“Silver Sparrow” Malware Perched Inside 30,000 M1 Macs
- A new malware that was made to run on Apple Silicon has already infected 30,000 endpoints.
- The malware is keeping a low profile, not doing anything nasty on its hosts for the time being.
- There are many mysteries around the malware’s source, infection method, purpose, and features.
At the end of last week, we discussed the discovery of the first piece of malware written specifically to run natively on the new Apple Silicon platform and warned you about this being just the beginning of a new wave. Apparently, at the same time, another M1-specialized malware called “Silver Sparrow” was just being discovered by researchers of ‘Red Canary.’ According to Malwarebytes data, this one has already infected 29,139 Macs across 153 countries. For now, the malware hasn’t fetched its potentially malicious second-stage payload, but this could happen at any moment.
It is possible that this is just a security exercise and that there’s no second payload to threaten the infected users, but the existence of the particular malware and the success in its distribution is causing a headache to Apple’s security engineers. However, as the researchers warn, there’s also the scenario of the payload having been already delivered and removed at a later stage after it had done its data exfiltration job. Again, there’s no way to tell.
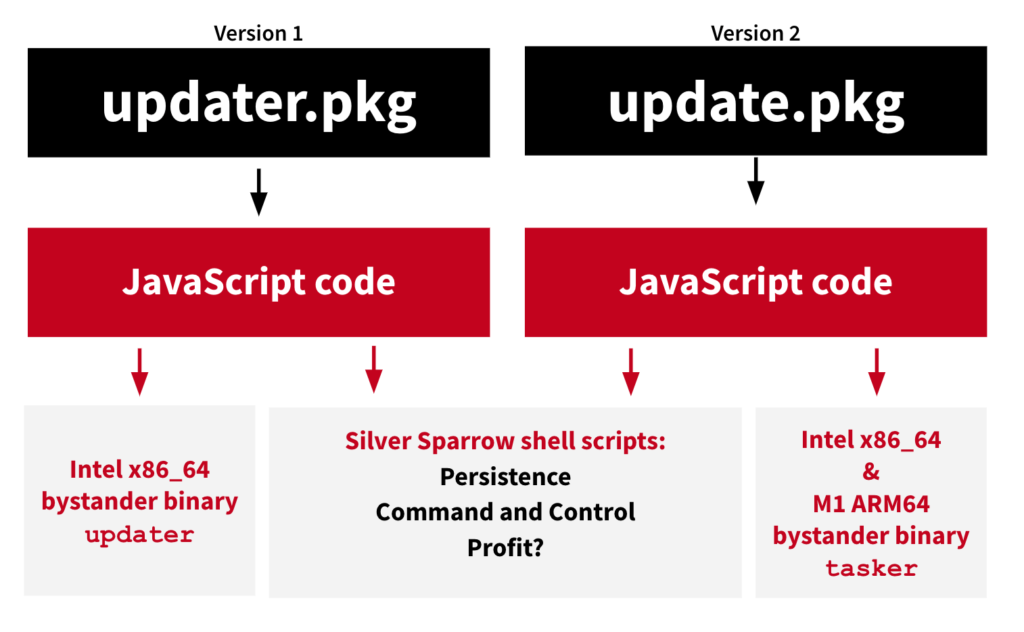
The malware abuses the macOS Installer JavaScript API to execute commands through the dynamic generation of two shell scripts that are written onto the target’s file system. The first script is responsible for confirming the initial infection with the C2, while the second runs periodically to fetch any additional modules or to receive command execution instructions. The malware also has the intrinsic ability to delete itself, which it hasn’t done yet.
Another mysterious feature of “Silver Sparrow” is a file check that removes all persistence mechanisms and scripts from the endpoint. This feature appears on some samples while it misses on others, and the researchers don’t have a clear picture of which circumstances trigger its appearance.
Finally, the distribution method remains unknown, too, although it is clear that the malware lands on the infected machines via PKG files. There’s a suspicion about a malicious search engine that directs users to download “Silver Sparrow” themselves, which would be masqueraded as an app or hidden in one. These are all assumptions at this point, though, and the questions remain more than the answers.
As for the notarization aspect, there’s no word about what certification underpins the installer and the binaries of the “Silver Sparrow,” but since users can bypass Gatekeeper’s warnings, that wouldn’t stop the infection from happening if the manual installation process is indeed how it’s done.
If you want to check your macOS for “Silver Sparrow,” here are the indicators of compromise as shared by Red Canary:
- Look for a process that appears to be PlistBuddy executing in conjunction with a command-line containing the following: LaunchAgents and RunAtLoad and true. This analytic helps us find multiple macOS malware families establishing LaunchAgent persistence.
- Look for a process that appears to be sqlite3 executing in conjunction with a command line that contains: LSQuarantine. This analytic helps us find multiple macOS malware families manipulating or searching metadata for downloaded files.
- Look for a process that appears to be curl executing in conjunction with a command line that contains: s3.amazonaws.com. This analytic helps us find multiple macOS malware families using S3 buckets for distribution.