Smishing Scams Impersonating Toll Roads Rising Due to Enhanced Phishing Kits Sold by Hackers
- A surge in smishing was observed across the U.S., asking recipients to pay debts to scammers impersonating legitimate toll road operators.
- These phishing pages load only on mobile devices and ask for sensitive data such as payment details and OTPs.
- This rise may be due to enhanced SMS phishing kits sold by China-based hackers who integrated phishing infrastructure with iMessage and RCS.
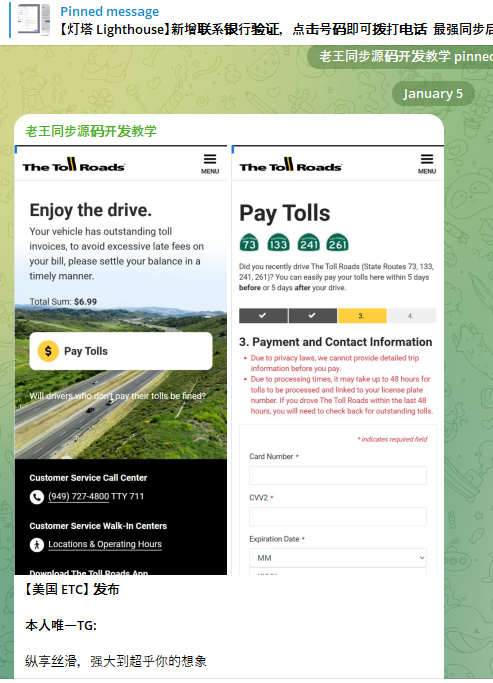
Residents across the U.S. are facing a surge in SMS phishing scams mimicking toll road operators like E-ZPass, North Texas Toll Authority, Sunpass, or The Toll Roads. These smishing messages often warn of unpaid tolls and fines, luring unsuspecting recipients into providing sensitive payment information.
According to security experts, this uptick aligns with the release of enhanced phishing kits sold by cybercriminal groups based in China, enabling the creation of sophisticated spoofed toll operator websites targeting mobile users.
Last week, the Massachusetts Department of Transportation (MassDOT) alerted users of its all-electronic tolling program, EZDriveMA, to a new wave of smishing attacks, which typically direct to phishing pages that request payment card details and a one-time password (OTP) sent via SMS or authentication apps.
Simultaneously, similar phishing attacks were reported across the country. Residents in Florida, Texas, California, Colorado, Connecticut, Minnesota, and Washington received fraudulent texts posing as local toll road services, such as Sunpass in Florida and the North Texas Toll Authority.
These phishing pages are specifically designed to load only on mobile devices, seamlessly mimicking the legitimate websites of the targeted operators.
Ford Merrill, a security researcher at SecAlliance, attributes the dramatic rise in toll phishing scams to advancements in SMS phishing kits sold by China-based cybercriminal vendors. These kits include phishing pages explicitly built to impersonate toll road operators across various U.S. states.
According to Merrill, multiple distinct phishing kits are being sold, with each attracting thousands of users. Their primary aim is to steal enough personal information to add compromised payment cards to mobile wallets and use them for financial fraud or laundering money through shell companies.
While SMS phishing kits have been around for years, Chinese smishing groups are now innovating delivery methods, integrating phishing infrastructure with Apple’s iMessage and Android’s Rich Communication Services (RCS) as critical developments.
These rich-text channels bypass many telecom filtering systems and often yield higher success rates, enabling more seamless phishing campaigns.
According to the MassDOT, targeted phone numbers appear to be chosen randomly and are not linked to specific toll road accounts. Some recipients, like a user on Mastodon, reported receiving phishing attempts despite not owning a vehicle.
In August 2024, a novel Remote Access Trojan (RAT) infected Android devices via smishing, employing Account Takeover (ATO) via a well-known technique called On Device Fraud (ODF).