SneakyChef Espionage Group Targets Worldwide Government Agencies With SugarGh0st Malware
- SneakyChef espionage group has expanded its scope to EMEA and Asia government agencies.
- The cybercriminal group deploys a remote access trojan dubbed SugarGh0st onto the infected systems.
- Victims are lured with document scans impersonating official communication from various ministries.
SneakyChef, a newly discovered threat actor that was seen using SugarGh0st malware, is now targeting governments across EMEA and Asia, in addition to South Korea and Uzbekistan, as a Cisco Talos report says. The group uses scanned documents of government agencies like ministries of foreign affairs or embassies as a lure.
SneakyChef is a threat actor discovered in August 2023, when a campaign using remote access trojan (RAT) security researchers named SugarGh0st was deployed against the Uzbekistan Ministry of Foreign Affairs and users in South Korea via a malicious RAR with an LNK file, likely delivered via phishing email.
Cisco Talos discovered last week a new RAT dubbed SpiceRAT SneakyChef used to target government agencies in EMEA and Asia. Now, an extra infection chain uses SFX RAR files to deliver SugarGh0st to the same regions. Most of the samples observed in this campaign communicate with the same C2 domain account[.]drive-google-com[.]tk as their previous campaign.
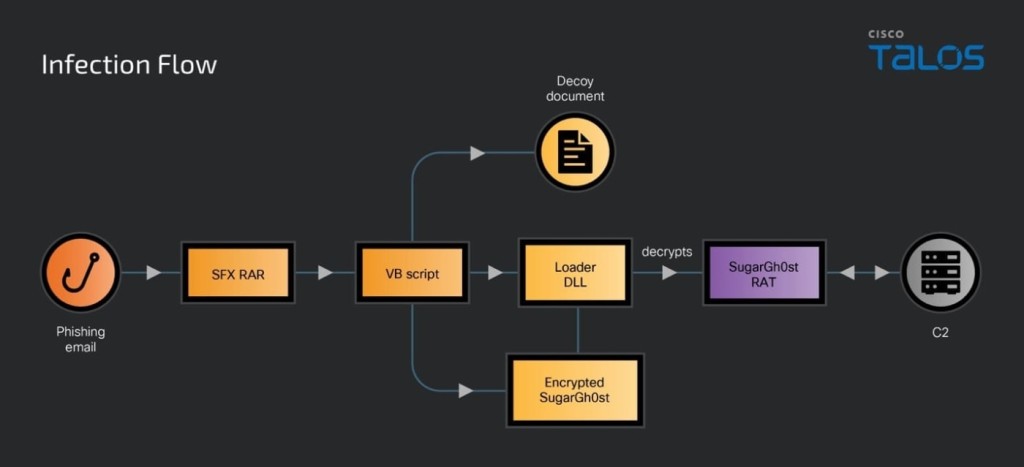
SneakyChef added a new technique, using an SFX RAR as the initial vector. When executed, the SFX script drops a decoy document, DLL loader, and encrypted SugarGh0st into the victim’s user profile temporary folder. It also downloads and executes a malicious VB script that establishes persistence.
The malicious script writes the command to a registry key that executes when a user belonging to a local workgroup or domain logs into the system. It then runs and launches the loader DLL “update.dll” using regsvr32.exe. The loader reads and decrypts SugarGg0st RAT “authz.lib” and injects it into a process.
Based on the contents of the decoy documents, the potential targets could be Angola, Turkmenistan, Kazakhstan, India, Abu Dhabi, and Latvia.
The lure content in the sample documents included a debt conciliation meeting between a ministry authority and a financial advisory company, a meeting between the Turkmenistan embassy in Argentina and the representatives of transportation and infrastructure of Italy, a formal proclamation-signing event between Uzbekistan and Kazakhstan.
Other examples include an official circular about creating an official Saudi Arabia holiday, an Indian passport application form, a document with India-U.S. bilateral relations events, and a circular impersonating the Embassy of Lithuania announcing the absence and replacement of an ambassador in Latvia.
Governments were not the only target, as the campaign also included documents related to the Universal Research Cluster (URC) conference, the ICCSE international conference, the Political Science and International Relations conferences.