Sophisticated LockBit Ransomware Attack Exploits Enterprise Network Vulnerabilities
- A complex cyberattack leveraged Cobalt Strike masquerading as Microsoft Windows Media Configuration Utility files.
- The attacker successfully established persistence on the backup server using GhostSOCKS proxies.
- Abusing the victims’ elevated permissions, the attack culminated with the deployment of the LockBit ransomware 11 days after initial access.
A meticulously coordinated cyber intrusion, leveraging multiple advanced tactics, recently culminated in deploying LockBit ransomware across an enterprise network via a fake media configuration executable used as a Cobalt Strike beacon.
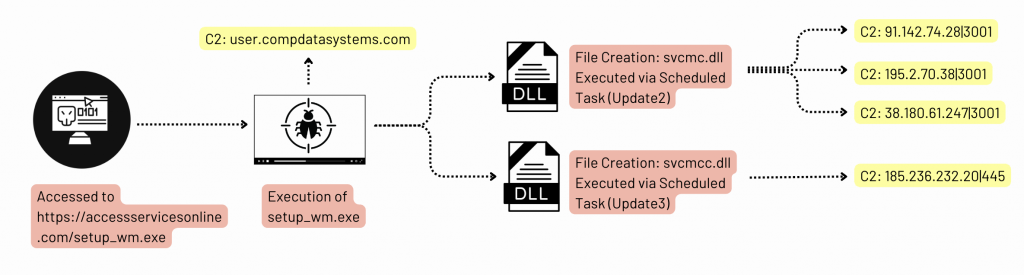
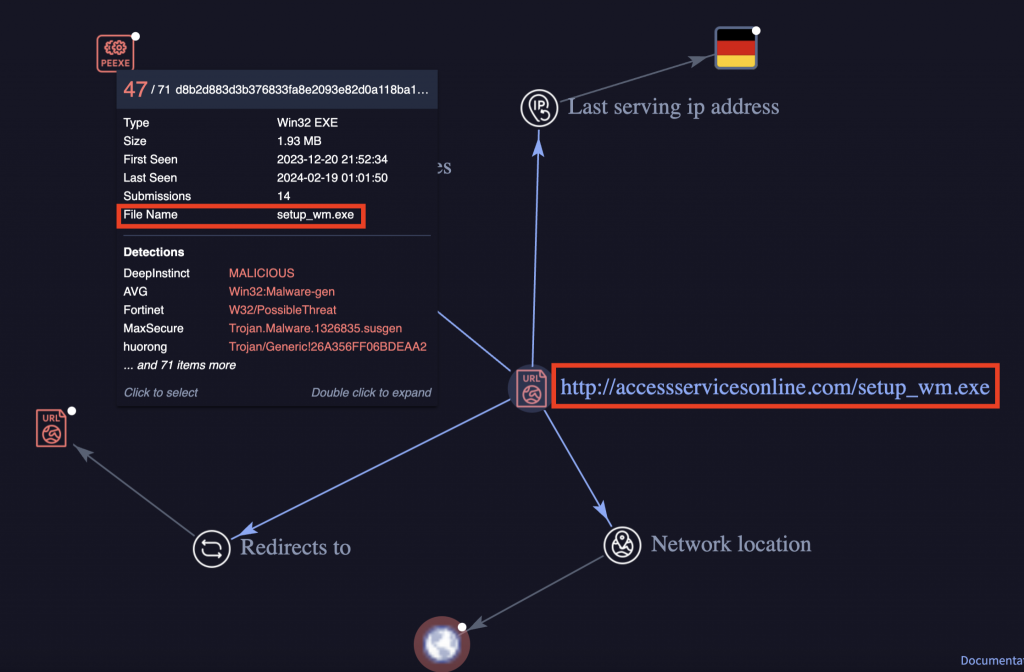
The attack began in late January 2024 when a user executed a malicious file disguised as the Microsoft Windows Media Configuration Utility named "setup_wm.exe," which initiated an outbound connection within minutes, according to the latest DFIR security report.
Approximately 30 minutes post-execution, the beacon launched reconnaissance commands, uncovering domain controllers via "nltest." Capitalizing on the victim's elevated permissions, the attacker distributed proxy tools—SystemBC and GhostSOCKS—onto a domain controller using SMB and remote services.
Despite Windows Defender neutralizing GhostSOCKS, SystemBC established a persistent command and control (C2) channel, allowing the attacker to further compromise the environment.
With the previously injected WUAUCLT.exe process acting as a vantage point, the threat actor executed additional reconnaissance by extracting credentials from the Local Security Authority Subsystem Service (LSASS).
The attacker injected two additional tools—Seatbelt and SharpView—to enhance situational awareness, while persistence was maintained through scheduled tasks re-executing SystemBC and GhostSOCKS proxies.
One hour into the breach, the attacker laterally moved to a file server via remote services using the same user account compromised in the initial attack phase. On the file server, they deployed a new Cobalt Strike PowerShell beacon communicating with a secondary C2 server alongside additional instances of SystemBC and GhostSOCKS proxies.
By leveraging these proxy tunnels, the attacker initiated a Remote Desktop Protocol (RDP) session to explore the file server configuration. This included reviewing running processes, accessing the Local Group Policy Editor, and disabling specific Windows Defender settings to ensure their persistence went undetected.
The attacker explored shared files and located a sensitive document containing stored credentials. These credentials enabled access to a backup server, where attempts to deploy a Cobalt Strike PowerShell beacon were initially blocked by Windows Defender.
However, after issuing a WMI command to disable Windows Defender's real-time monitoring on the target, the attacker successfully established persistence on the backup server using GhostSOCKS proxies.
Roughly four hours post-initial access, the attacker pivoted to exfiltration efforts. Internet Explorer on the file server probed temporary file-sharing sites, likely as staging areas for stolen data. Despite no downloads being observed, the attacker transitioned to Rclone, a popular cloud synchronization tool, to begin larger-scale data transfers.
While an initial attempt via FTP failed due to server issues, success was achieved by pivoting to Mega.io as the destination. Using Rclone, data exfiltration continued uninterrupted for approximately 40 minutes. The attacker then returned to FTP and established an extended data transfer session lasting nearly 16 hours.
After pausing for nearly 11 days, the attacker revisited the network with a clear objective — ransomware deployment. Multiple batch scripts were distributed across the enterprise network using the backup server as a staging ground. Tools such as PsExec and BITSAdmin facilitated the propagation of the ransomware binary, ds.exe, identified as LockBit, to Windows hosts.
These scripts also included commands to disable Windows Defender and modify RDP settings network-wide to streamline ransomware execution and restrict remediation efforts. The attack concluded with ransomware encrypting critical systems across the environment in just under 239 hours.