Spanish Bank Clients Now Face the “Grandoreiro” Malware Threat
- Hackers are manually overlaying banking login phishing pages on top of the real URLs.
- They are informed via a malware called “Grandoreiro” when the victim is visiting the targeted site.
- The malware can replace the Chrome shortcut with one that loads a malicious extension.
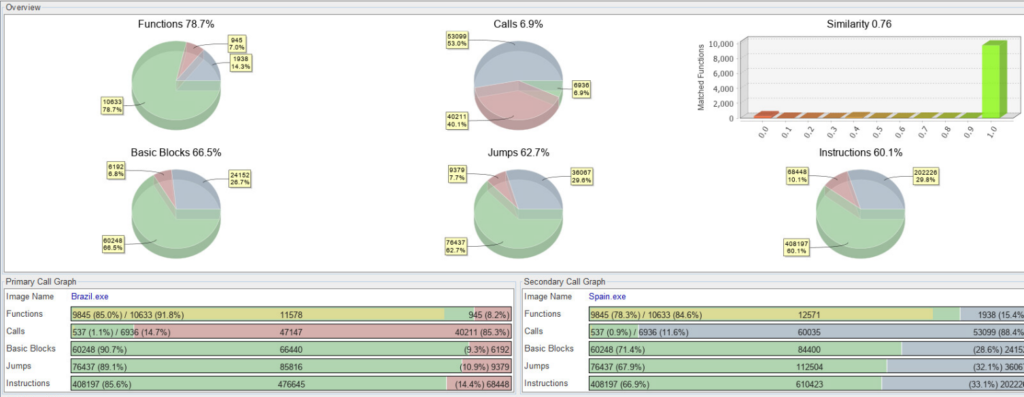
Banks and financial institutions in Spain are dealing with a new overlaying malware threat called “Grandoreiro.” According to an analysis conducted by IBM X-Force researchers, the particular malware easily migrated from Brazil to Spain, since its creators didn’t have much modification to do on its code (similarity of up to 90%). Banking trojans are used extensively in Latin America, as they have proven to be very successful over the last six years. It is possible that Spanish actors have bought the Grandoreiro on the dark web, or that they have direct ties with Brazilian hackers.
Source: securityintelligence.com
The infection begins with spam mail containing links to a dropper website. Grandoreiro uses .msi files masked as invoices to act as loaders. The additional modules are hosted on GitHub repositories for easy and reliable access, as well as detection risk mitigation. Once Grandoreiro receives the modules, it runs on the infected system and establishes communication with the actors. The operators are responsible for loading the overlays, which are made to look exactly like the real banks’ websites, asking the visitor to enter their e-banking credentials or other payment and credit card details. The inputs are then stolen and transmitted to the C2 server via SSL (encrypted communication).
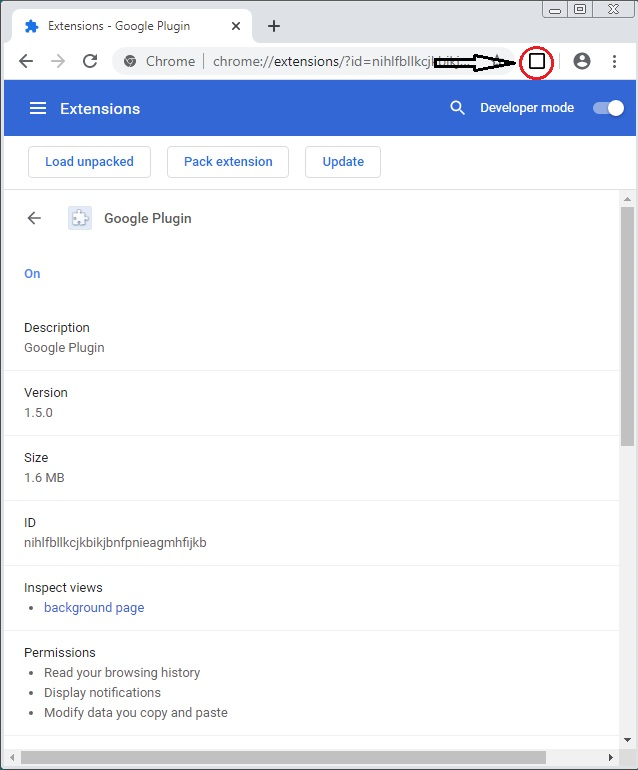
Grandoreiro is sending notifications when the victim accesses a banking site, sends machine information, clipboard data, and can facilitate remote access capabilities. The malware is also engaging in a pretty neat trick that kills any active Chrome sessions and replaces the browser shortcut with one that has a parameter for loading a malicious extension. The extension is named “Google Plugin” v1.5.0. While it sounds legit, it is the piece of code that will access your browsing history, push notifications, modify the copy and paste data, and collect user information from cookies.
Source: securityintelligence.com
If you’re wondering about what you can do in order to protect yourself from these risks, the first step would be to disregard unsolicited email communications. Secondly, you should use browser modes that don’t allow running extensions, such as the incognito mode in Chrome. Thirdly, using a network security solution would most certainly detect and block the overlaying attempt that takes place when you try to visit the banking website. Finally, using a password manager that automatically fills in your credentials could potentially act as a savior in the case of overlays, as seeing nothing filled in the page would be a chance for you to realize that you’re dealing with a fake overlay.