Free Decryptor Made Available for ShrinkLocker Ransomware Victims
- Targets of the BitLocker-based ShrinkLocker Ransomware can now enjoy a free decryptor made available by Bitdefender.
- The security company discovered a flaw in the old-school ransomware that uses VBScript and a built-in Windows feature for encryption.
- The significant ShrinkLocker bug causes execution failure during forced reboots, leaving the script inoperable post-reboot.
Bitdefender has released a free decryptor for victims of the ShrinkLocker ransomware, which utilizes Microsoft's BitLocker for encrypting files. This tool promises a lifeline to compromised entities, enabling data recovery by exploiting a vulnerability found immediately after the removal of BitLocker protectors.
The ransomware, a modified VBScript variant, targets Windows 10, 11, and server systems (2016, 2019). Despite its effectiveness, Bitdefender identified a significant bug causing execution failure—a "Privilege Not Held" error during forced reboots, leaving the script inoperable post-reboot. This flaw presents an opportunity for manual intervention to disrupt the attack.
Initially observed in May 2024 by Kaspersky, ShrinkLocker has been known for its novel approach of hijacking BitLocker—a native Windows utility—for encryption. This technique has been predominantly employed in attacks across Mexico, Indonesia, and Jordan, among other regions.
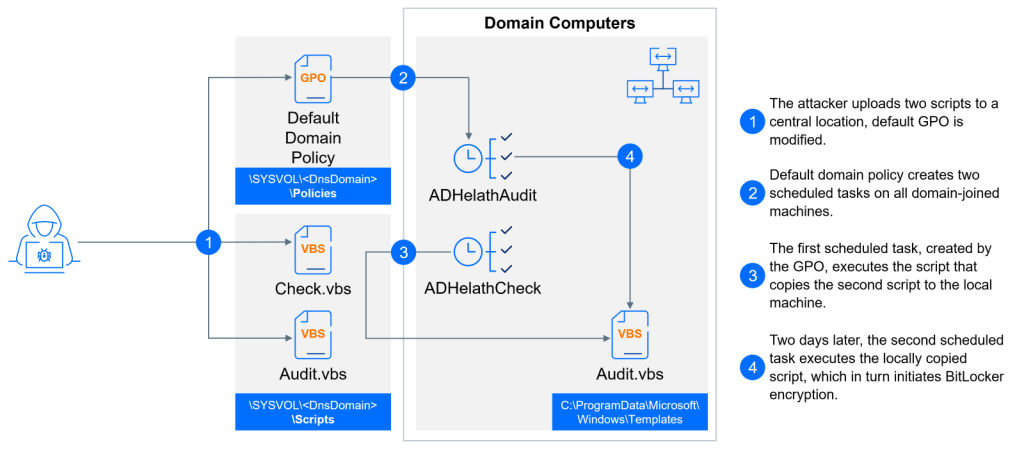
Bitdefender's decryptor emerges from an extensive analysis of ShrinkLocker's mechanics, especially following an attack on an undisclosed healthcare company in the Middle East.
The breach demonstrated a sophisticated exploitation of the supply chain, with threat actors using trusted contractor relationships to gain unauthorized network access. They successfully compromised systems through lateral movement using legitimate credentials, executing ransomware via scheduled tasks.
ShrinkLocker's deceptive naming misleads about its functionality, only shrinking partitions on legacy systems. Through Group Policy Objects and scheduled tasks, it risks rapid network-wide encryption. Proactive measures, such as monitoring Windows event logs and configuring BitLocker with AD DS storage policies, are crucial defenses against such threats.
Recently, Avast released a free decryptor for Mallox ransomware attacks occurring between 2023 and early 2024, and the FBI made available a free decryption key for LockBit victims.