State-Supported Actors Use Coin Miners to Stay Hidden
- A group of Vietnamese hackers is planting Monero miners to create a false idea about the intrusion.
- IT teams are more likely to think of a botnet infection than an attack from a sophisticated actor.
- The attacks end up being complicated, persistent, and multi-level, so reducing the surface is the best defense.
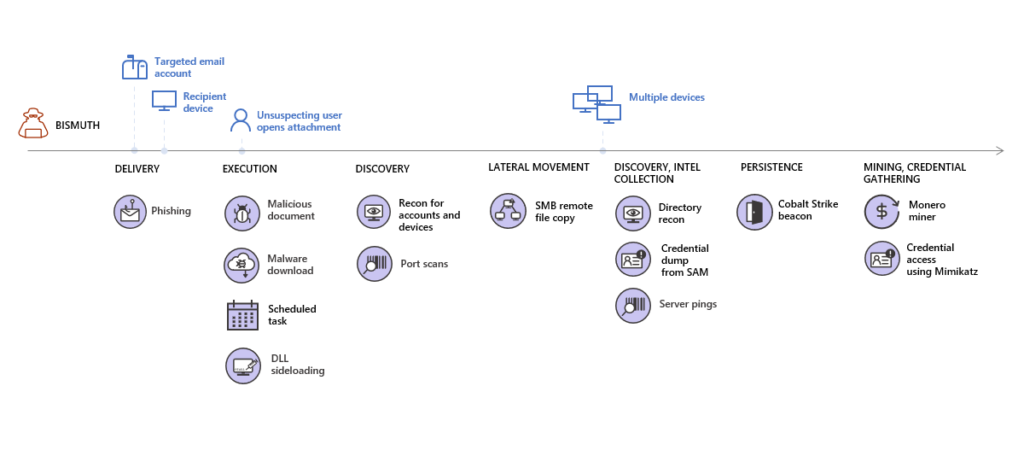
A state-backed actor operating at a sophisticated level was “caught” using coin mining techniques to fly under the radar while collecting sensitive information from compromised networks. The discovery and detailed report come from researchers of the Microsoft Threat Intelligence team, and the actor has been identified as “Bismuth,” sharing similarities with “OceanLotus” (APT32). This is a Vietnam-based group of actors who were previously confirmed to be behind cyber-attacks against BMW and Hyundai.
Microsoft reports that between July and August 2020, the group started deploying Monero coin miners in attacks against government institutions and private entities in France and Vietnam. In their home country, the actors targeted mainly human and civil rights organizations, which are considered a threat to the local regime.
The attack chain starts with phishing emails carrying macros that download malware. This, in turn, sets up a scheduled task and performs DLL sideloading. Through port scans and credential-stealing, the actors move laterally in the compromised network, collect intelligence and exfiltrate it. Their toolset includes Mimikatz and Cobalt Strike, as we’ve seen in the attacks against the auto-makers, but the Monero miner is a new element.
The miner is registered as a service that resembles a common Virtual Machine process, attempting to hide it in plain sight. Each miner pointed to a unique wallet address loaded with crypto, but this is just a distraction from the real goal of stealing user credentials through Mimikatz. So essentially, “Bismuth” increases the complexity of the response and uses the Monero miners not for profit but for overwhelming the targets and diverting their attention.
Typically, when IT teams discover crypto miners, they don’t suspect that a sophisticated actor has broken their perimeter. They will assume that they’re dealing with an unsophisticated botnet infection or the deployment of commodity malware planted by low-level crooks. This is precisely what Bismuth wants to inspire and the reason why they’re using Monero in their campaigns.
Microsoft suggests that you take attack surface-limiting measures, build credential hygiene, and turn on cloud and tamper protection features to stay safe from all that. Moreover, monitoring event logs and looking for clearing actions should indicate this type of threat. If you discover ID 1102, or ID 4624 alerts, you should investigate further, focusing on the abuse of highly privileged accounts on your network.