Popular South Korean Bus App Found to Contain Malware Delivery Code
- An Android bus-tracking and route-information app has turned into a malware dropper, four years after its initial release.
- The malware targets the Google account credentials of users, prompting them on a fake login form.
- The malware has been delivered to very few people, but many thousands are still using the app, risking an infection.
As revealed by McAfee’s Mobile Research team, a South Korean bus app that has been under development for the past five years is actually a malware delivery tool. The app is masquerading as a bus stop locator and bus arrival estimator, and according to McAfee, it was not always malicious but turned into one at a later date, and more specifically last summer. This means that many Koreans may have been using the app for a long time until one day it delivered malware into their device. The particular app, as well as others in the same series that have been developed by the same person, have now been removed from the Google Play store.
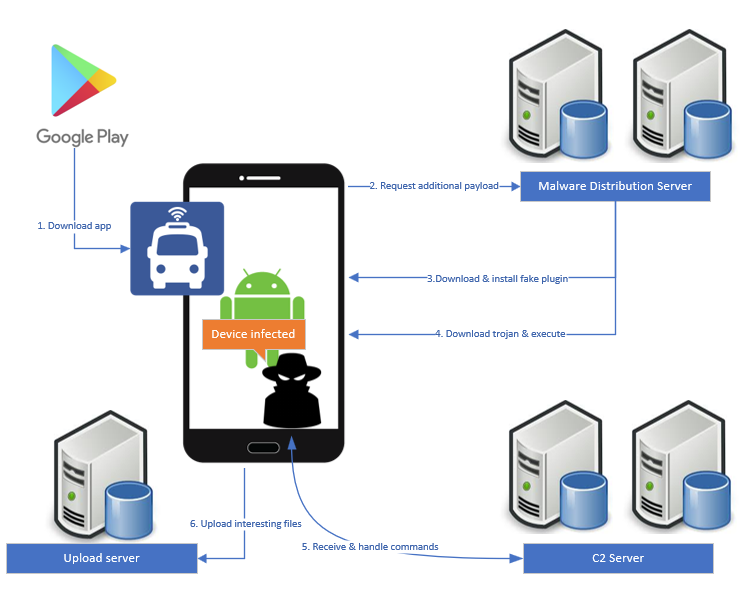
According to the findings of McAfee's researchers, the particular malware that is downloaded from the command and control server is focused on phishing, prompting the victims to input their Google account login credentials on a fake form, so that the app can take full control of the compromised device. Another interesting point is that the malware utilizes a native library (libAudio3.0.so) for this process, while it deletes it on its next step, so the detection of something “phishy” gets harder and more unlikely.
source: securingtomorrow.mcafee.com
Further analysis of the various versions of the malware indicates the presence of the aforementioned library in all malicious releases, which is absent in the old and clean version. In total, the malicious versions have been downloaded by over 650.000 users, so the chance of many still having it on their devices is high. However, McAfee’s telemetry data shows that the actual number of the infected devices is currently low, so the final payload was not delivered widely just yet. However, keeping these apps installed on a device, now that their purpose has been revealed, is especially risky.
The malware does not only attempt to phish the user credentials through the fake JavaScript Google login page but follows other paths as well. For example, it requests a password recovery which may trick users into believing it, or even sets a recovery email address when the users create a new Google account so that it can get access and control to the actual user account.
As we have seen it happen in the past, not all malware delivery apps start as such, since building up a user base before breaching trust is an excellent strategy to do the most massive possible damage (and earnings). This bus app and its siblings are a characteristic example of this category of apps, proving that you should never trust an app unconditionally. Even after four years of enjoying it, it may turn into a malicious one, either intentionally, or without the developers even realizing it.
Have you had a similar experience with an app? Let us know in the comments beneath, and don’t forget that you have the power to help us spread the word of warning to others by sharing our posts through our Twitter and Facebook.