“Shlayer” Remains the Most Common Malware Targeting macOS Systems
- macOS systems in the USA, Germany, France, and the UK remain big targets for the "Shlayer" Trojan.
- A new variant of the malware that first appeared in 2018 is written in Python instead of Bash.
- The main channel of distribution comes from websites that promise live soccer match feeds.
According to report data compiled by researchers at Kaspersky, the Shlayer Trojan remains the most common threat on the macOS platform, hitting 10% of the computers running Apple’s operating system, and accounting for 29.2% of all detections that concern it. Of course, the data derives from systems that have Kaspersky’s security solutions deployed, but it can be considered representative due to the large number of the specimens that were collected. More specifically, the Russian security expert has collected 32000 samples of Shlayer communicating with 143 C2 servers, since February 2018, which is when the particular Trojan first appeared.
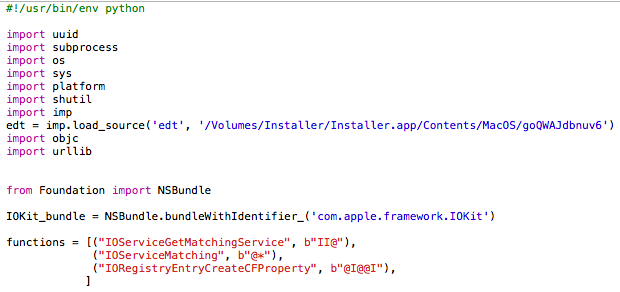
Although almost two years have passed since then, Shlayer has evolved very little and remains an ordinary piece of malware today. The only things that have changed since its humble beginnings are the infection method and the loader that is used by the actors. However, the researchers note that a recent variant (Trojan-Downloader.OSX.Shlayer.e) which is written in Python stands out from the crowd. It comes in the form of a DMG image and prompts the user to run the contained installation file once it’s mounted. If this action is approved, two Python scripts are executed. The first stage of the infection involves the system profiling and the fetching of an additional ZIP archive.
Source: Kaspersky Secure List
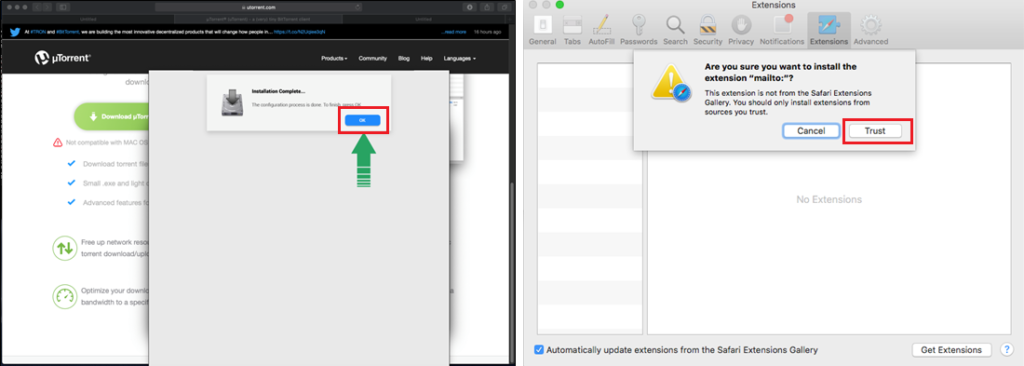
In the second stage, Shlayer is entering adware territory through “Cimpli”, planting a malicious extension in the Safari browser and popping a window right on top of the notification to hide the fact from the user. The extension monitors the user’s searches and tries to redirect the victim to a malicious domain. Moreover, a “mitmdump” tool with a trusted certificate is executed to help the actors see into HTTPS traffic as well. As a result, all user traffic passes through a proxy server, and the user hasn’t realized a thing.
Source: Kaspersky Secure List
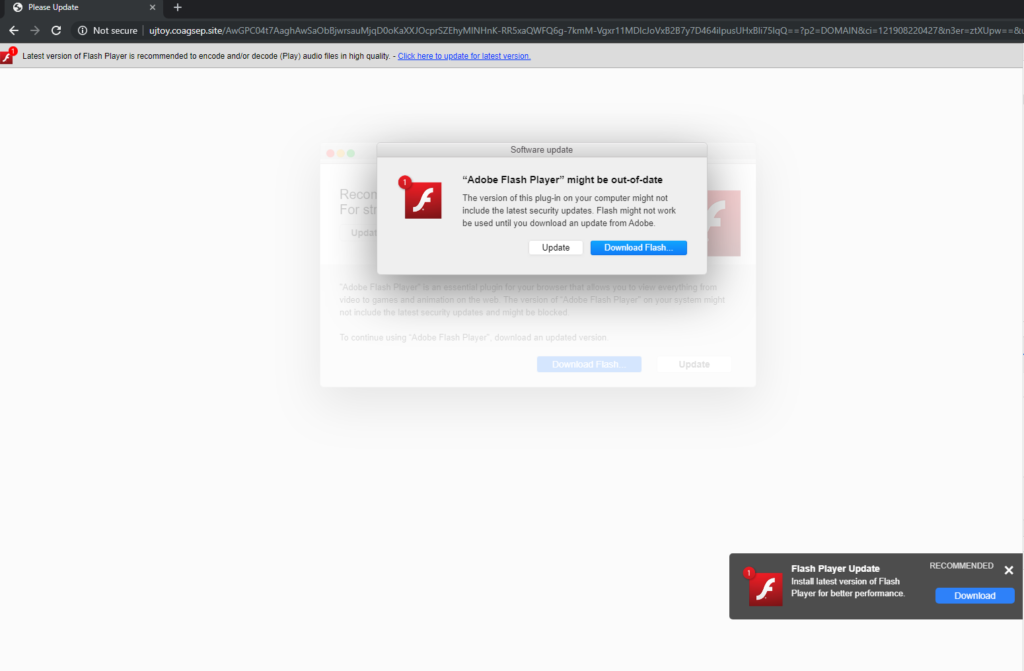
Of course, Shlayer isn’t devoting all of its payload-fetching capabilities solely to Cimpli. Other payloads that are currently used include Geonei, Bnodlero, and Pirrit. As for the distribution, right now, the actors are targeting people who want to access a live broadcast of a soccer match, or watch an episode from a popular series. The actors are promising precisely that by offering an update of “Adobe Flash Player” onto the victim’s browser.
Source: Kaspersky Secure List
In reality, this is nothing else than Shlayer, and agreeing to the Flash Player update is basically inviting the malware to your system. Right now, Shlayer enjoys a large network of distribution partners, who plant malicious pages on YouTube video comments and even on Wikipedia footnotes.