New Slack and GitHub Backdoor Malware Evades AntiVirus Detection
- A new malware that communicates via Slack, and uses GitHub gist snippets is spotted on the wild.
- The particular malware seems to be the work of sophisticated actors, evading detection of AV tools.
- The malware takes advantage of two vulnerabilities that have already been patched, but many websites remain susceptible.
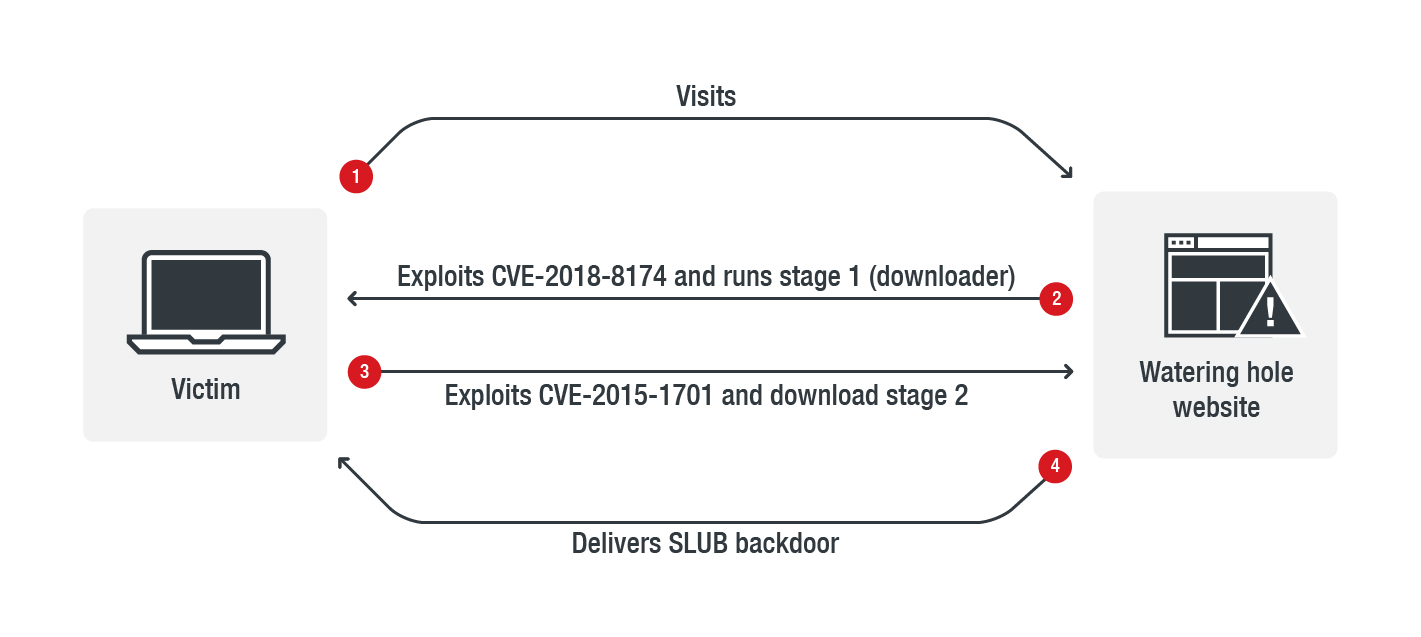
Trend Micro cyber-security researchers have encountered a new malware that exploits a VBScript engine vulnerability (CVE-2018-8174) to compromise legitimate websites and redirect their visitors to another page that downloads a malicious DLL and run it in PowerShell. This file in turn, downloads a second executable that downloads a backdoor, which is the final payload. According to the detailed report, the malware is scanning the infected system for the presence of anti-virus tools, and exits if any are found to be running, however, the backdoor is not detected by any AV products at this time.
source: blog.trendmicro.com
The attackers are using the “watering hole” technique to compromise a targeted website by inserting a piece of code that leads to the malware infection for its visitors. The attackers carefully gather the required website information to figure out which ones are unpatched, and thus vulnerable. It’s a robust method and attackers have been using it extensively since 2009.
