Spectre Vulnerability Allows Malware to Hide and Run Stealthy
- A specially crafted malware can enter your CPU and keep on running unobstructively.
- While there are some significant technical limitations to this malware, it can still bite hard.
- The urgency to address modern CPU flaws decisively is now more crucial than ever.
There has been a lot of talk about Spectre and Meltdown vulnerabilities since their discovery about a year ago, and all security researchers agree that while the situation is currently under control, things will definitely get worse as we move further into 2019. A presentation on the ongoing NDSS Symposium in California however, has raised the concerns even more and rendered the addressing of Spectre more imperative than ever before. According to three scientists from the University of Colorado, it is technically possible to hide malware in the realm of speculative execution, making it completely undetectable.
Speculative execution is a processing optimization method, according to which the CPUs run some tasks proactively. This helps reduce the processing times by predicting the execution paths of programs, based on the previous history. Branch prediction, value prediction, memory and file prefetching, and optimistic concurrency control are all manifestations of speculative execution used in today’s systems. As this feature is built-in to the CPUs, the user has no insight of what runs at that level, so if something bad is executed in the context of speculative execution, the user will never know.
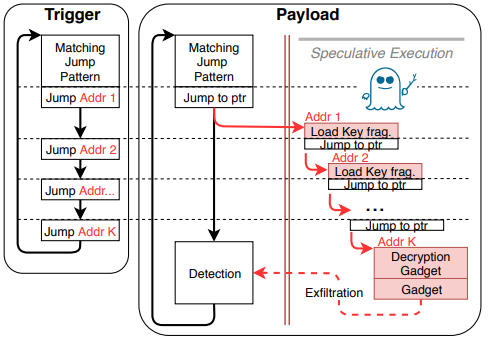
The three researchers took advantage of Spectre flaws that leak pre-computation sensitive data to attackers and created a malware that can be hidden so effectively that even a debugger following an instruction-level trace wouldn’t be able to tell what’s going on. The malicious binary cannot be detected, analyzed, or reverse-engineered, so it’s essentially the ultimate weapon. The decryption of the binary code happens in speculative execution, performing arbitrary system calls in a few milliseconds after its triggering. It all happens through OpenSSL, so the attack is launched remotely. The code of the binary cannot be very extensive (only up to 200 instructions), while the maximum decryption rate is 5.38 Kb/sec, but still, this is enough to cause serious trouble.
source: ndss-symposium.org
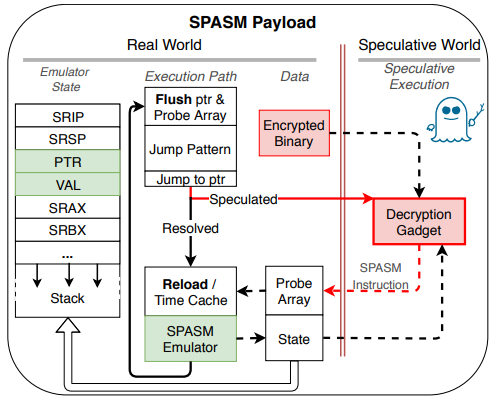
The security researchers have developed their own “Speculative Assembly” emulator and 6-bit instruction set so as to develop the malware and encrypt it into a payload program. While this light-weight emulator is ideal for this task, they note that a wrapper could be implemented around another emulator to construct payloads that are qualitatively different and still avoid detection and analysis.
source: ndss-symposium.org
Finally, the researchers suggest the development and implementation of silicon and microarchitecture patches, as CPUs are currently completely unprotected against this kind of malware. As they characteristically conclude: “New detection techniques and software-level mitigations are desperately needed until the flaws are fixed on the microprocessor level.”
How do you reckon the Spectre and Meltdown situation will unfold in 2019? Let us know your thoughts in the comments section below. Also, don’t forget to check out our socials, on Facebook and Twitter, where fresh news are posted continuously.