Unique Social Engineering Campaign Installs Malware via Fake Google Chrome Errors
- A unique social engineering campaign runs PowerShell and installs malware on victims’ devices via fake Chrome errors.
- The cybercriminals present what could be a real problem and offer a solution, enticing potential victims to click through.
- Security researchers say this technique has been deployed by TA571 and the ClearFake activity cluster.
Security researchers have observed a surge in the use of a technique employing unique social engineering that asks potential victims to copy malicious PowerShell scripts that deploy malware on their computers, including DarkGate, Matanbuchus, NetSupport, and various information stealers, as per a Proofpoint report.
This method has been used by several threat actors, including initial access broker TA571 and at least one fake update activity set, such as ClearFake. On March 1, 2024, TA571 started a campaign targeting thousands of organizations globally with over 100,000 messages. In early April, the fake browser update cluster that compromises legitimate websites with malicious HTML and JavaScript started using this technique as well.
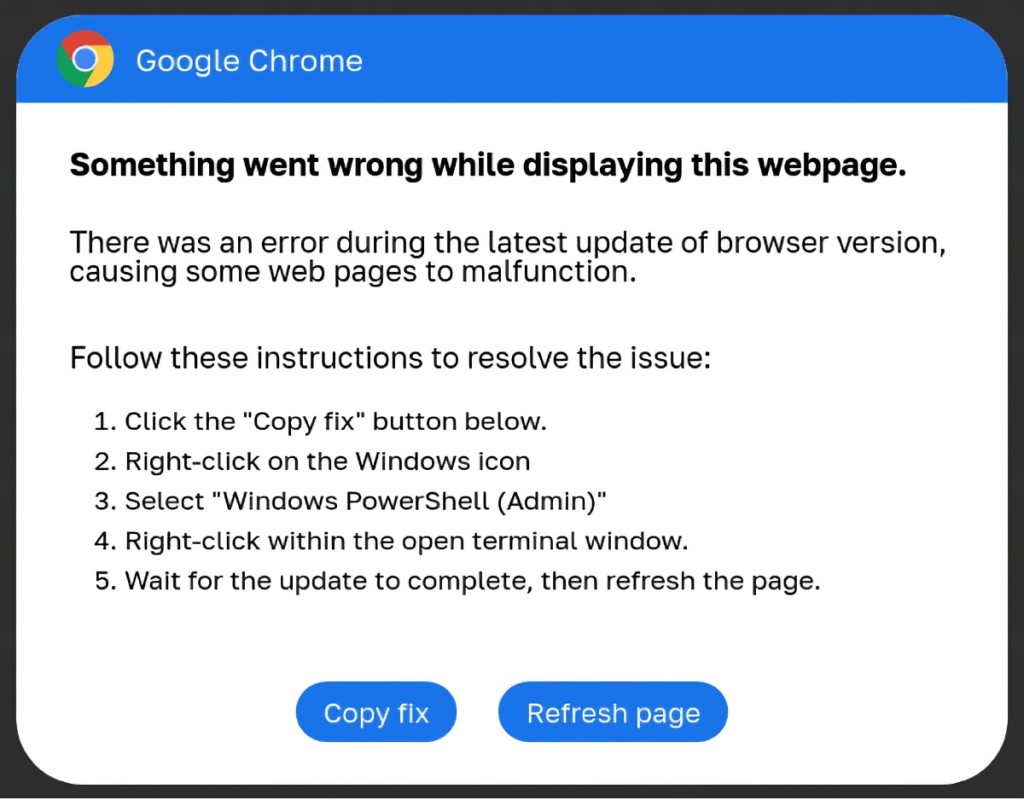
The initial campaign begins via malspam or Web browser injects. Chrome users see a popup textbox that says an error prevented the document or webpage from functioning. It instructs potential victims to copy and paste a malicious script into the PowerShell terminal or the Windows Run dialog box.
In a ClearFake example, they used a technique known as "EtherHiding," where the compromised site loads a malicious script hosted on the blockchain via Binance’s Smart Chain contracts, which then loaded a second script from a domain using Keitaro TDS filtering. Eventually, the potential victims were presented with a fake warning overlay asking them to install a certificate to view the website correctly.
The message instructed the user to copy a PowerShell script by clicking a button and followed up with steps to paste it into the PowerShell command line interface window and run this script on the victim's computer, which led the user to execute the PowerShell on their own device.
The scripts performed various functions, including flushing the DNS cache, removing clipboard content, displaying decoy messages, executing a remote PowerShell script, obtaining system temperatures via WMI, or downloading a “data.zip” file. The archive bundled various legitimate, signed executables that side-loaded a trojanized DLL using DOILoader to load Lumma Stealer, which downloaded payloads enabling malware execution.
TA571 used email as a campaign starter, which has been observed to contain HTML attachments mimicking Microsoft Word files that came with an error message asking for a fix.