Sophisticated Actors Refresh Their ‘SombRAT’ Backdoor to Hide Better Following Analysis
- A group of APT actors using the SombRAT backdoor for months is now circulating a new version.
- The new iteration features better obfuscation and anti-analysis, but the group’s operations are still being tracked.
- The group is either making a move in the “hackers for hire” space or selling SombRAT to others as well.
A group of APT actors who are likely operating from the Latin American region and is dubbed “CostaRicto” has been working on refreshing its tools and C2 infrastructure in response to having been analyzed by the BlackBerry threat research and intelligence team. This is a typical move by sophisticated actors, but it appears that they still failed to hide their tracks and operations, as BlackBerry is back with another update on the details of this refresh.
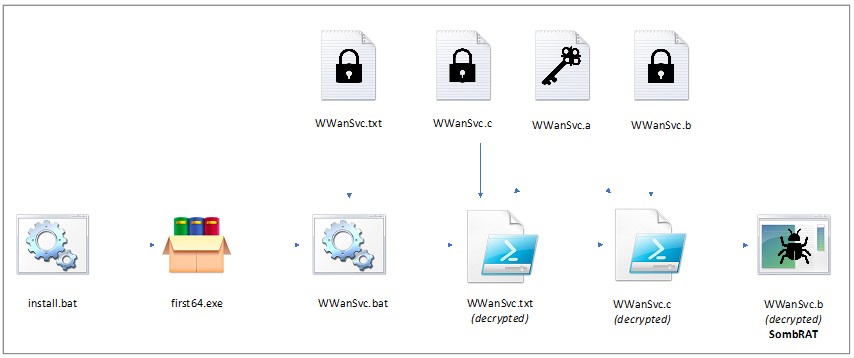
According to the report of the former smartphone maker turning into a security firm, CostaRicto is an APT which lends some tricks from APT10 and APT28, even though there doesn’t seem to be a direct relationship, to target corporate entities in the South Asian region (India, Bangladesh, Singapore). The group has been using a custom backdoor named “SombRAT,” which comes in both x86 and x64 variants and features RSA-2048 C2 traffic encryption, AES-encrypted storage for the harvested data, and communication over DNS tunnel with DGA-generated subdomains.
The actors have been using the particular backdoor since at least November 2020 and are still using it, albeit with some modifications. Other tools in CostaRicto’s arsenal include CobaltStrike, WinPwn, Rubeus, TeamViewer, AnyDesk, PsExec, SoftPerfect, and various other network reconnaissance third-party tools that are not inherently malicious.
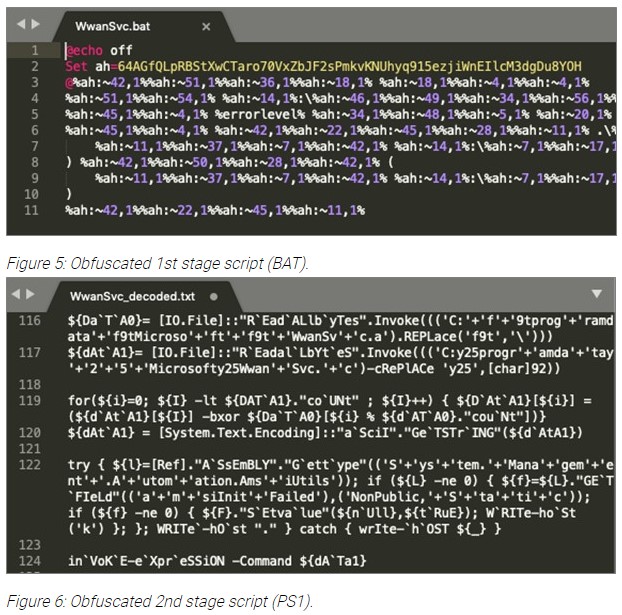
Following the December revelations, the actors have introduced some modifications and improvements to hide from the researchers, and these can be summed up in the following things:
- Compilation timestamps have been overwritten with zeros;
- Program database (PDB) paths are not included;
- The internal versioning system has changed;
- Run-time-type-information (RTTI) has been removed from the binaries to prevent easy C++ class analysis;
- The code is now statically linked with a TLS library called mbedtls, which is employed to avoid using Windows® cryptographic APIs for RSA key handling (and evade EDR software);
- Modifications to C2 commands;
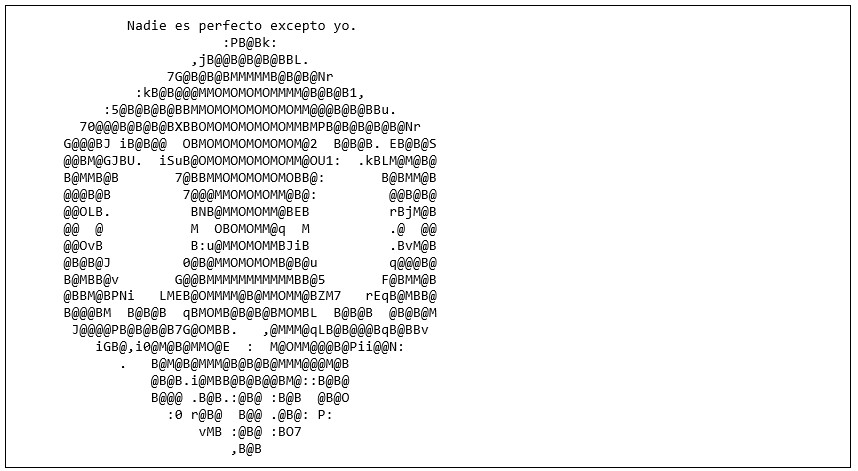
- A new ASCII art message containing the message "Nadie es perfecto excepto yo" (No one is perfect except me).
As BlackBerry details in its report, it appears that CostaRicto is evolving and broadening its services, as the victims now include companies in Europe, America, and other seemingly “random” places. Another possible explanation besides CostaRicto being “hackers for hire” is that they are selling SombRAT to other groups, so it’s being used for various purposes.
Whatever the case, it is clear that SombRAT is under active development and is being constantly improved. Most worryingly, the actors have added the ability to exfiltrate data from the compromised machine now, whereas previously, SombRAT was only capable of deploying ransomware.