Stanadyne’s “PurePower Technologies” Hit by the Conti Ransomware Group
- “PurePower Technologies,” a Stanadyne company, has been hit by the Conti ransomware gang.
- The actors appear to have stolen several sensitive documents and are already leaking some online.
- For now, PurePower Technologies hasn’t announced anything concerning a data breach.
The notorious ransomware group that goes by the name ‘Conti’ has claimed yet another high-profile victim that engages in the engineering and technology field, "PurePower Technologies." The South Carolina-based company, which is part of Stanadyne, is a leader in the engineering and remanufacturing of air and fuel management components for OEMs and the aftermarket.
PurePower Technologies produced over 30 million diesel fuel injectors since 1999, when the firm was founded. It now operates a 40,000-square-foot R&D center and a 200,000-square-foot production plant which is TS16949 and ISO 14001 Certified. So, all in all, it is a large firm that generates enough revenue to draw the attention of ransomware actors.
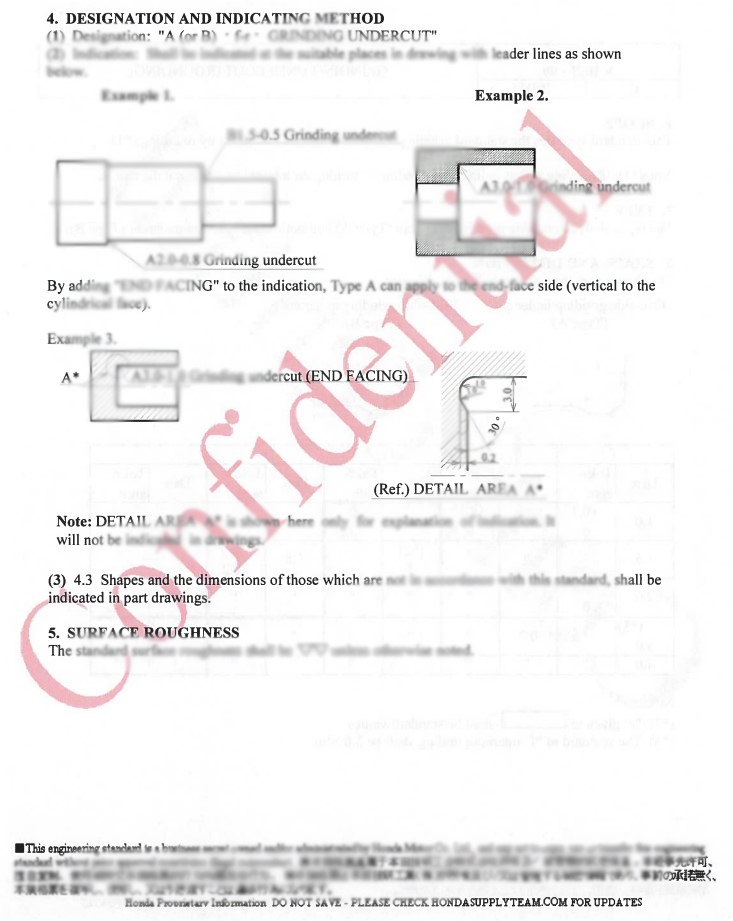
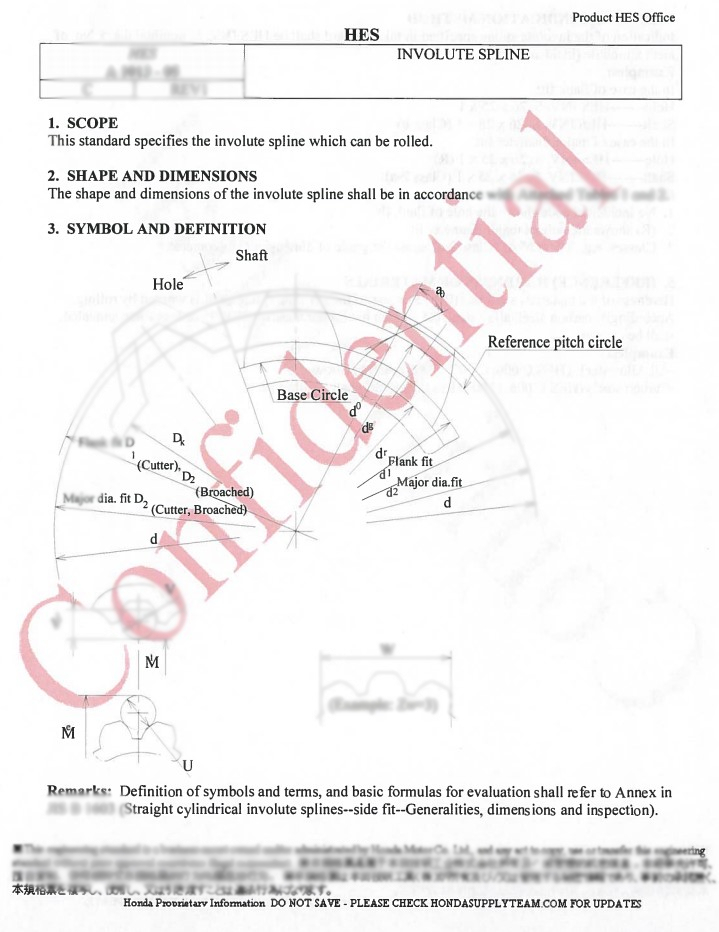
Conti appears to have exfiltrated sensitive and confidential data from the corporate network of PurePower Technologies, including schematics, technical drawings, financial details, presentation slides, inventory listings, supplier contracts, device spec sheets, service guides, historical revenue details, and more.
We have taken a look at some of the shared samples, and we can confirm that the files appear to derive from PurePower Technologies. Here’s are two blurred samples showcasing a page from a confidential document containing technical data.
The website of PurePower remains up, so there seems to be no disruption on the front-facing services. We don’t know what the case is with the production and manufacturing, though, which could have been undergoing downtime already. For now, the firm hasn’t published any statements about any data breaches or hacker intrusions. We have reached out, of course, and we will update this piece as soon as we hear back.
As for Stanadyne, Conti lists PurePower Technologies specifically, so we would take it that there was no pivoting to the owner company. Stanadyne is a much larger entity, operating manufacturing plants of fuel pumps and fuel injectors in the United States, China, India, and Italy. Stanadyne had reported a data breach back in February 2019, which exposed customer and employee details. Since then, the company has maintained a resilient stance, not suffering any compromises.
Conti partner activity continues unabated, and as the FBI warned last week, the actors target companies and organizations via a wide range of tricks and methods. According to the same advisory, Conti actors typically use stolen RDP credentials or send emails with malicious attachments to successfully establish a foothold on the target network. Some signs of their presence include the beaconing through ports 80, 443, 8080, and 8443, the appearance of new accounts, and the disabling of endpoint detection solutions.