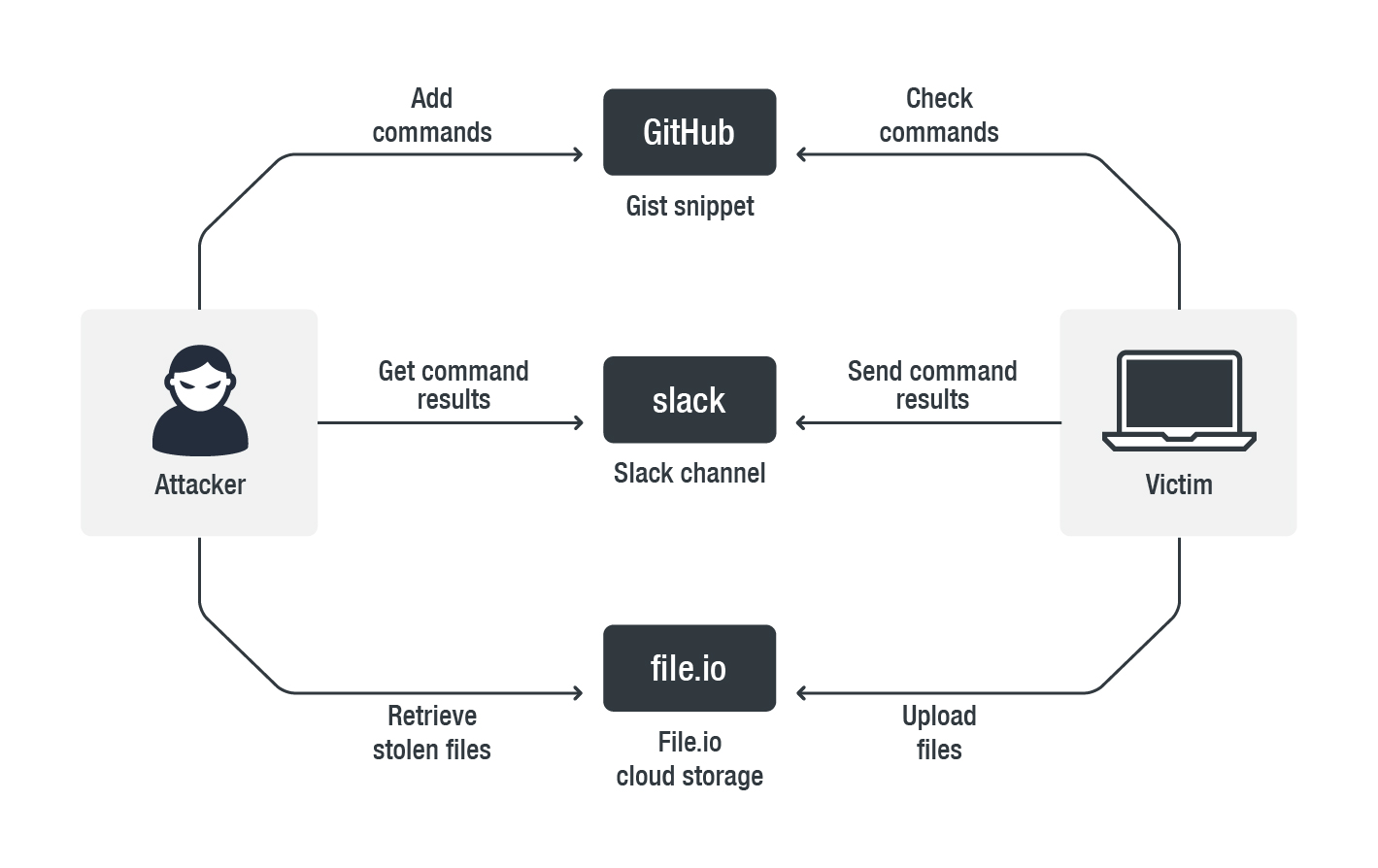
Because the particular malware is using Slack to communicate and its exploit code is most probably the result of a modification of a GitHub repository code and uses Gist snippets, Trend Micro’s researchers have named it as “SLUB” backdoor. Written in C++, it performs multiple HTTP requests, while its commands set includes process listing and termination, registry key read and write functions, file downloading, directory creation and removal, and more. A screenshot action (capture) is also included and used for the purpose of sending it to the Slack channel for communication between the victim’s machine and the attacker. The following diagram shows how it all works together for SLUB.
