Fake Slack Ads Deploying Malware Are Introduced Gradually via Google Ads to Avoid Detection
- A new malvertising campaign uses the Slack communication tool as a lure to deploy malware.
- Fake ads for this legitimate tool were introduced gradually, initially just redirecting users to the official Slack website.
- In the beginning, the actors used a non-malicious fake domain to prevent the newly created websites from being flagged as fraud.
Unnamed threat actors patiently developed a malvertising campaign with multiple layering that ultimately deployed malware. The operation targeted users interested in installing the legitimate Slack communication app, a new report from security company Malwarebytes said.
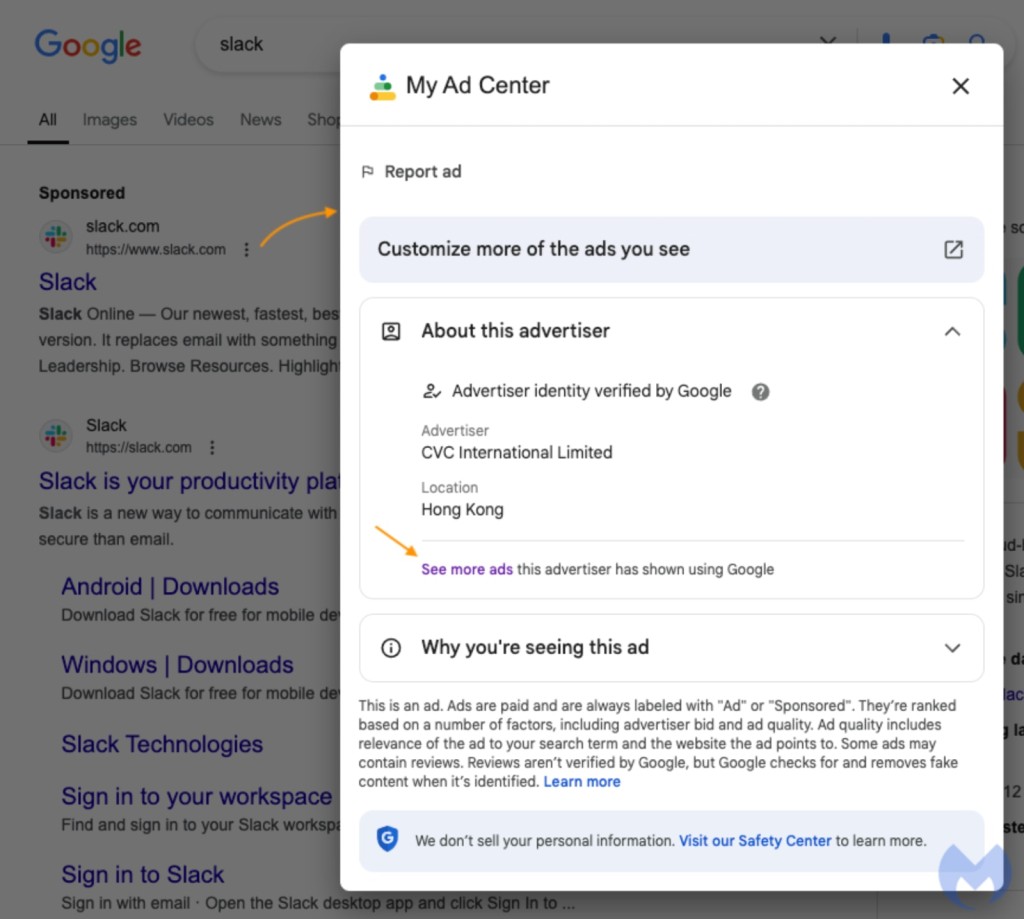
The fake Slack ads’ advertiser information in the Google Ads Transparency Center showed they registered as CVC International Limited and promoted products for the Asian market.
