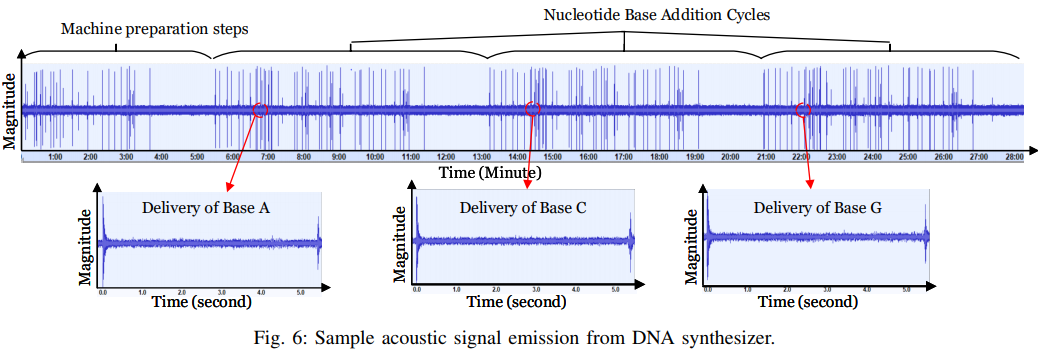
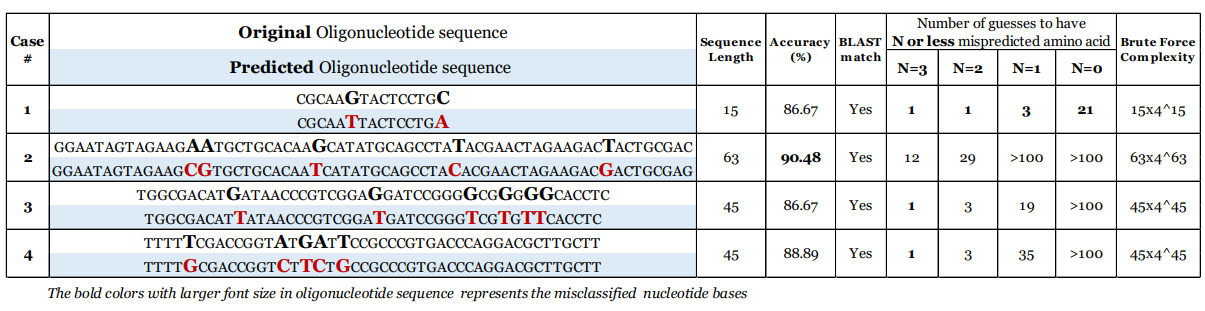
The engineers have tested various widely used bio-synthesizer machines from different manufacturers, and based on the sound they make during operation, they were able to guess the DNA sequencing with an average accuracy level of 88.07%. The experiment was based on the capturing of the acoustic waves produced by the machines, their pre-processing (high-pass filtering), removal of background noise, signal segmentation (based on the machine's profiling), extraction, classification, and sequence reproduction. The team has tested various experimental configurations and figured that the maximum distance to the machine in order to generate adequately reliable results is 0.7 meters.
From the researchers' paper
The possible eavesdropping could come from an employee who has reasons to do it, a visitor of a DNA synthesis lab, or just a hacked smartphone that sits in the pocket of an employee or a table nearby the machine. As we have seen before, turning on the microphone on a smartphone without asking for user validation or displaying a relevant indicator icon on the phone’s screen is possible, so your phone could be listening without you knowing about it. If you’re working in a medical facility where DNA sequencing is considered an invaluable piece of information, competing companies or even foreign governments could sponsor hackers to gain access to your phone’s microphone.
From the researchers' paper
The obvious way to defend against this would be to develop more silent bio-engineering machines or add another source of sound in the lab to mix things up and make profiling impossible. However, as technology advances and wave detection and recognition algorithms get smarter, it will get harder and harder to keep a side channel attack surface within manageable constraints. For now, dampening those DNA sequencing machine pipes would be the safe thing to do.
Have any comments to share on the story? Feel free to do so in the comments section down below, or on our socials, on Facebook and Twitter.