source: blog.trendmicro.com
The danger of SLUB’s presence for the infected machines relies on the fact that it scans multiple key areas of the system to collect personal information, and even creates CAB files to archive the victim’s files and send them to the attacker. Examples include the user’s entire Desktop folder, the Skype local archive, word processor directories, and more. The exfiltration of data from some of these directories has not been 100% implemented yet, but it is seen in the code.
source: blog.trendmicro.com
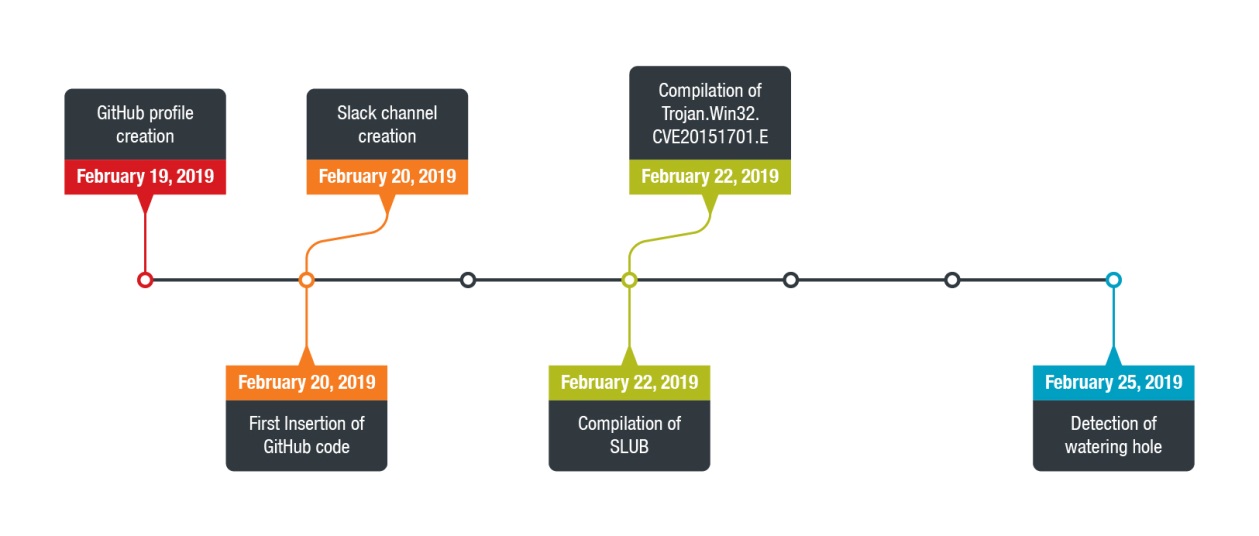
Trend Micro’s analysis shows that the timeline for SLUB starts on February 19, 2019, with the GitHub code and Slack channel being inserted and created in the next day. The compilation date for SLUB is February 22, 2019, and the detection of the watering hole on the compromised website occurred on February 25. That said, and considering the AV tools currently miss the particular backdoor, web admins are urged to update their tools, setup and use network traffic detection solutions, and correlate APT activities to figure out whether something suspicious is going on in their network.
Have you ever fallen victim of a watering hole attack? Share your experience in the comments section below, and help us spread the word by sharing this post through our socials, on Facebook and Twitter.