“Ripple20” Set of Flaws Is Sending Waves of Disturbance in IoT Security
- A set of 19 vulnerabilities named “Ripple20” is punching security holes in millions of IoT devices.
- The scope of the affection is extensive, and the complex supply chain is making the situation even worse.
- Six large vendors have confirmed their susceptibility, but the majority is still investigating.
The JSOF research lab has discovered a set of 19 vulnerabilities that they named “Ripple20”, and which affects a huge number of IoT devices deployed in a wide range of industries and applications. The flaws can potentially result in the hacking and takeover of the target devices, stealing of data, behavior change, settings change, planting of malicious code, and many more. The IoT vendors who are affected by “Ripple20” include Intel, Schneider Electric, HP, Rockwell Automation, Caterpillar, Baxter, and possibly many more that are yet to confirm it. The vulnerable devices are deployed in power networks, industrial systems, medical devices, networking, transportation services, home devices, retail, aviation, oil & gas, enterprise systems, and even the government and national security sectors.
The flaws are located in the “Treck IP” network stack software that is designed for deployment in various embedded systems. The Treck IP is plagued by 19 memory management bugs given the following identifiers. Severity scores only included for the highly critical flaws.
- CVE-2020-11896 – CVSSv3: 10
- CVE-2020-11897 – CVSSv3: 10
- CVE-2020-11898 – CVSSv3: 9.1
- CVE-2020-11899
- CVE-2020-11900 – CVSSv3: 8.2
- CVE-2020-11901 – CVSSv3: 9
- CVE-2020-11902
- CVE-2020-11903
- CVE-2020-11904
- CVE-2020-11905
- CVE-2020-11906
- CVE-2020-11907
- CVE-2020-11908
- CVE-2020-11909
- CVE-2020-11910
- CVE-2020-11911
- CVE-2020-11912
- CVE-2020-11913
- CVE-2020-11914
So, any device that uses an older version of the Treck IP software is vulnerable to arbitrary code execution, information disclosure, code planting, unauthenticated access, susceptibility to denial of service attacks, and remote code execution. Every flaw of the “Ripple20” set has been identified and addressed through a fixing patch, so the vendors are advised to upgrade to version 6.0.1.67 or later.
One of the main practical problems with the Treck IP library is that two unrelated firms manage separate branches of the software. Treck and Elmic Systems were once working together when the TCP/IP library first appeared in the market two decades ago. As the two split, the dissemination of the software followed separate paths, and the already complicated supply chain became even more tangly.
Downstream users cannot do much other than wait for the update to reach them. Until then, mitigation is your best bet, with the detection and blocking of anomalous IP traffic being a sure way to stay safe. Other than that, you may disable IP tunneling, block IP source routing, enforce TCP inspection, use OSI layer 2 equipment, disable IPv6 multicast, and reject IP fragments.
Source: JSOF
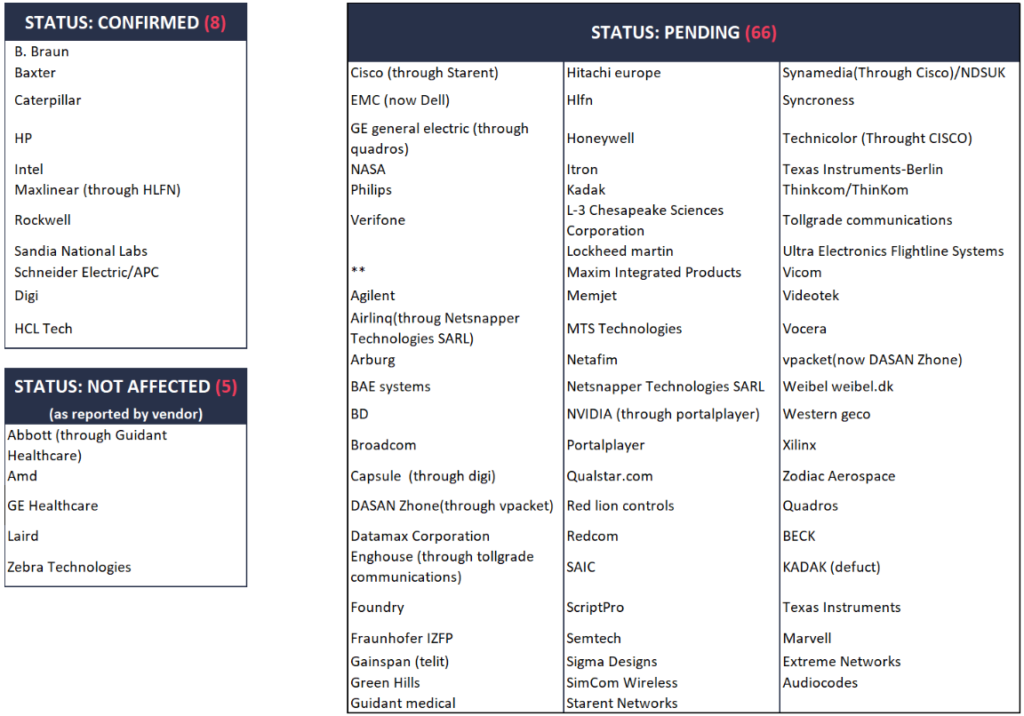
As shown in the above diagram, eight vendors have confirmed the vulnerability of their devices, five claim not to be affected, and 66 are still investigating. The majority of these vendors may be vulnerable to the “Ripple20” flaws, so if you’re using their devices, implement mitigatory measures now.