Watch Out for Spear Phishing Emails Impersonating Major Brands – Barracuda Networks
- Barracuda Networks points out that over 80% of spear phishing emails appear to come from major brands
- The rest use blackmail and business email compromise to pick up credentials and other data
The biggest chunk of spear phishing attempts feature emails that appear to come from well-known brands, new study shows.
According to a special report from Barracuda Networks, which was sent to TechNadu, 83% of spear phishing attack emails sent over a three month period - adding up to 360,000 emails - appeared to come from various brands. Another 11% of the emails used blackmail as a method, and 6% used business email compromise.
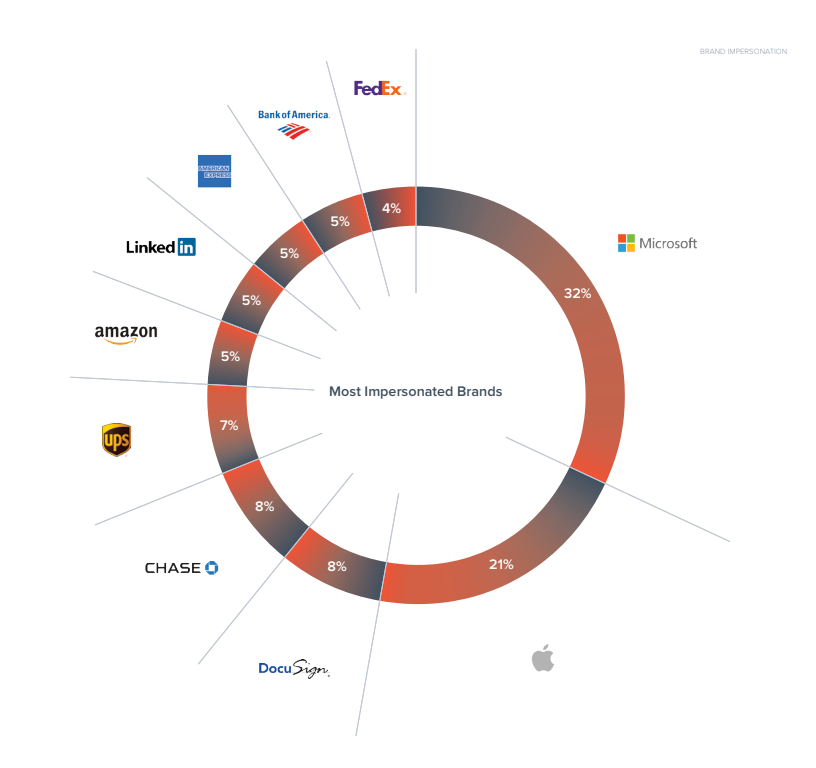
"These types of spear-phishing attacks, designed to impersonate well-known companies and commonly-used business applications, are by far the most popular because they are well designed as an entry point to harvest credentials and carry out account takeover," the report reads. "Brand impersonation attacks are also used to steal personally-identifiable information, such as credit card and Social Security numbers. Microsoft and Apple are the most-impersonated brands in spear-phishing attacks."
As far as the blackmail scams go, here you can even find sextortion attacks, where scammers claim to have recorded compromising video via the victim's computer. Business email compromise only makes up a small part of spear-phishing attacks because it's much more difficult to impersonate a company exec than a random brand.
If you're trying to figure out how best to avoid these scams, well, your email client may already be doing that job for you. If any of these messages fall through the cracks and end up in your inbox, remember always to check the address of the sender and make sure the site address is real. Plus, if it's of any help, it seems that spear-phishing attacks peak between Tuesday and Thursday.
How Do Brand Impersonation Attacks Work?
Scammers regularly use email to impersonate an entity you would trust, as one of the largest tech companies in the world. The purpose of the email is to get people to give up their account credentials or to click on malicious links. Attackers use domain-spoofing or lookalike domains to fool you into clicking on a link. Usually, for some reason or another, your account "was frozen," or you're asked to review a document and you're in sudden need to sign into an account.
As mentioned, emails appearing to come from Microsoft are most prevalent, with over 32% of emails coming from this "source". Apple takes second place with 21%. DocuSign and Chase follow up with 8% each, UPS with 7%, Amazon, LinkedIn, American Express, Bank of America with 5% each, and FedEx with 4%.
That being said, make sure you keep an eye out on what links you click on and what email addresses these messages come from! Since brand impersonation attacks often include "zero-day" links - namely URLs that are hosted on domains that weren't previously used for malicious attacks - they may go undetected by your email client. Under these circumstances, you have also to make sure to keep an eye on all details before providing your credentials.
Staying Safe Online
Barracuda's Olesia Klevchuk, senior marketing manager for email security, told us over email that there are multiple signs for individuals to look out for when getting suspicious emails from an unusual email address, an unusual request, an unexpected request to change the password and so on. "If your executive is asking you for an urgent wire transfer, purchase gift cards or any sensitive information – it’s always best practice to double check this request in person, over the phone or send a separate email that is not a reply to the one received," Kevhuck notes.
Also, when the requests involve changing passwords or reviewing recent activity, it's best not to click on the link within the email, but to login into account directly through the web browser.
As already mentioned, the browser won't help you in all instances, either, even if it commonly warns people of visiting unsecured pages. That's because hackers can always find ways to get around this type of problems by making their pages HTTPS too. "We regularly see these links as hackers are looking for new ways to circumvent security. Cybercriminals hack websites of legitimate organizations and insert their phishing login pages, this helps them to go undetected. They also don’t use the same sites for multiple attacks, rather investing time and effort in a more targeted approach," said Klevchuk. "When attackers do create their own sites they will often choose web encryption (HTTPS) to make it appear more legitimate and safe. Encrypted sites although might seem to be legitimate, are not always are, and should not be treated as 100% safe."
So, how do you stay safe online? Do you 100% trust your web browser to keep you away from harm? Do you check who's sending you emails?
Let us know by dropping a note in the comments section below. Please share the article online so others are made aware of the issues. Follow TechNadu on Facebook and Twitter for more tech news, reviews, guides, and interviews.