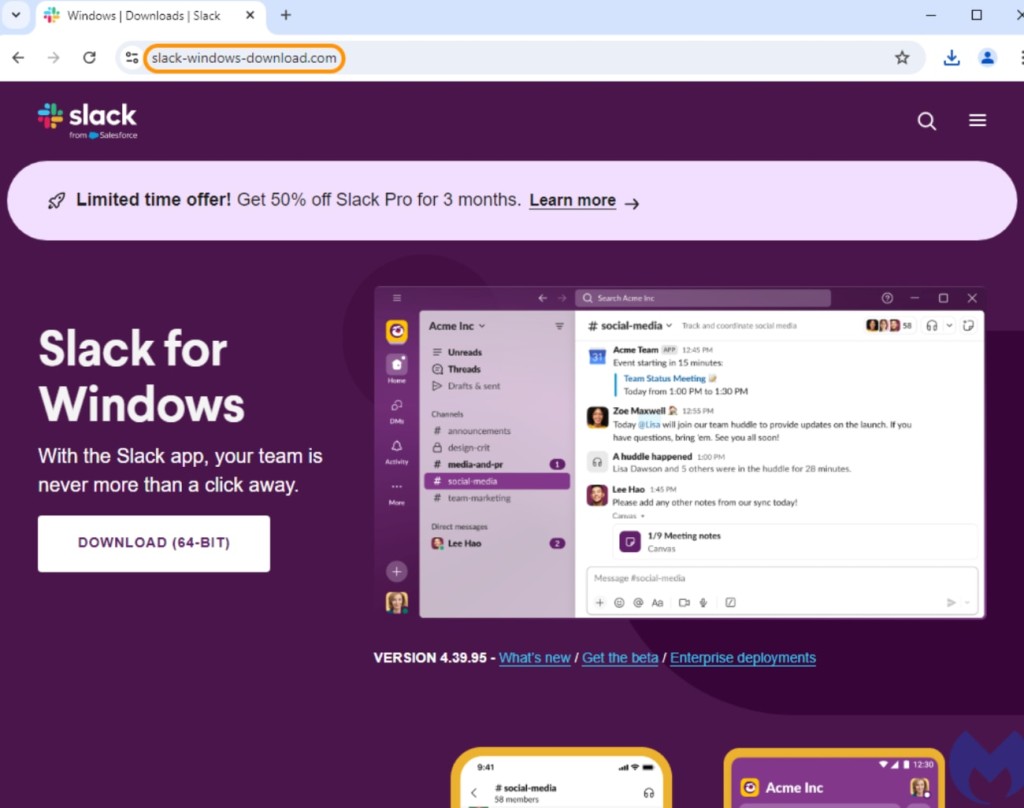
To avoid being immediately flagged, the deceiving ad led to a price page on Slack’s official website in the beginning. Lately, it redirected to a click fraud detection tool, followed by a click tracker. Then, the ad’s final URL became a domain without malicious content: slack-windows-download[.]com.
However, the security researchers could see the malicious page after tweaking some settings.
The click trackers are followed by one more cloaking domain, resulting in deep layering that makes evaluating an ad harder unless one has specific tools and knowledge of the threat actor’s tactics, techniques, and procedures (TTPs).
This is one of the Google ad ecosystem’s weaknesses, as the Alphabet Inc.-owned service cannot know where users are going after the click tracker since such services can be abused to filter clicks and send traffic to any domain.
Clicking the button to get the app triggers the malware binary download from another domain, and researchers say they saw a hint of a parallel campaign targeting Zoom in the file’s name.
The server used for the remote connection was previously used by SecTopRAT, an infostealer RAT, while this payload was previously used in previous malvertising operations, including fake NordVPN ads.
In the past year, hundreds of unique malvertising incidents related to Google search ads were observed.
Recently, a phishing site masquerading as an official ‘Google Safety Centre’ page deployed malware like Latrodectus and ACR Stealer while pretending to let users download the trusted multi-factor authentication (MFA) app Google Authenticator.
Simultaneously, a fake ad for Authenticator appeared among Google search results, and the advertiser’s identity was even verified by Google.