Snaptrip Database Leaks Out Personal Data of 200 of its Customers[Updated]
- Hashed payment data and CVV tokens of the cards of Snaptrip customers have been leaked.
- The lodge renting company has left a MongoDB instance unprotected for at least four days.
- The company has now secured the database but has not issued an announcement yet.
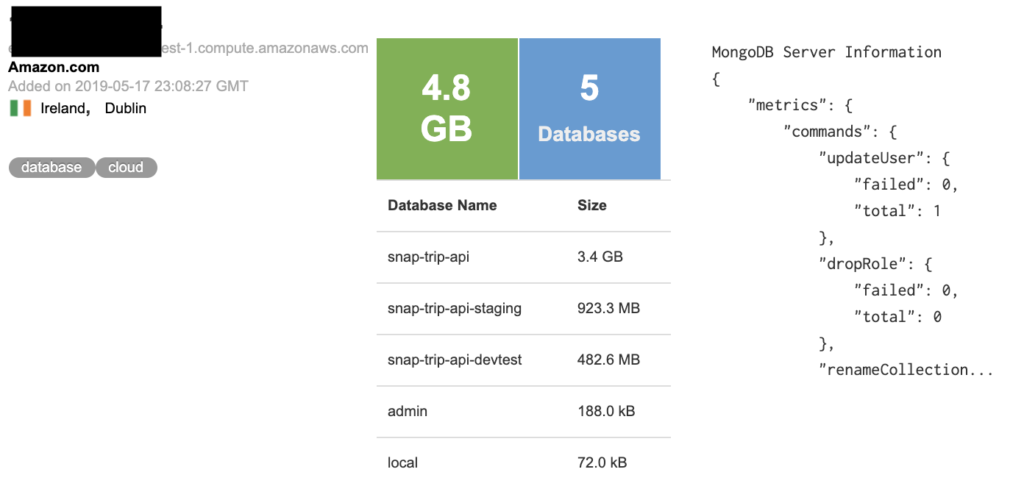
According to a report by Bob Diachenko, the London-based “last minute cottage renting” company Snaptrip has leaked out the sensitive information of about 200 of its customers. The company has entered the endless list of entities who have misconfigured their MongoDB database, exposing the personal and even financial information of their clients. Snaptrip’s MongoDB instance counted five databases of a total size of 4.8 GB, containing the full names, email addresses, phone numbers, and physical address details. Moreover, it contained payment data such as the brand, type, holder name, PAN token, and CVV token. While the records that have been leaked are about a thousand, most of them were testing entries, and the actual number of affected customers is two hundred.
image source: securitydiscovery.com
The researcher discovered the database on May 21, 2019, and immediately notified the company of the fact that they had left their MongoDB without a login password. The company responded almost immediately by securing the database in a couple of hours, but so far, they have not published a statement to clarify if there is any evidence of malicious access in the database, or for how long has the information remained accessible. The Shodan index shows that this date is at least May 17, 2019.
What didn’t happen, although it could have, is the complete taking over of the database, the installation of ransomware, or the planting of malware. Leaving databases with backend details exposed and unprotected like that is an invitation to cyber-criminals to take it over and manage the system as administrators. That is after they dump everything that’s contained in the database of course, which in this case was a collection of invaluable payment information. Whether this last part actually happened or not, no one knows until Snaptrip starts sending notifications, if they are even planning to.
If you have booked a last-minute cottage or lodge in the UK through Snaptrip, you shouldn't be freaking out right now, as the payment data that was contained in the database entries is hashed and encrypted. This means that it would be practically infeasible, if not entirely impossible, for hackers to decrypt the leaked information.
Care to share any thoughts on the above? Feel free to do so in the comments down below, and also on our socials, on Facebook and Twitter.