SilentCryptoMiner Campaign Blackmails YouTubers to Spread Malware
- A novel blackmail-driven campaign distributes SilentCryptoMiner to YouTubers and their audience.
- The attackers threatened the content creators under the pretext of copyright infringement.
- The YouTubers were asked to post videos with malicious links or risk the shutdown of their channels.
Attackers capitalize on increased interest in Windows Packet Divert drivers to intercept and modify network traffic in Windows systems to disguise SilentCryptoMiner as a bypass tool. They coerce content creators to promote it under threats of penalties for the YouTube channel.
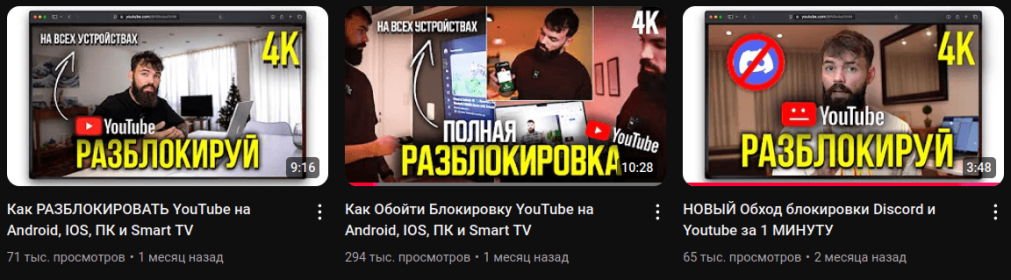
The attackers launch their campaigns with copyright strike claims against YouTubers who publish videos about bypassing restrictive blocks, especially using open-source tools deployed from platforms like GitHub, according to a detailed Kaspersky report.
The blackmail threat escalates as the attackers demand the creators upload videos with links to malicious downloads—or face the closure of their YouTube channels. By leveraging the credibility of content creators, they enhance the malware's reach and legitimacy.
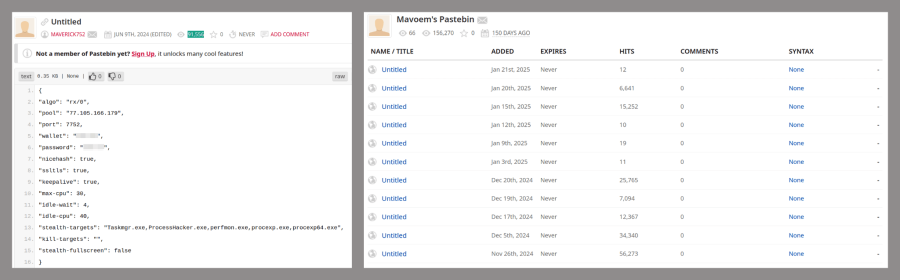
The SilentCryptoMiner malware masquerades as a tool to bypass internet restrictions but operates as a resource-draining cryptocurrency miner. The program hijacks computing power to mine cryptocurrencies, including Ethereum (ETH) and Monero (XMR), without the knowledge or consent of victims.
One YouTuber with 60,000 subscribers was coerced into promoting the infected tool in videos that collectively garnered over 400,000 views. Another prominent YouTube account with 340,000 subscribers was seen hosting a similar video tutorial, demonstrating the deceptive scale of this operation.
The malware is distributed through malicious archives hosted on compromised sites like “gitrok[.]com” and further promoted across Telegram groups and online communities.
Additionally, attackers urge victims to disable antivirus programs during installation, granting the malware unrestricted access to their systems.
Once active, SilentCryptoMiner employs several evasion tactics, such as using process hollowing to inject mining processes into legitimate system programs like dwm.exe and expanding the payload’s file size to hinder detection by antivirus solutions.
The malware allows attackers remote control through a web interface, allowing them to monitor and sustain their mining operations.
The malware campaign has reportedly affected over 2,000 victims in Russia. However, actual impact figures could be much higher, given the widespread use of bypass tools and the involvement of influential YouTube channels.
Recently, a Google flaw exposed the email addresses associated with several YouTube channels.